US banks and financial services companies are estimated to spend billions of dollars and millions of labor-hours each year on sanctions compliance. However, if you were the Chief Compliance Officer or Chief Marketing Officer at a major US bank, and you just found out that your company’s ads were serving on a website that was explicitly listed on the US Treasury’s Specially Designated Nationals (SDN) sanctions list, how would you feel?
On February 25th, 2022, a day after Russian armed forces invaded Ukraine, the Chairman of the US Senate Intelligence Committee, Senator Mark Warner, wrote a letter to Sundar Pichai, the CEO of Alphabet (Google’s parent company). Senator Warner said in his letter:
“I write to encourage your company to assume a heightened posture towards exploitation of your platform by Russia and Russian-linked entities. [...] Unfortunately, your platforms continue to be key vectors for malign actors – including, notably, those affiliated with the Russian government – to not only spread disinformation, but to profit from it. [..] Google even continues to serve ads for sanctioned influence actors like Southfront – a matter that I have separately referred to the Department of Treasury and Department of Justice for their attention. [..] Given the gravity of this situation, I would encourage you to, at a minimum, take immediate steps to: [...] Conduct an audit of Google and YouTube’s advertising business, including its compliance with sanctions”.
Despite the US Senate Intelligence Committee’s requests to Google, Google’s ad exchange appeared to, as recently as April 13th, 2022, serve digital ads on websites that were explicitly listed on the US Treasury’s Office of Foreign Assets Control (OFAC) sanctions list.
This research report will discuss several observations, including, among others, that:
- Google’s ad exchange appears to have been serving ads on websites which are explicitly mentioned in the Treasury OFAC SDN list – for at least 3 years
- Google’s ad exchange has been observing serving ads on possible Iranian, Syrian, Donetsk, and Crimean websites for at least 5 years
- Major U.S. brands that were observed running ads placed by Google on websites which may be under Treasury sanctions include: Citibank, HSBC, PayPal, Subaru, Charles Schwab, Refinitiv, GoDaddy, Zillow, Kayak, Zendesk, Facebook, Adidas, Norton, Alibaba, Banker's Compliance Consulting, Inc., Oxford University, and Yale University
- Major media agencies, including Interpublic Group (IPG), WPP, and Publicis Groupe, may have placed clients’ ads on websites which may be under sanctions
- Google’s own products have been advertised for months on a website that has been listed in the Treasury sanctions list since 2015
- All the potentially-sanctioned websites identified in this report use redacted, “confidential” (according to Google’s sellers.json declaration) accounts with Google. Those seller IDs are “mixed” with seemingly benign non-sanctioned websites
- Overall, an estimated 87% of Google’s ad inventory seller IDs in Russia are marked as “Confidential”
- Media buyers have reported that Google’s ad buying tools make it difficult to avoid “Confidential” seller IDs that may belong to sanctioned Russian entities
Important Note: Adalytics is just reporting what it has observed & cannot make any conclusions regarding the legality of any data it has observed and is reporting. For example, some of the entities mentioned in this research may well have obtained specific waivers, and/or licenses, from the US government to continue to run these ads despite sanctions.
Background - How do ads get on websites?
When you visit a website like wsj.com or nytimes.com, how do ads get served on those websites?
Digital advertising has a virtual “supply chain” of Supply Side Platforms (SSPs or ad exchanges) that work with publishers, and Demand Side Platforms (DSPs), which aggregate ad buying demand from media agencies and brands.
A publisher like Wall Street Journal (WSJ) or the New York Times (NYT) can apply for an account with an ad exchange, such as Google, Pubmatic, or Xandr. These ad exchanges collect ad slot inventory from different websites when consumers frequent those sites, and auction it off to the buyers.
Each publisher account gets assigned a unique ID by an ad exchange. You can see the NYT’s or Wall Street Journal’s ad exchange account IDs by visiting https://www.nytimes.com/ads.txt or https://www.wsj.com/ads.txt, respectively.
Advertisers who buy ads via DSP platforms, like The Trade Desk or Google Display & Video 360 (DV360), can purchase digital ads slots via their DSP and an ad exchange. For example, a media buyer working on behalf of Nike can use DV360 or Trade Desk to buy ad slots that were presented by Xandr or Google AdX on wsj.com.
 Source: Clearcode.cc (https://clearcode.cc/blog/what-is-supply-side-platform/)
Source: Clearcode.cc (https://clearcode.cc/blog/what-is-supply-side-platform/)This research will look into transparency issues with how some ad exchanges declare their ad inventory, and how some DSPs handle confidential ownership in the ad supply chain.
Ads serving on Russian military and intelligence operated websites
On April 15th, 2021, the US Department of the Treasury, acting on information provided by the Office of the Director of National Intelligence and Executive Orders signed by the US President, released a statement placing a number of Russian media outlets and websites on the US Department of Treasury Office of Foreign Assets Control (OFAC) Specially Designated Nationals And Blocked Persons (SDN) List.
The Treasury announcement had a section titled: “Treasury targets disinformation outlets controlled by Russian intelligence services,” which elaborated further that: “Russian Intelligence Services, namely the Federal Security Service (FSB), the Main Intelligence Directorate (GRU), and the Foreign Intelligence Service (SVR), play critical roles in propagating Russian disinformation online. The FSB, GRU, and SVR operate a network of websites that obscure their Russian origin to appeal to Western audiences. Outlets operated by Russian Intelligence Services focus on divisive issues in the United States.” The “FSB directly operates disinformation outlets. SouthFront is an online disinformation site registered in Russia that receives taskings from the FSB. It attempts to appeal to military enthusiasts, veterans, and conspiracy theorists, all while going to great lengths to hide its connections to Russian intelligence.”
The Treasury OFAC SDN list explicitly provided names and websites of the Russian intelligence operated websites. Even after the announcement of US sanctions against these sites, however, it appeared that ad exchanges, including the largest such as Google’s, continued to serve ads from Western brands for some time.
Some time after the Treasury Department’s explicit guidance, transparency activist group Check My Ads Institute and journalist Andrew Blustein from AdWeek reached out to Google for comment about these websites. The ads appeared to have been swiftly removed several hours later from the sanctioned Russian intelligence websites. However, one might ask the question - how long were ads being served on these Russian intelligence controlled websites? How long were the sites being monetized via ad exchanges?
For the Russian FSB-directed southfront.org, it appears that the website was serving ads via Google’s ad exchange since at least October 17th, 2018. The website was using Google seller ID ca-pub-8386451025337892 to serve the ads from Google’s ad exchange. There is no public information available on who owned or operated this specific Google seller ID. This seller ID was not even listed or observed in Google’s sellers.json manifest file since July 7th, 2020, despite being used to serve ads in 2020 and 2021.
The US Department of State issued a report in August 2020, explicitly stating that SouthFront was operated and directed by the Russian intelligence services. This suggests that for at least 8 months (early August 2020 to late April 2021), it is possible that Google’s ad exchange may have been serving ads on a site that was publicly known to be linked to the Russian FSB.
Ads serving on sanctioned US Treasury sanctioned websites
This section of the report documents observations of ads being served on sanctioned and likely-sanctioned websites.
A “sanctioned website” is a website that is explicitly and unambiguously defined on the Treasury OFAC SDN list.
A “likely-sanctioned” website is a website that is not directly or explicitly mentioned on the SDN list, but for other reasons, is possibly associated with a sanctioned entity. These are sites that are in various geographic regions where broad sanctions have been put in place by the US government, including North Korea, Iran, Crimea, Donetsk People’s Republic, and the Luhansk People’s Republic.
Adalytics posed the question “Is digital advertising exempt or subject to US Treasury sanctions?” to Stewart Baker, a lawyer who heads the homeland and cybersecurity practices at Steptoe & Johnson LLP. Baker was previously the General Counsel of the National Security Agency (NSA) and the Assistant Secretary for Policy at the Department of Homeland Security (DHS).
Baker responded: “US sanctions do not apply to informational materials, but they do apply to services. I’m pretty sure that the US Treasury would treat advertising on a Russian or Iranian website as a service that is barred by sanctions.”
Websites explicitly sanctioned on the Treasury OFAC SDN list
As mentioned, previously, the United States Treasury Office of Foreign Assets Control maintains a list of specific entities and individuals who are explicitly sanctioned. This list is known as the Specially Designated Nationals And Blocked Persons List (SDN). The SDN lists various identifiers and indicators to help compliance officers identify sanctioned entities. These sometimes include addresses, phone numbers, emails, or websites.
During the course of this study, Google’s ad exchange appeared to serve ads from several major Fortune 500 brands and many small businesses on websites that are explicitly and unambiguously listed on the SDN list.
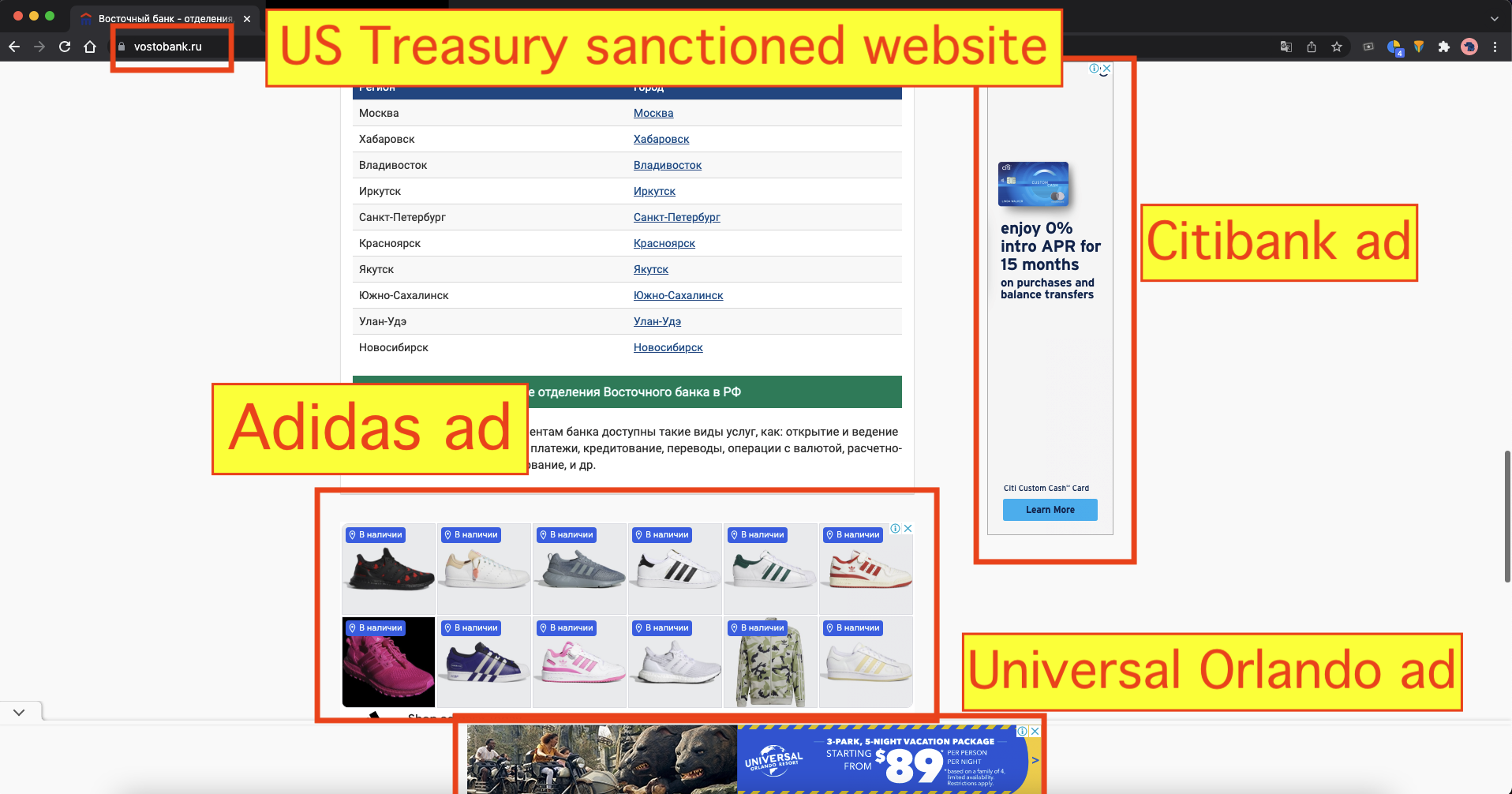
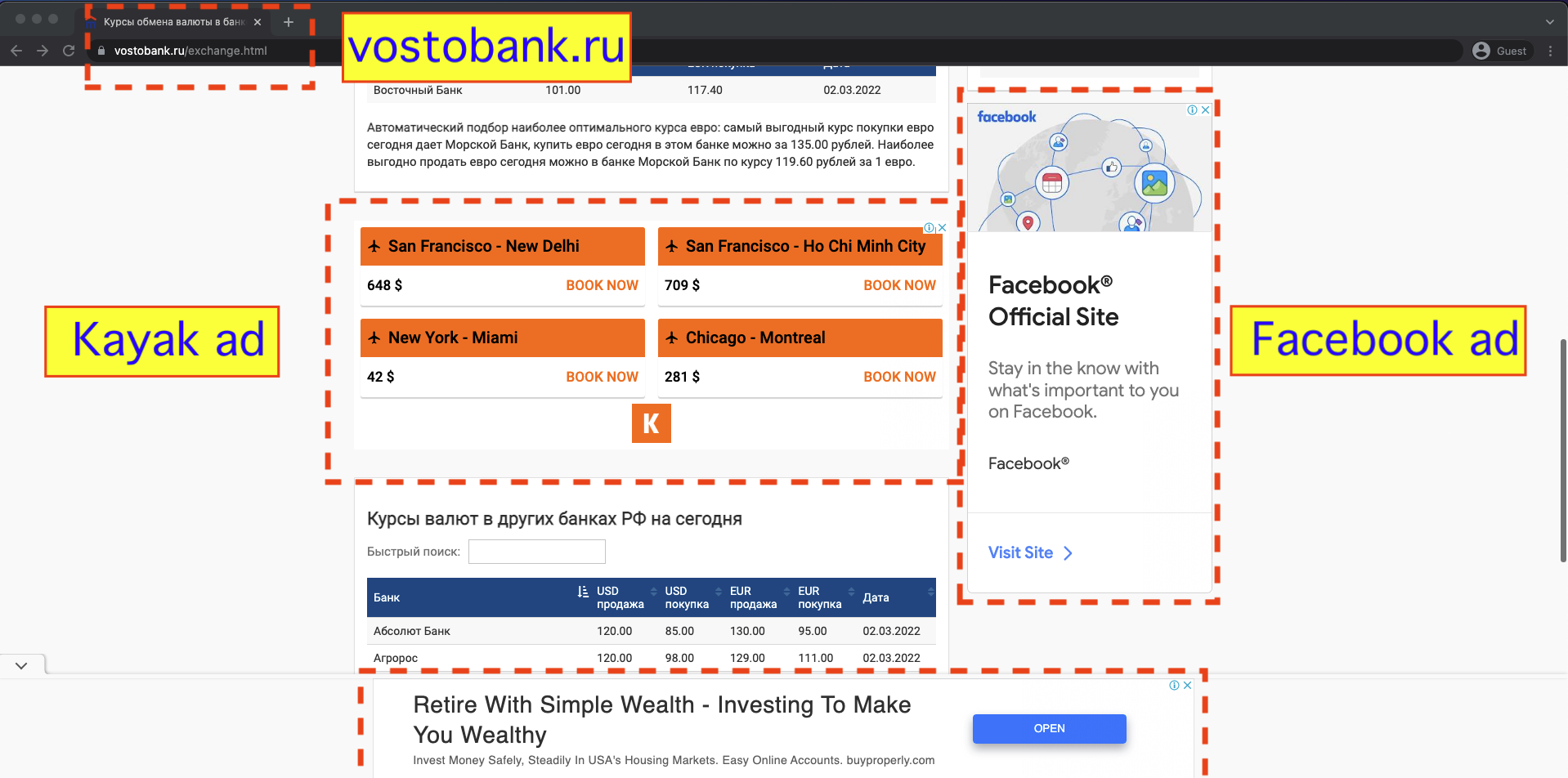
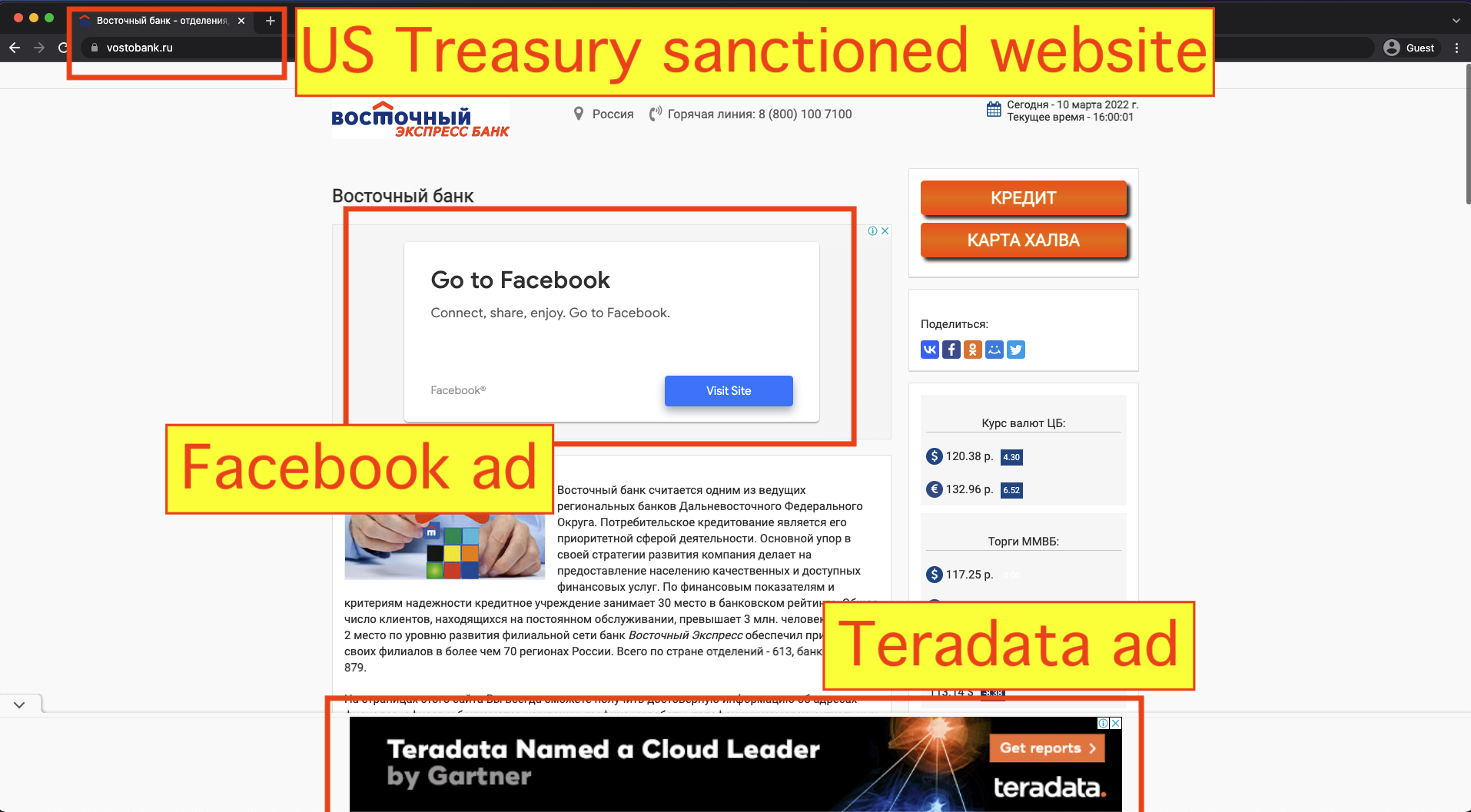
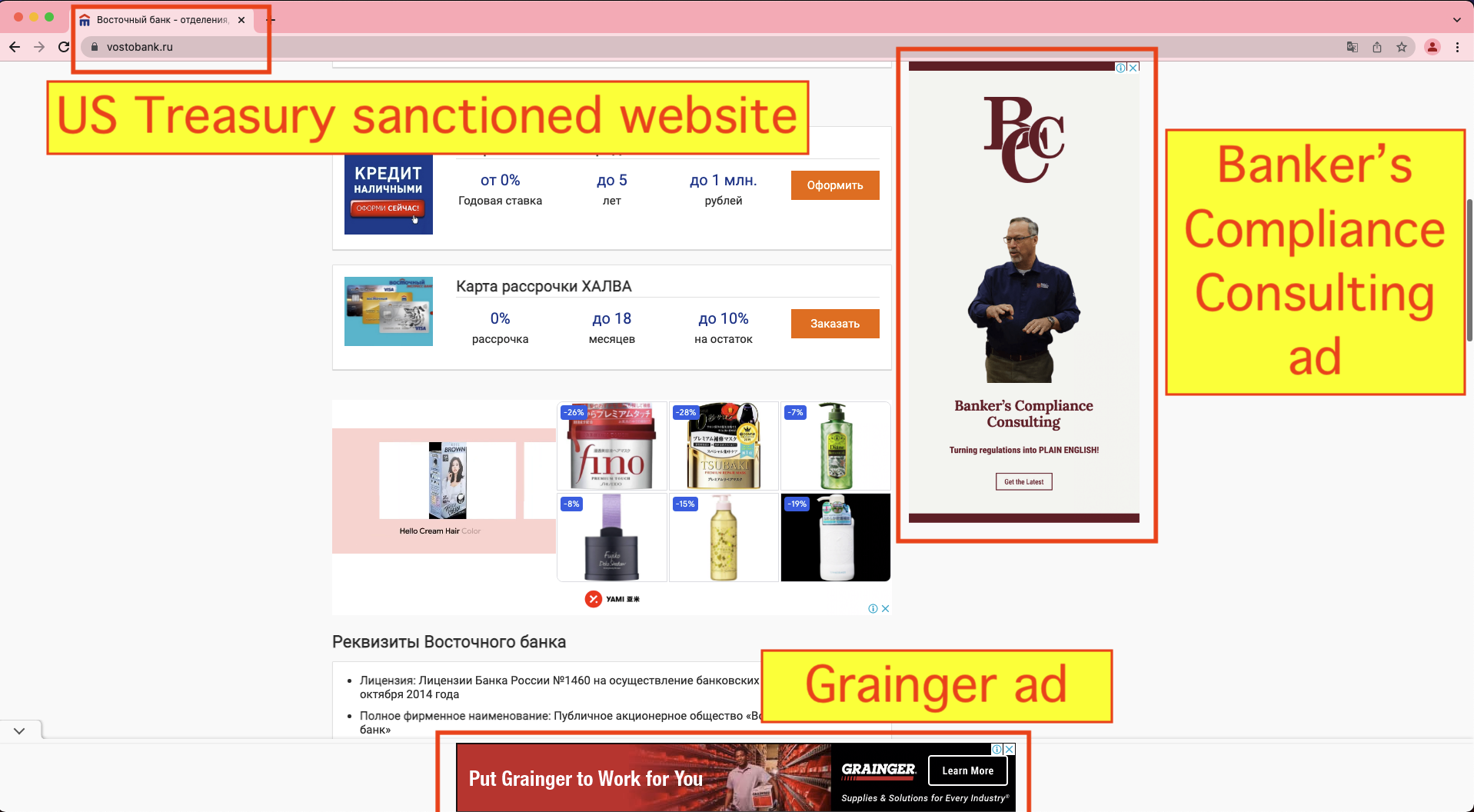
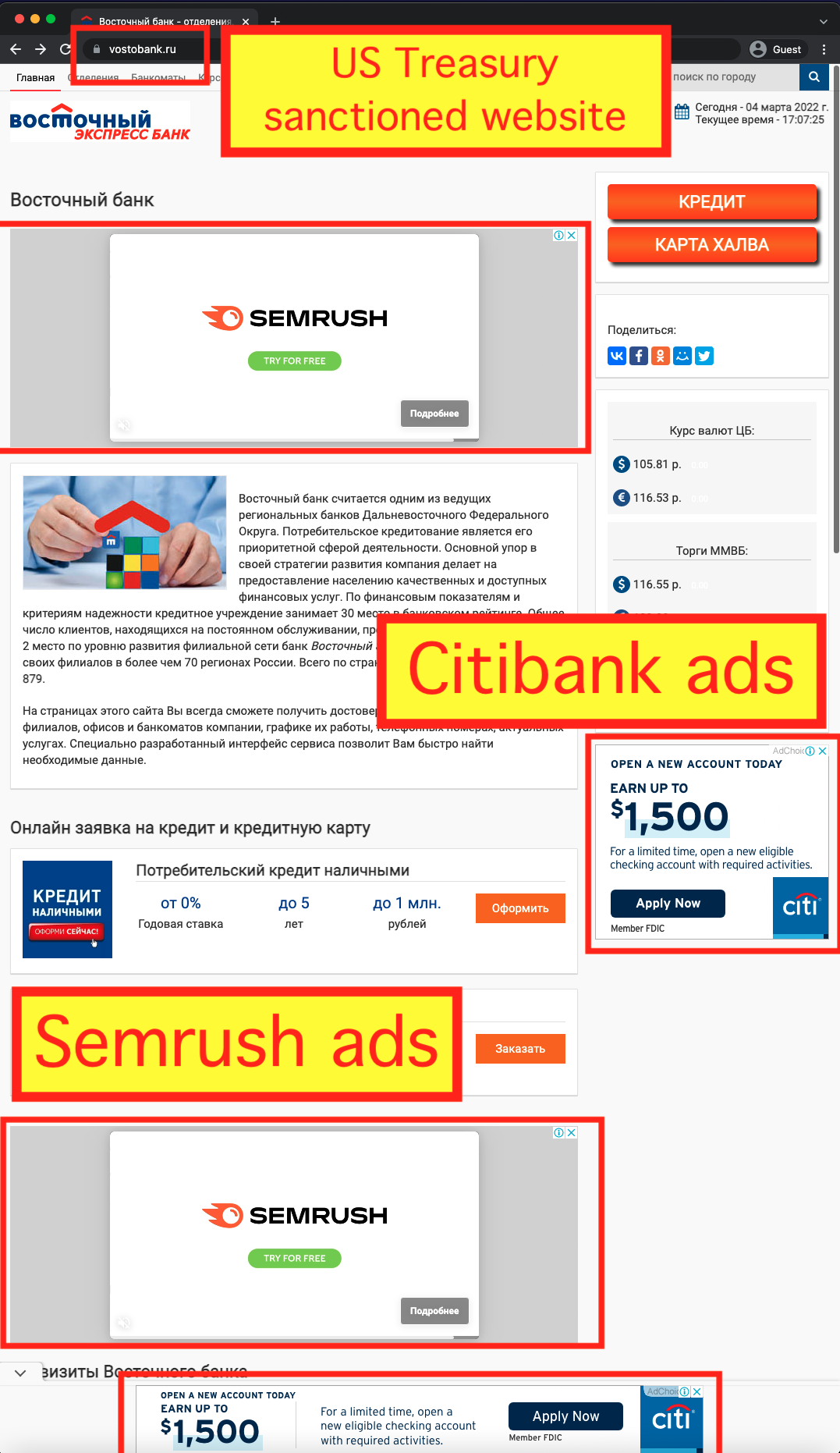
On February 24th, 2022, in response to the Russian invasion of Ukraine, OFAC placed Vostochny Bank, part of the Russian Sovcombank, on the SDN list. The SDN list mentions one of the websites operated by Vostochny Bank - vostobank.ru.
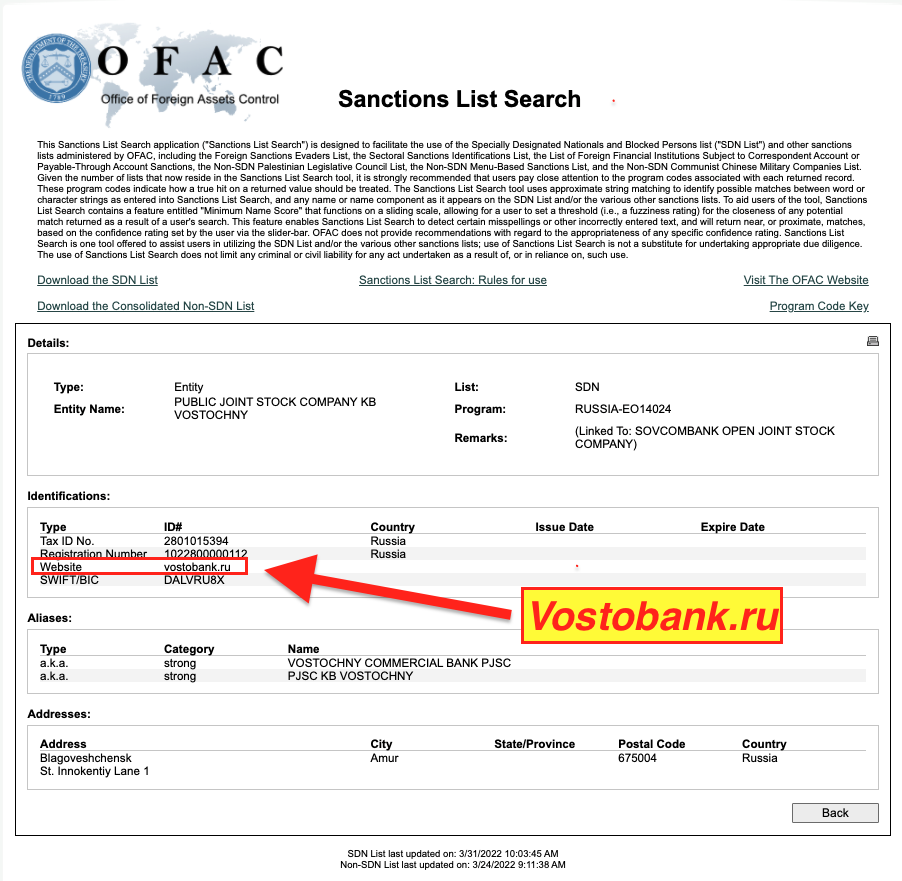
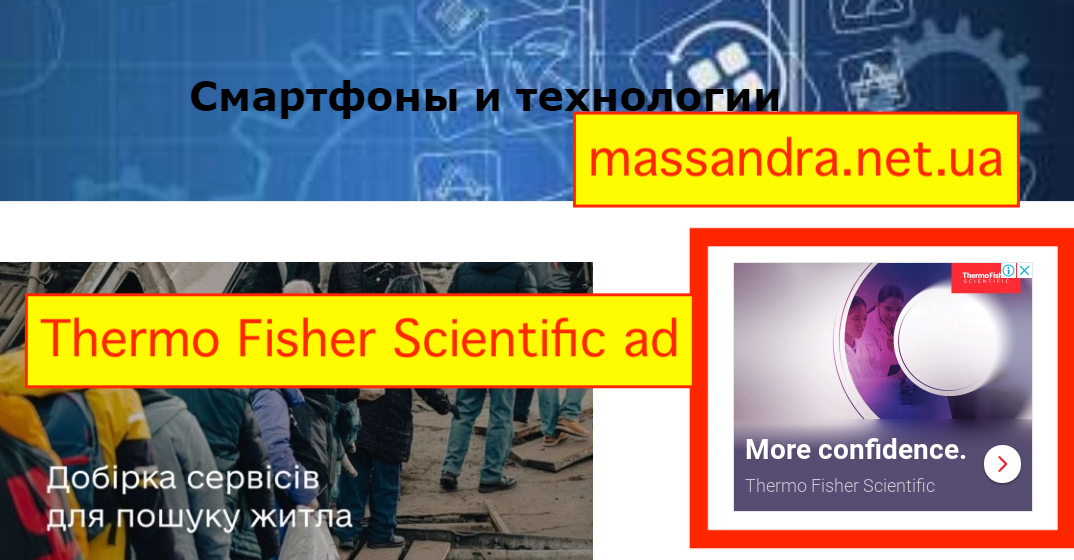
On December 28th, 2015, in response to the Russian annexation of Crimea, OFAC placed the “State Concern National Association of Producers Massandra” on the SDN list. This entity is based in the Crimean city of Yalta. OFAC explicitly lists the website of this sanctioned entity as massandra.net.ua.
Both of these websites were observed serving ads via Google ad exchange and ad buying tools after sanctions had been put in place.
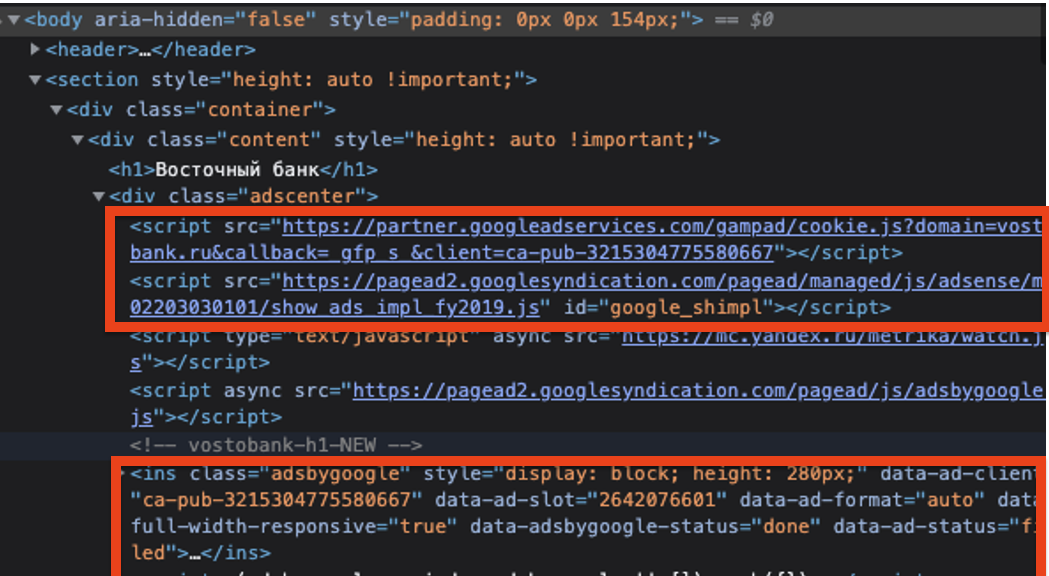
For vostobank.ru, the Google seller ID observed on the site was ca-pub-3215304775580667. This seller ID is marked as “Confidential” in Google’s sellers.json manifest file. The owner or operator of the seller ID is not publicly disclosed by Google. This specific seller ID was also observed in use on 13 other Russian websites, besides vostobank.ru.
Around March 20th, 2022, it appears that Google disabled ads from loading on vostobank.ru, possibly in response to outreach from various government entities. After March 20th, HTTPS requests to the endpoint “googleads.g.doubleclick.net/pagead/ad” return a 403 HTTP error status code on vostobank.ru.
However, even though Google may have disabled ads from loading on vostobank.ru, it appearsed (as of April 1st, 2022), that ads were still serving via the same confidential Google seller ID ca-pub-3215304775580667 on other websites. That suggests that the owner or operator of the seller ID which was originally found on vostobank.ru was still able to access and utilize Google’s ad services for some time.
Some of these websites which used confidential Google seller ID ca-pub-3215304775580667 and continue to serve ads for several weeks included:
- a-bank-adresa.ru
- vtb-adresa.ru
- mtcbank-adresa.ru
It is not clear why Google allows for confidential seller IDs to be re-used amongst different websites. However, this present situation suggests the possibility that the intermingling of sanctioned and non-sanctioned inventory via the same Google seller ID allows an OFAC sanctioned entity to continue to access Google’s products, even after the sanctioned website is taken down.
The other explicitly sanctioned website - massandra.net.ua - was added to the sanctioned entities list in 2015. Based on data provided by DeepSee.io, it appears that Google has been serving ads on massandra.net.ua since at least December 7th, 2020. This sanctioned website uses Google seller ID ca-pub-1546467778732436 to serve ads. The website does not have an ads.txt file.
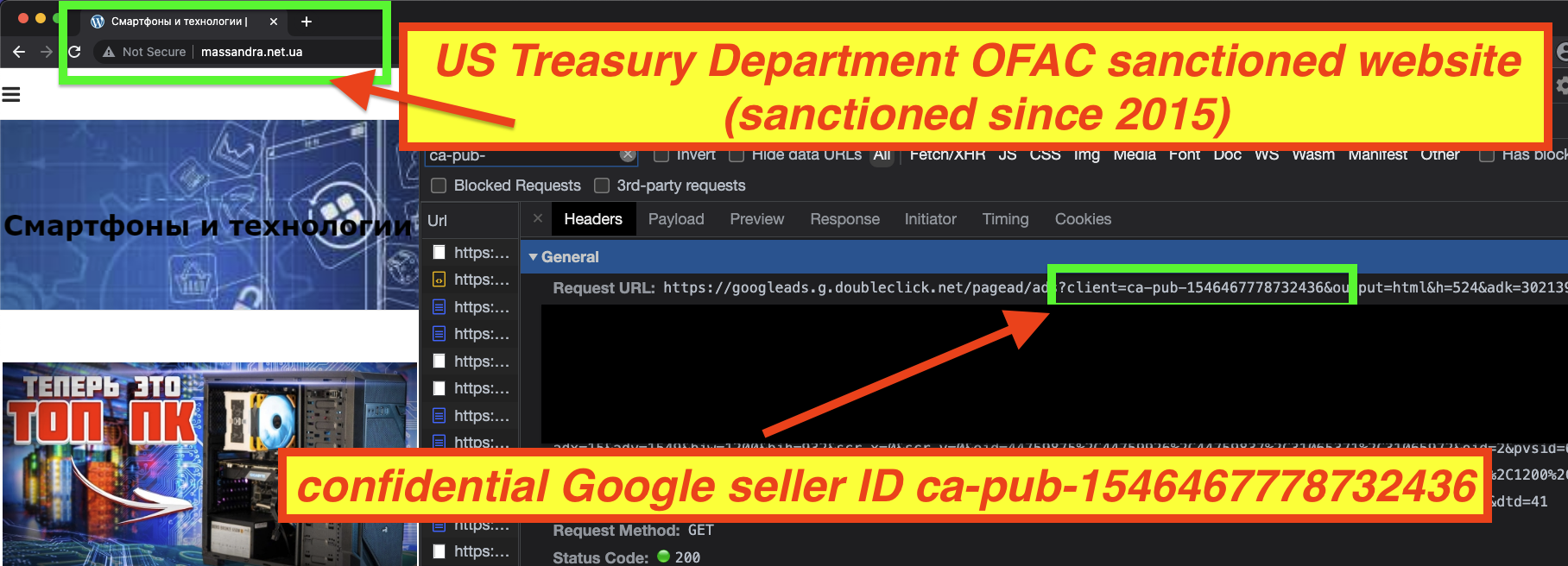
Who owns or operates Google seller ID ca-pub-1546467778732436? It is not clear, as Google’s sellers.json manifest file marks the ID as “confidential”.
However, it is interesting to note that this confidential seller ID is not used exclusively on the sanctioned website massandra.net.ua. The confidential seller ID was observed in use on 39 different websites. Some of those websites include:
- freeshared.ru
- ibizblog.ru
- nenadogryazi.ru
- likhnitsky.ru
- bonzone.ru
- donbassrus.dn.ua
- rassvet.dn.ua
The last two websites have a .dn.ua TLD, which is for the Donetsk region of Ukraine. Certain portions of the Donetsk Oblast have been under OFAC sanctions since 2015 due to Russian military action and because they have been incorporated into a separatist country called the “Donetsk People’s Republic” (DNR). Google’s own publisher policies state their products “are not available to publishers in” regions or countries including the “so-called Donetsk People’s Republic”. It is unclear if these last two websites are based or operated out of the DNR.
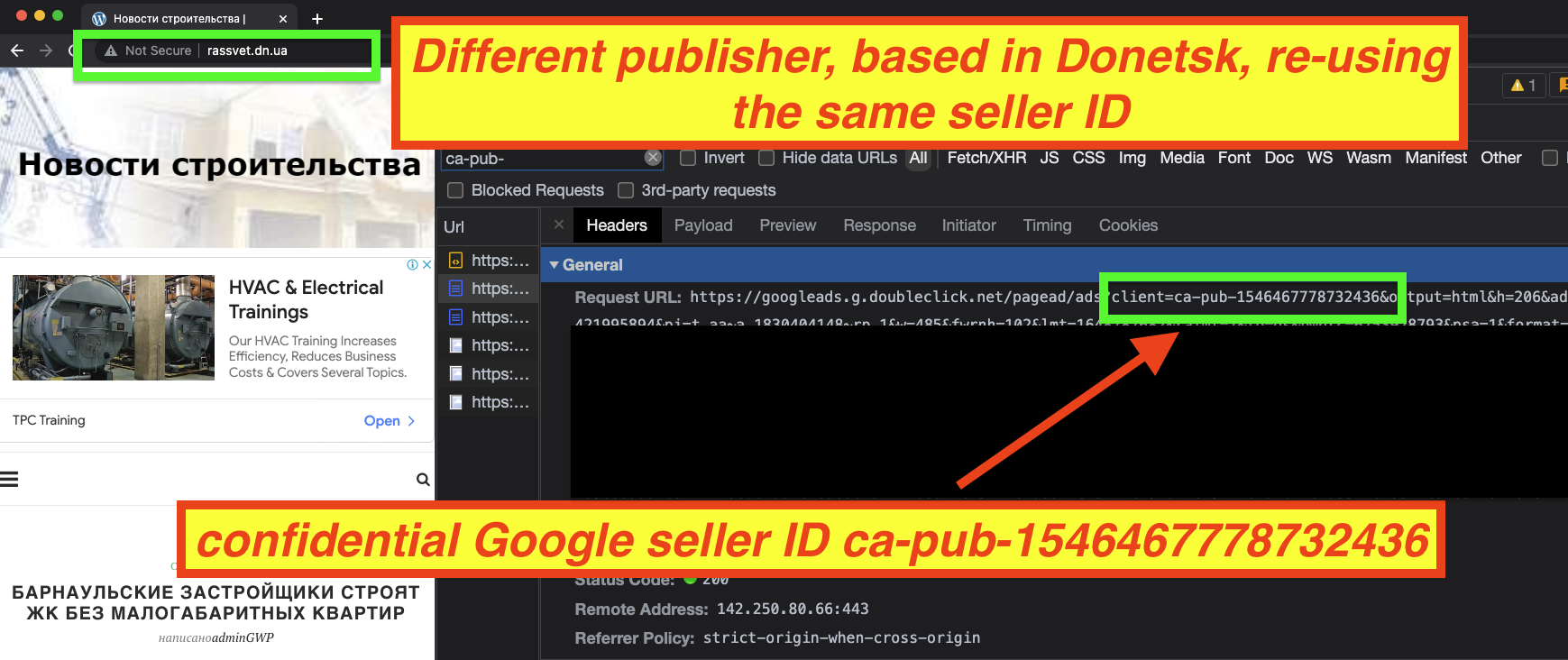
It is not clear why Google has allowed an explicitly sanctioned website to serve ads for several years. It is also not clear who is behind seller ID ca-pub-1546467778732436, or what their role is in the other 39 different websites that appear to use that same exact seller ID to serve ads. It is theoretically possible that the inter-mingling of 40 sanctioned and non-sanctioned websites via shared seller IDs allows the owners of some of those websites to bypass US government sanctions.
Many major brands and media agencies had their ads served on these two explicitly sanctioned websites via Google’s ad exchange and demand side platform (DSP). For example, travel platform Kayak and social media tech company Facebook both had their ads served multiple times on vostobank.ru. Facebook’s media agency of record is Publicis Groupe's Spark Foundry.
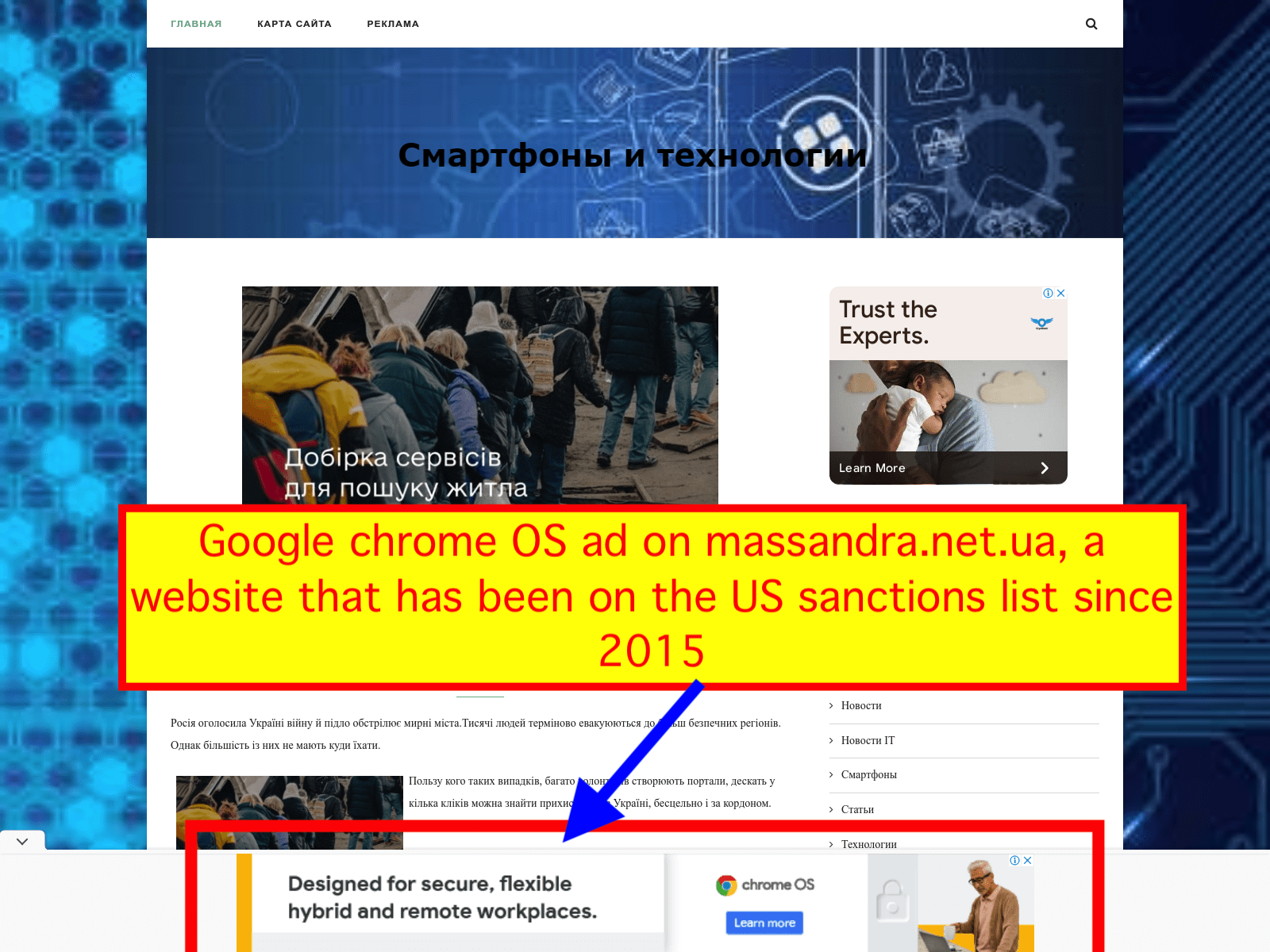
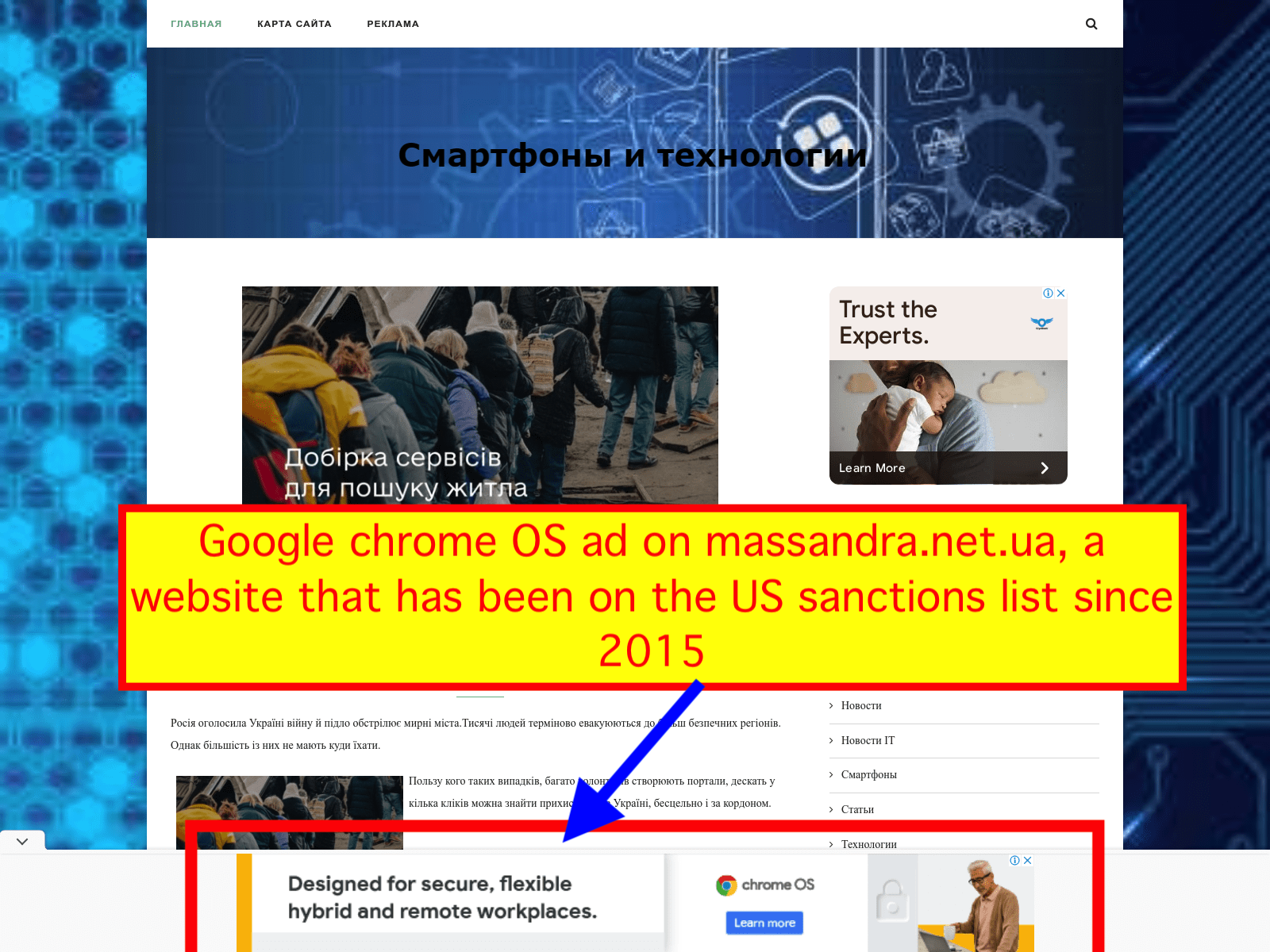
It appears that Google itself (or its media agency of record, WPP’s Essence) may have also been buying ads on the sanctioned massandra.net.ua website. Ads for Google’s Chrome operating system, a software package that helps enable hybrid workforces, were observed as recently as late March 2022 on a website that has been under US Treasury sanctions since 2015.
A latter section of this report will discuss the lists of brands, advertisers, and media agencies whose ads were observed serving on sanctioned websites such as these last two.
Websites in sanctioned regions serving ads
A number of websites observed serving ads via Google’s ad exchange are not individually mentioned by name on the Treasury OFAC SDN list. However, many of these websites appear to be hosted, headquartered, or listed in various geographic regions where there are broad sanctions in effect, such as Iran and Crimea.
According to one international law firm, countries like Iran and Syria are under “comprehensive sanctions”, which “prohibit most trade between the US and the target country.”
Google’s own Publisher Policies states that: “Google publisher products are not available to publishers in the following countries or territories: Crimea, Cuba, So-called Donetsk People's Republic (DNR) and Luhansk People's Republic (LNR), Iran, North Korea, Syria. Google publisher products also may not be used for or on behalf of a party located in the above listed sanctioned countries or regions.”
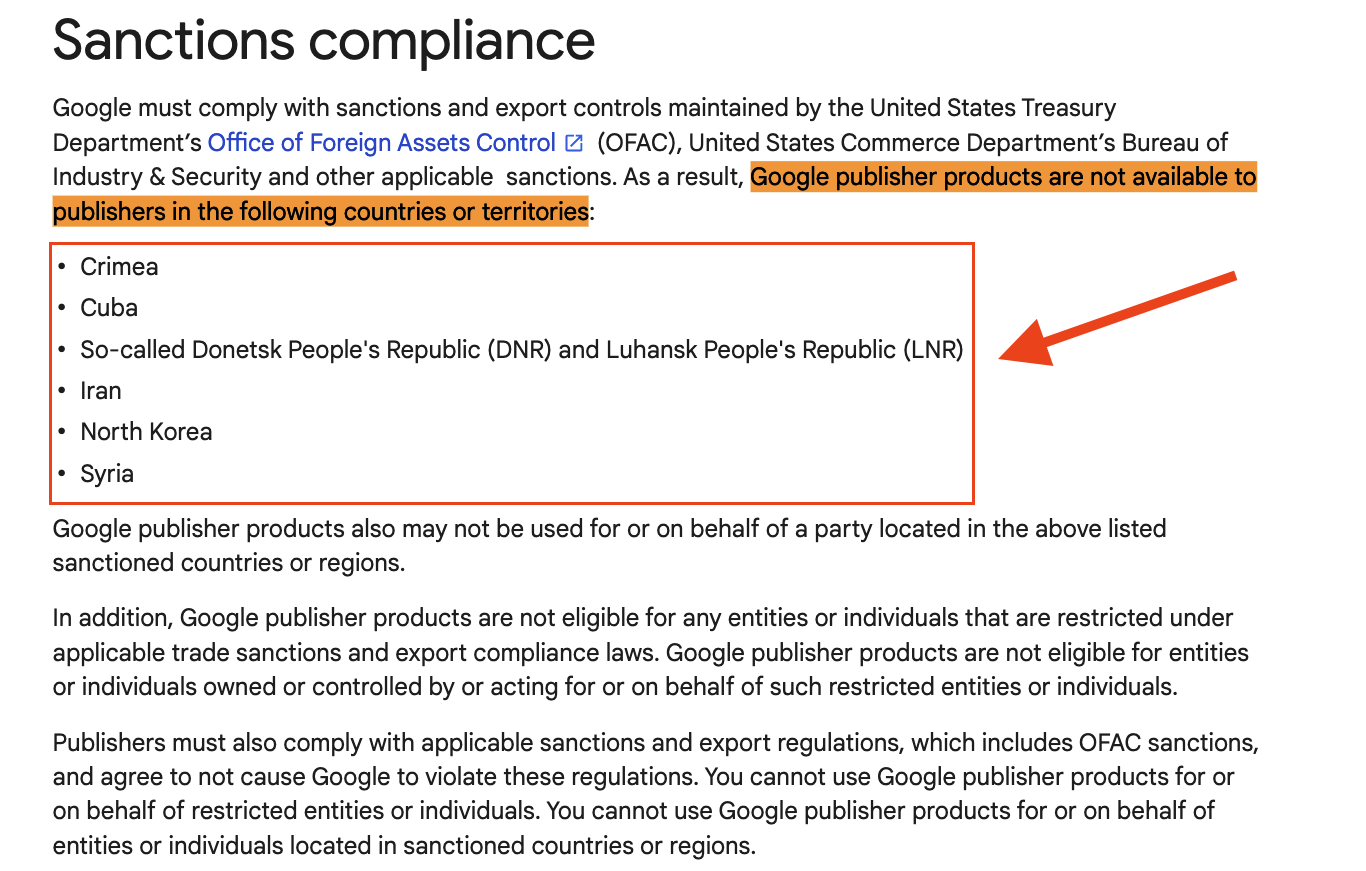
However, it appears that Google’s ad exchange has been serving ads, in some cases for years, on websites that appear to be linked or based out of Syria, Crimea, Donetsk, Luhansk, and Iran.
Iranian websites serving ads
The United States has imposed economic sanctions on Iran since 1979. Various levels of sanctions have been introduced in 1995, 2006, 2010, 2011, 2013, and 2018. In 2014, French bank BNP Paribas agreed to pay an $8.9 billion fine for violating US sanctions against Iran. In 2017, a Delaware based company paid a $1.2 million dollar fine to OFAC for exporting dental equipment and supplies to Iran.
The country code top-level domain (ccTLD) for Iranian websites is “.ir”. A number of websites with the .ir ccTLD were observed loading ads via “googleads.g.doubleclick.net/pagead/ads”, a Google owned domain. Based on data obtained from DeepSee.io, Google’s servers were observed serving ads on some of these Iranian domains since at least March 6th, 2021.
Examples of such sites (and the observed Google seller IDs), included:
- mammmmad[.]artanblog[.]ir
- Google ID ca-pub-3227144438472147
- Google ID ca-pub-3227144438472147
- mammmmad[.]avablog[.]ir
- Google ID ca-pub-3227144438472147
- compact-byn[.]atrinblog[.]ir
- Google ID ca-pub-639873936991074
- dezhar[.]partblog[.]ir
- Google ID ca-pub-4475538612939430
Each of these three Google seller IDs is marked as “Confidential” in Google’s Sellers.json index, so it is not immediately apparent who (if anyone) is being paid for the ads that load via Google ad exchange on these domains. None of these domains have ads.txt files on their websites.
A WHOIS record lookup or IP address enrichment confirms that the sites appear to be registered or hosted in Iran.
For example, for dezhar[.]partblog[.]ir, the domain host IP address is 82.99.244.238, which is located in Tehran, according to ipinfo.io.
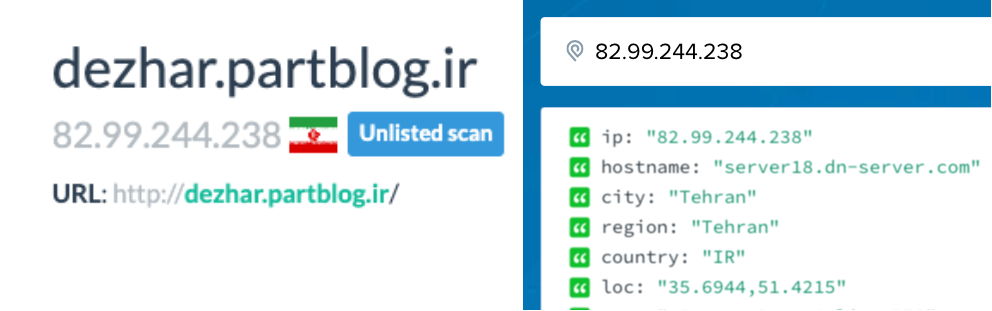
A WHOIS lookup of the domain confirms it is registered in Iran.
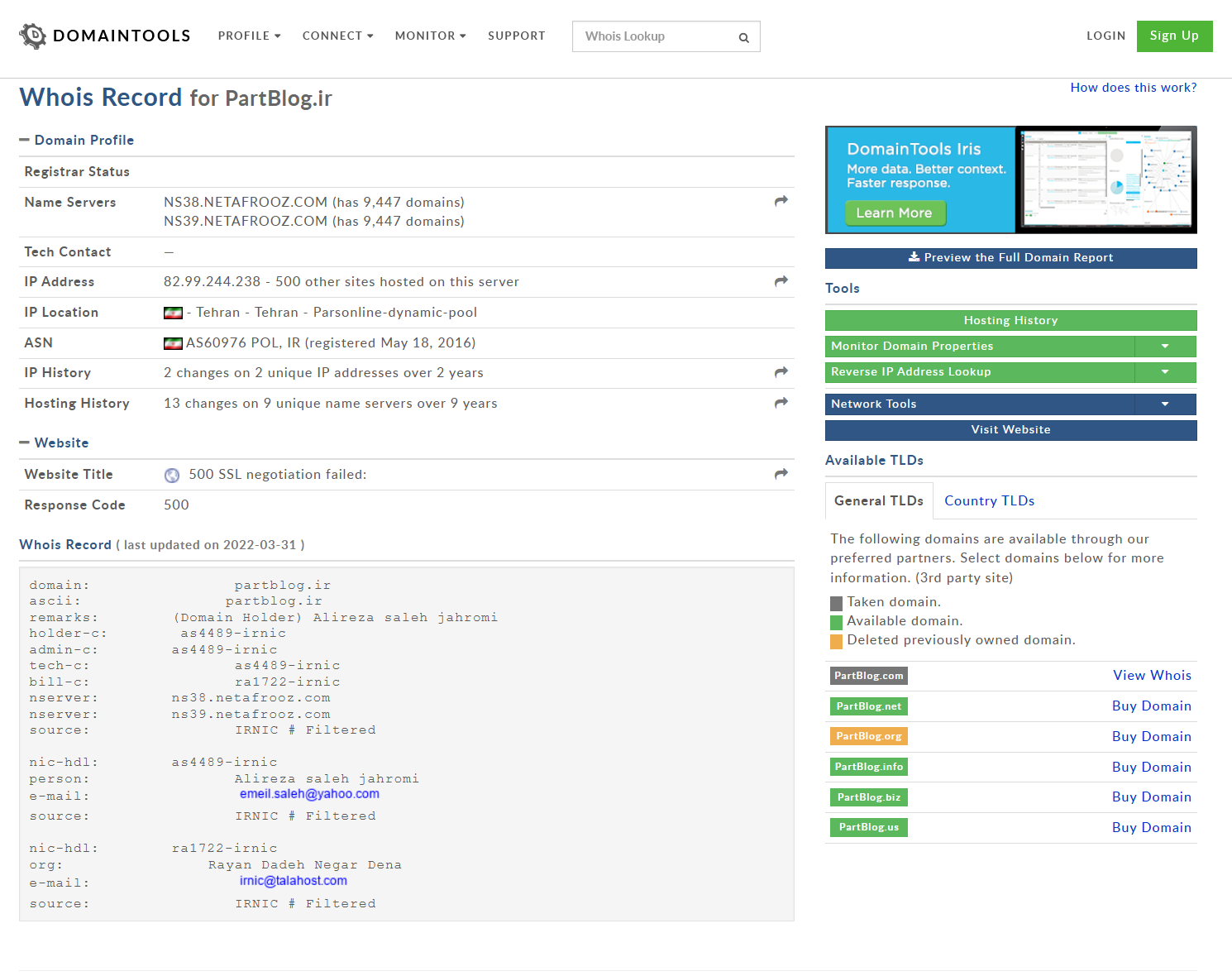 Source: whois.domaintools.com
Source: whois.domaintools.comCareful inspection of these websites shows that some of them appear to be using elaborate Javascript or CSS techniques to create hidden ads, including pop-unders or ads that are made invisible to the human eye through applications of style attributes. Google’s Ad placement policies generally prohibit pop-unders and “invisible” ads.
Google’s ad exchange was observed serving ads on these Iranian sites from dozens of small American businesses, as well as several large Fortune 500 brands, including:
- PayPal (via their joinhoney.com browser extension product)
- Twilio
- Ionos
- Alibaba
- Coldwell Banker Bain
- GoDaddy
- nationaldisastercompensation.com
- BistroMD
Several of these Confidential Google seller IDs are observed on other, non-Iranian websites. For example, seller ID from dezhar[.]partblog[.]ir (ca-pub-4475538612939430) was observed in use on architecturebeast.com on February 16th, 2022. It is not clear what relationship these two websites have (if any), beyond the fact that they share a confidential Google seller ID.
Somewhat interesting, some of these sites may be engaging in a phenomenon known as “domain spoofing”, where the publisher mis-specifies the page URL or domain that the user is on when the reader visits the website. This may give the media buyer faulty information as to where their ads are running on.
Syrian websites serving ads
The US government has imposed sanctions against Syria for several reasons - in 2011, some of these sanctions were strengthened as a result of the repression of civilians in the Syrian civil war. According to one legal commentary, “Syria is the target of broad country-based sanction regime like that of Iran and North Korea.”
Google’s publisher policies also state that their products are not available in Syra, and “may not be used for or on behalf of a party located in” a sanctioned region like Syria.
However, it is possible that some websites which were observed serving ads via Google’s ad exchange may be closely linked to Syria.
The country code top-level domain (ccTLD) for Syrian websites is “.sy”. The domain syrianow.sy redirects automatically to syrianownews.com. The “About Us” page of this website says it is editorialized by “A group of media professionals and corresponds in Damasus and the Syrian governorates.”
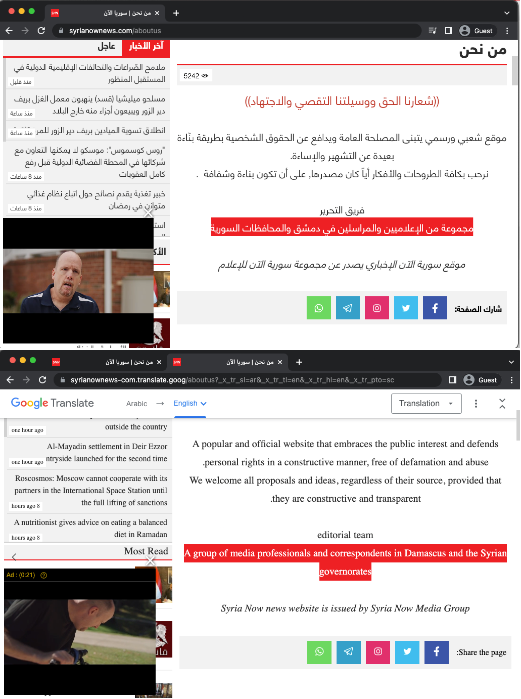
This website was observed serving ads using Google seller ID ca-pub-1500203688393627. It is not clear who owns or gets paid through this seller ID, as it is marked as confidential in Google’s sellers.json manifest file.
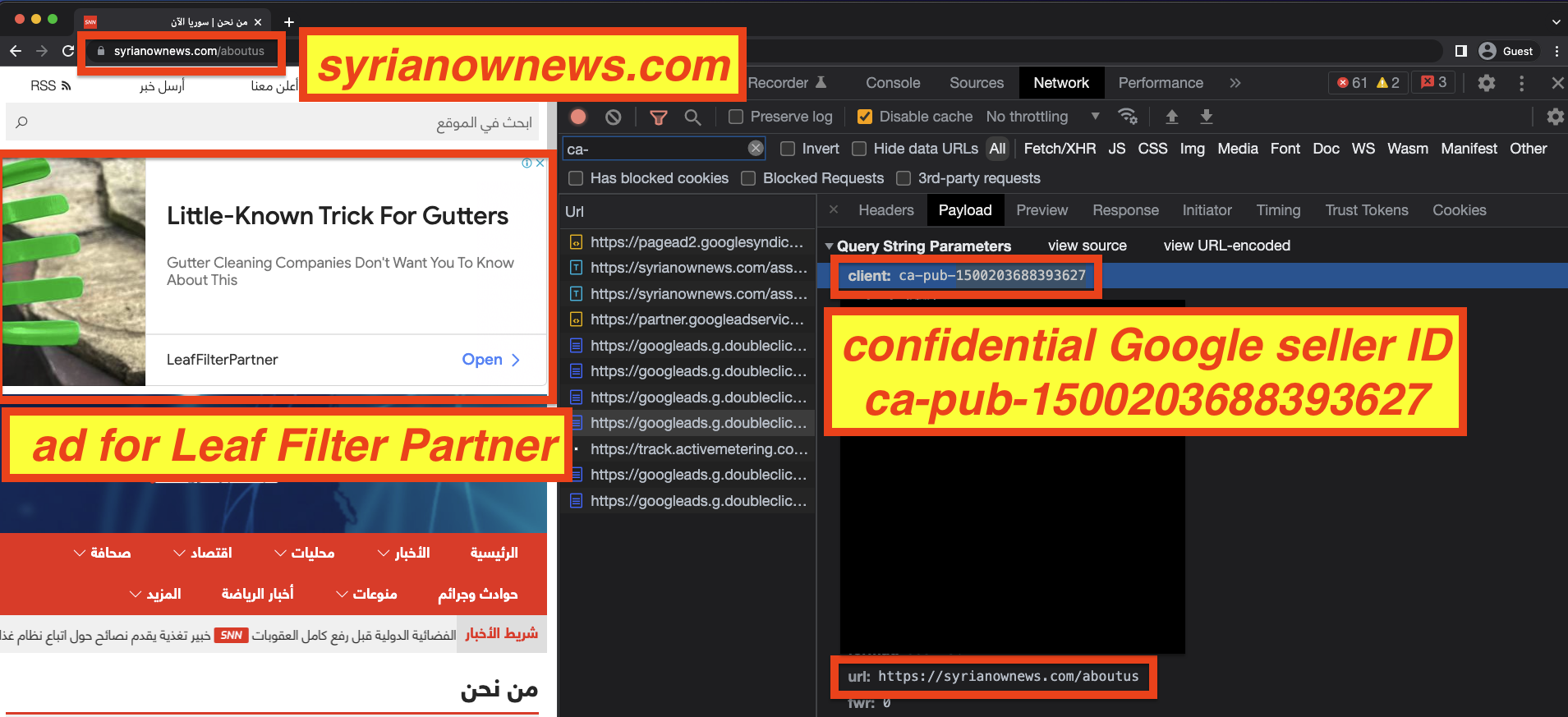
Ads from several major brands, including Dunkin Donuts, Facebook, Alibaba, University of Miami Health System, Oregon Community Credit Union, and Boston-based home security company Simplisafe, were observing loading on syrianownews.com.
Donetsk & Luhansk People's Republic websites serving ads
The US government has imposed “comprehensive sanctions” on the so-called Donetsk People’s Republic (“DNR”) and Luhansk People’s Republic (“LNR”) regions of eastern Ukraine. A compliance commentary states that: “it is now prohibited for US Persons to export, reexport, sell, or supply, directly or indirectly, any goods, services, or technology to the Covered Regions.”
Google’s own publisher policies state their products “are not available to publishers in” regions or countries including the “So-called Donetsk People's Republic (DNR) and Luhansk People's Republic (LNR)”.
However, there are a number of websites that may be linked to or based out of the DNR and LNR which have been observed serving digital ads via Google’s ad exchange.
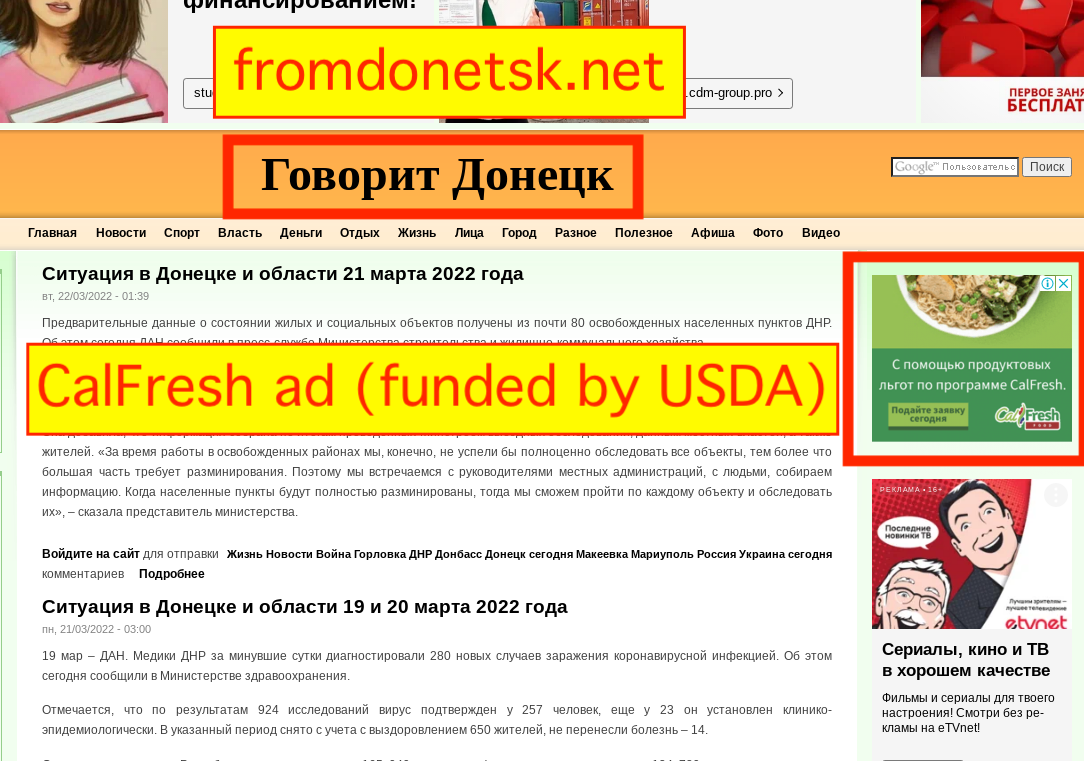
For example, the website fromdonetsk.net includes a number of local news and information from the city of Donetsk. The website discusses the “liberation” of 80 cities in the DNR by Russian armed forces, and describes the Ukraine military as “invaders”. The website’s Twitter account says it is based out of the city of Donetsk, the capital of the DNR.
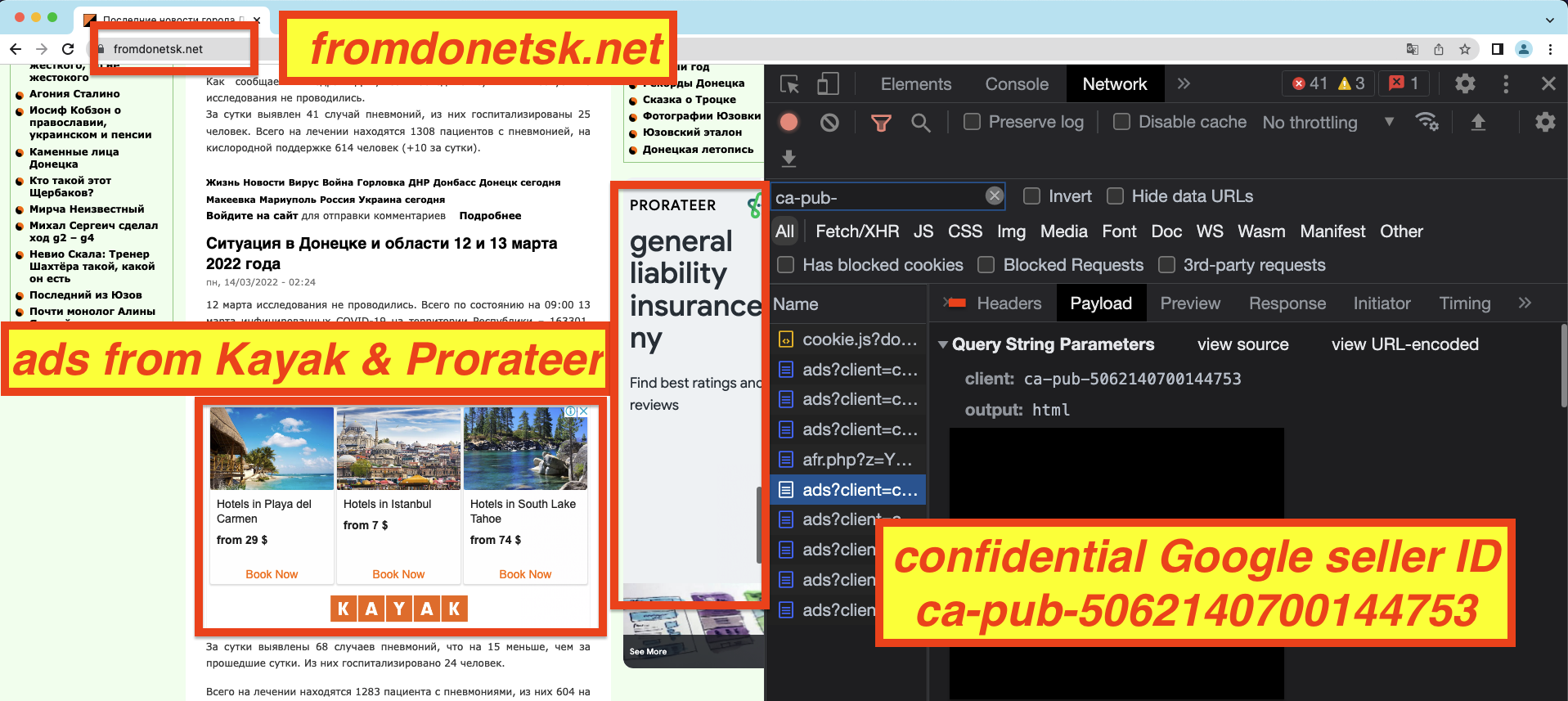
Google’s ad exchange was serving ads for a number of American and European advertisers via Google seller ID ca-pub-5062140700144753. It is not clear who owns or is paid for ads that run through this seller ID, as Google’s sellers.json manifest marks this seller ID as confidential.
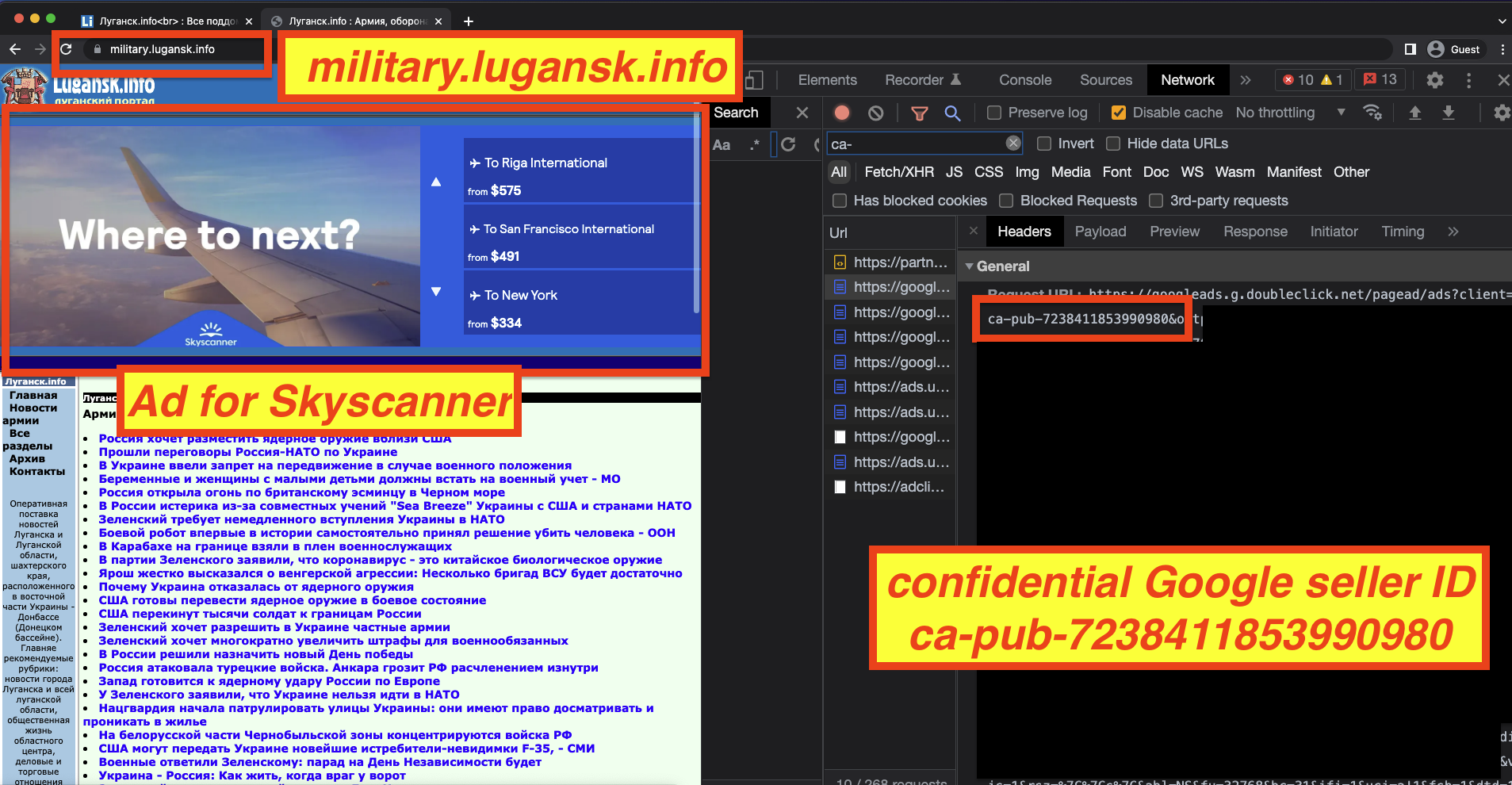
Ads from major brands such as Kayak, Ebay, the California state government, and the US Department of Agriculture (via their Supplemental Nutrition Assistance Program) were observed on fromdonetsk.net. The website military.lugansk.info, whose contact details say it is based in “Lugansk, Donbas, Ukraine”, was observing serving as from brands such as Skyscanner and BistroMD via Google seller ID ca-pub-7238411853990980. The seller ID is marked as confidential in Google’s sellers.json file, so it is not immediately clear who is being paid for the ads that run on this website.
Crimean websites serving ads
According to one legal commentary, “On December 19, 2014 the United States imposed fairly comprehensive, “country-based” sanctions on the Crimea region of Ukraine.” The legal commentary explains, “The Crimea region of Ukraine is subject to comprehensive, “country” based sanctions. This is true even though Crimea is not a country. The region is being targeted for sanctions that are similar in scope and construction to those targeting Iran, Sudan, Syria, and North Korea.”
Google’s publisher policies also state that their products are not available in Crimea, and “may not be used for or on behalf of a party located in” a sanctioned region like Crimea.
However, several websites which may be linked to Crimea appear to have been serving ads via Google’s ad exchange.
For example, news.allcrimea.net, a news and business site covering topics in various Crimean cities like Sevastopol, was observed serving ads from brands such as Kayak via Google seller ID ca-pub-6461300772818991.
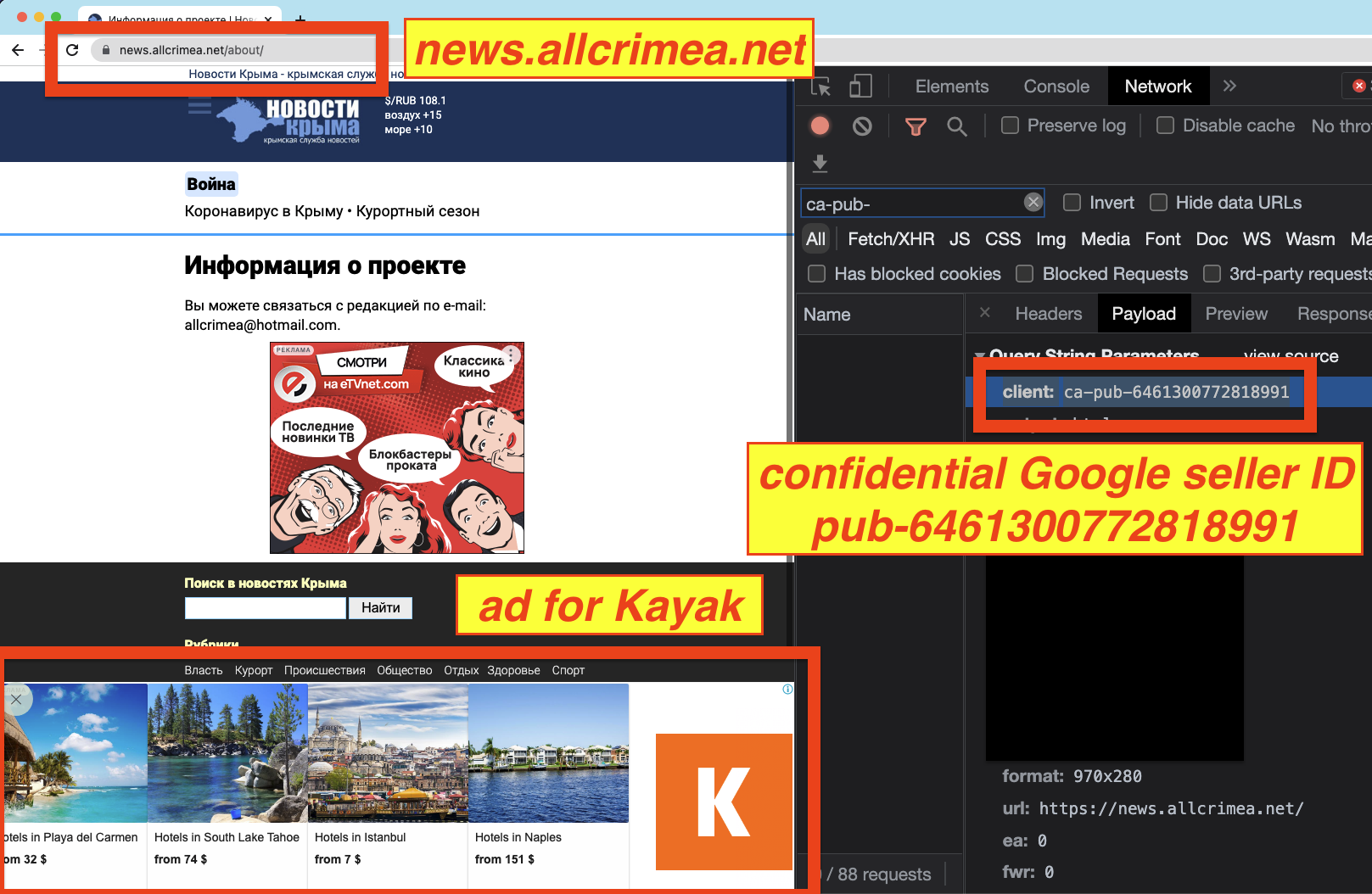
Another website which includes tourism, business, and news information for Crimea is crimea-media.ru. This site was also observed serving ads, via Google seller ID pub-7054553415728119. The ownership of this ID is not clear, as it is marked as confidential in Google’s sellers.json manifest file.
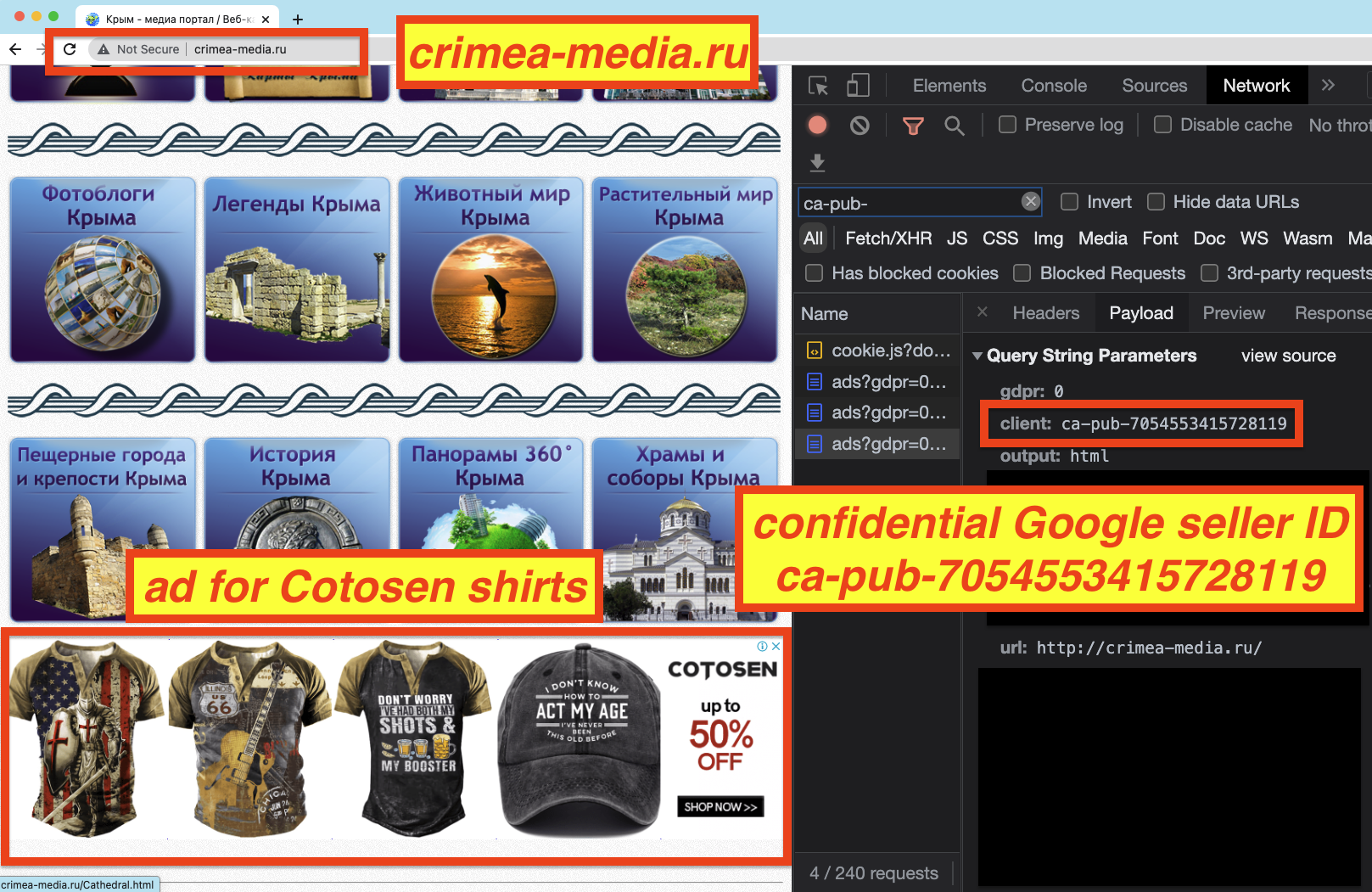
Some other websites which were observed serving ads, and which may possibly have links to Crimea (based on the content they serve, IP address, WHOIS information, or physical office address) include:
- ekomissionka.crimea.ua
- Google ID ca-pub-3227144438472147
- koktebel.ecrimea.ru
- Google ID ca-pub-9729040712826300
- crimea-media.ru
- Google ID ca-pub-7054553415728119
- crimeamap.ru
- Google ID ca-pub-9729040712826300
- crimeasearch.com
- Google ID ca-pub-2909196838435833
- uavto.crimea.ua
- Google ID ca-pub-2053143612831793
- vsesdelki.crimea.ua
- Google ID ca-pub-6098931991541959
- autocrimea.net
- Google ID ca-pub-2342310453462883
All of these Google seller IDs are marked as confidential in Google’s sellers.json file, so it is unclear who owns or operates them. Furthermore, some of these seller IDs are re-used on other websites - for some example, seller ID ca-pub-2053143612831793 was observed in use on 19 other websites besides uavto.crimea.ua.
Ads from many major brands and organizations were observed loading on these potentially Crimea related websites, including those of Facebook, Bestbuy, Kayak, Alibaba, Oculus (owned by Facebook), and Mercy College in New York. The media agencies of record for some of these brands include Publicis Groupe’s Spark Foundry and IPG’s UM.
Google’s ad inventory is highly redacted and non-transparent
Many ad exchanges allow media buyers to know from whom they are buying ad inventory. This transparency gives advertisers some degree of transparency into whom they are working with and funding via their ad budgets.
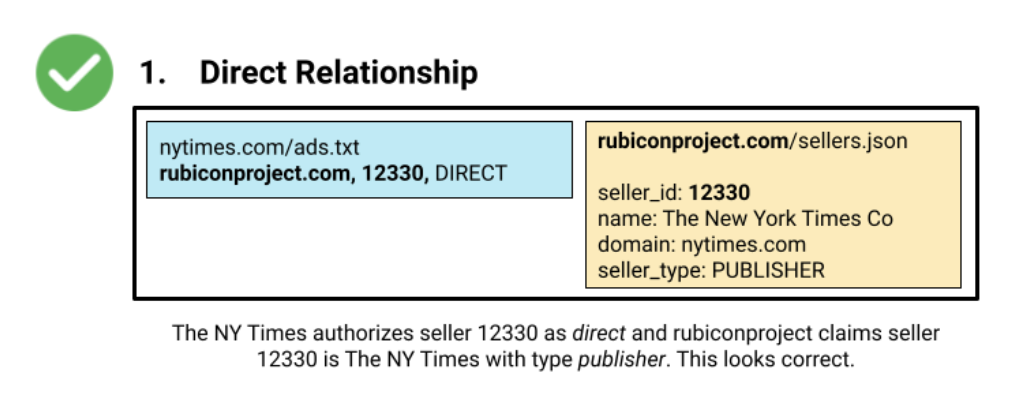
The Interactive Advertising Bureau (IAB), a trade group representing the world’s largest publishers, advertisers, and ad tech firms, released the Sellers.json standard in 2019. This standard requires ad exchanges to post publicly accessible text files on their websites which allow humans and automated crawlers to verify which websites are authorized to sell ad slots via a given exchange’s seller IDs.The Sellers.json of each ad exchange conveys the seller ID, the name of the corporate entity or business behind the seller ID, and the website of that business. For example, the screenshot below includes what a seller ID for the New York Times would look like, for the ad exchange Rubicon Project (now known as Magnite). The Rubicon Project Sellers.json file makes it immediately clear who the owner of seller ID 12330 is - The New York Time Co. With this information, an advertiser buying ads via Rubicon Project seller ID 12330 can quickly understand that their ad spend is funding The New York Times.
However, unlike many other ad exchanges, Google’s Sellers.json file does not indicate the media organization or business behind many of the Google seller IDs. In the (re-arranged) screenshot below from March 6th, 2022, one can see examples of many Google seller IDs that are marked as “is_confidential: 1”. For these Google publisher accounts, it is not immediately apparent who is being funded via an advertiser’s media buy. It is also not immediately apparent which websites are using or operating with that given Google seller ID.
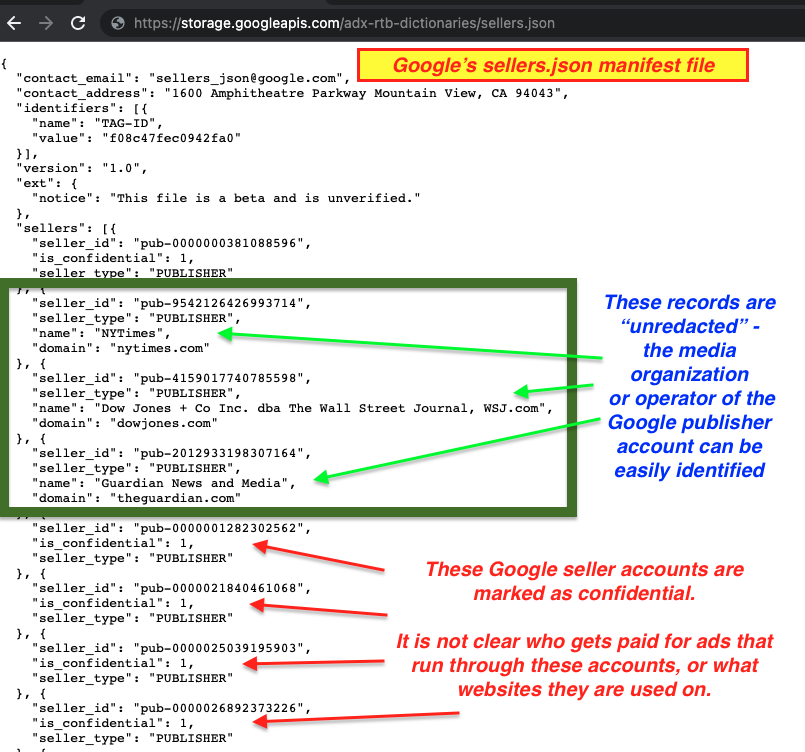
As mentioned in previous sections, for all the sanctioned, Iranian, Syrian, and Crimean websites identified in this study that were serving ads, each website used a Google seller ID which was marked as “confidential” in Google’s Sellers.json file. This means that Google does not include the entity that is paid for ads that serve on those websites, nor does Google disclose all the websites which use said seller ID. Many of the seller IDs observed in use on sanctioned websites were also observed in use on dozens of other, un-related websites.
Because the identity and ownership of these seller IDs is marked as “confidential” in Google’s sellers.json file, it is generally very difficult if not impossible for an advertiser to ascertain who is being funded by ads that run through these Google seller IDs.
Google seller IDs have been observed in use on over 1.9 million different websites in the last ~90 days. The actual number of publisher websites that Google serves ads on is likely higher. In those last ~90 days, at least 643,275 different Google seller IDs were observed in use on those different websites. Many IDs are re-used between different websites.
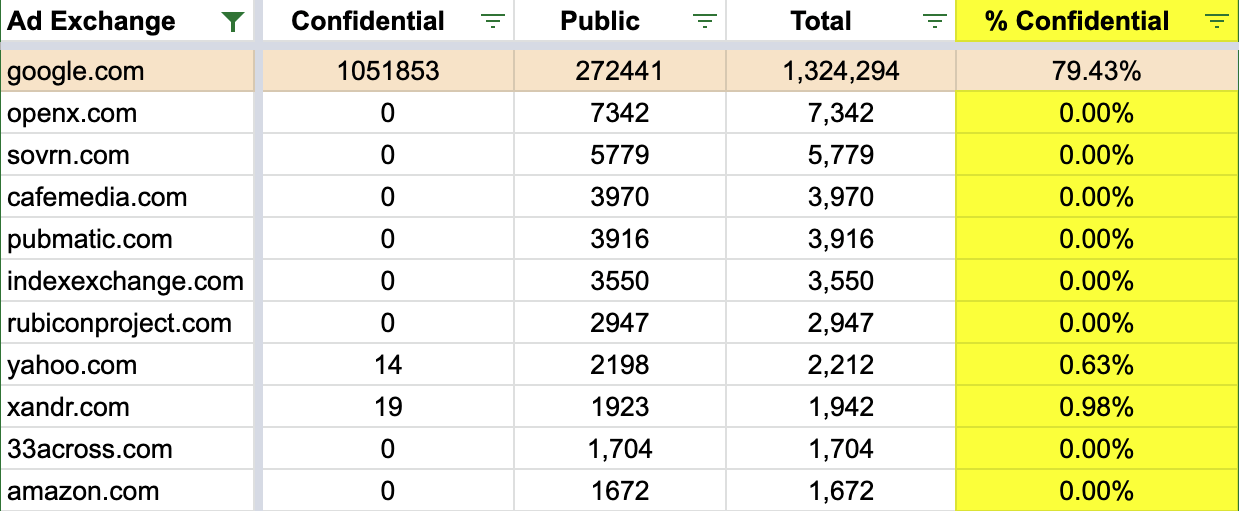
However, unlike other major Western ad exchanges, Google’s sellers.json is relatively unique in that it is the only one for which the vast majority of seller IDs do not include a company name or a publisher website domain. Google’s sellers.json contained 1,313,878 different seller ID records at one point in Q1 2022.
Based on data from ad tech researcher Braedon Vickers and well-known.dev, it appears that 79.35% of the records listed in Google’s sellers.json are marked as confidential. For these 1,042,624 Google seller IDs, it is not immediately apparent which business or entity gets paid when ads are served via that seller ID. As mentioned previously, many of the sanctioned websites observed serving ads via Google’s ad exchange appeared to be utilizing confidential Google seller IDs.
According to one ad tech industry professional, approximately 9% of all programmatic ad traffic is “confidential”.
One might reasonably ask - how does Google’s Sellers.json file compare to those of other major American ad exchanges? Do other ad exchanges, such as those of Amazon, also mark a large percentage of their seller ID records as confidential?
Alas, the answer appears to be “no”. No other major American ad exchange appears to have as many confidential seller IDs.
This differs markedly from other major American ad exchanges. For both Yahoo and Amazon’s ad exchanges, more than 99.3% of all seller IDs listed in their respective Sellers.json files enumerate the business owner and/or the domain that is using a given seller ID. For most other American ad exchanges, 100% of all their seller ID records contain this transparency information about the owner or operator of a given seller ID.
Why does Google allow for so many seller IDs to be marked as confidential in Google’s sellers.json file? Google’s documentation on “Identifying sellers through Sellers.json” states that Google supports both business and individual accounts. “Some publishers have individual accounts registered with their personal name and may want to remain confidential so as to protect their privacy.”

However, many large media organizations and business websites were observed using confidential seller IDs.
Trustpilot.com, a popular international consumer review website whose corporate owner is listed on the London stock exchange, was observed using confidential Google seller ID ca-pub-0509843775112688. Mashable.com, a New York based international media organization, was observed using confidential Google seller ID ca-pub-7281102704644151.
India.com, “the flagship website of ZEE Digital” media corporation and one of the highest traffic websites in India, was observed using confidential Google seller IDs ca-pub-7469782653477415 and ca-pub-2037142780490943.
smithsonianmag.com, a website operated by the Smithsonian Institution, which manages the National Air & Space Museum, National Museum of American History, National Museum of Natural History, and many other educational institutions in Washington DC, was observed using confidential Google seller ID ca-pub-953213130915538.
Liveinternet.ru, a Moscow-based popular internet portal and one of the largest blogging platforms on the Russian internet, was observed using confidential Google seller ID ca-pub-9165516179791802.
It is unclear if publicly traded, international corporations like Trustpilot or national museums like the Smithsonian are utilizing “individual” (rather than “business”) Google publisher accounts to serve ads on their websites. If they are using “business” accounts, it is unclear why Google’s sellers.json file lists some of the aforementioned records as confidential.
Google’s documentation states that “At this time, we do not recommend making buying decisions based on confidentiality.”
However, many of the sanctioned websites observed in this study were specifically using confidential Google seller IDs. Furthermore, many of those confidential seller IDs from sanctioned websites are re-used on dozens of other websites. If an advertiser cannot know who is the owner or operator of a specific Google seller ID, there is a non-zero percent possibility that their ad budget could be forwarded to an entity that works with sanctioned websites.
Furthermore, during the course of this study, many Russian domains were observed serving ads via confidential Google Seller IDs, based on data from different sources such as Common Crawl, URLScan.io, and DeepSee.io.
There were 64,606 websites which end in the “.ru” Russian ccTLD where various Google seller IDs were observed in HTTPS requests to Google ad serving endpoints. These 64,606 Russian websites were observed utilizing 20,366 distinct Google seller IDs. Of those 20,366 Google seller IDs, 13,584 (66.7%) were marked as confidential in Google’s sellers.json.
51,294 of the 64,606 “.ru” Russian websites were observed using at least one of confidential Google seller IDs. Some of the confidential seller IDs were observed being re-used on thousands of different websites. For example, confidential Google seller ID pub-7890420508150514 was observed in use on 2,998 different “.ru” Russian websites. The seller ID was also observed in use on 1,536 different websites which do not end in a ‘.ru’ ccTLD.
Many confidential Google seller IDs are observed being used on both “.ru” and non-”.ru” ccTLD websites.
Google’s ad buying tools make it difficult to assess who is being paid for ad inventory
Google is in a small minority amongst large Western ad tech firms, in that it has both a large “sell-side” business that works with website and app owners to serve ads, as well as a “buy-side” side business, which works with advertisers and media agencies to help them configure ad buying campaigns. Most other major open web ad tech companies only work with the “sell-side” (publishers) or “buy-side” (advertisers).
The previous section focused on Google’s sell-side practices, including their inventory of ad-hosting websites and (potential lack of) transparency in Google’s Sellers.json manifest file.
This section will focus on the experiences of buy-side advertisers, who are using Google’s software tools to purchase ads and allocate media budgets. The section will primarily focus on Google’s enterprise ad buying software - Display & Video 360 (DV360) and SMB ad buying tool - Google Adwords (currently referred to simply as “Google Ads”).
Some media buyers may specifically want to avoid purchasing ads from accounts or sellers where it is not clear who is getting paid for the ad buy. For example, if you are a brand or advertiser with a very sensitive corporate “image” or branding, you may not want your ad buy to be funding a media entity or website that undermines your organization’s stated ethics or political or social views.
As mentioned previously, Google’s Sellers.json is highly redacted - the ownership of many seller IDs is confidential. Google’s documentation states that “At this time, we do not recommend making buying decisions based on confidentiality.”
However, Google’s view point does not appear to be universally shared in the ad tech industry.
Several ad tech industry thought leaders and professionals suggested that it may be prudent to avoid purchasing ads from confidential sellers.
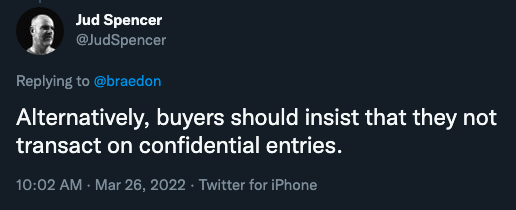
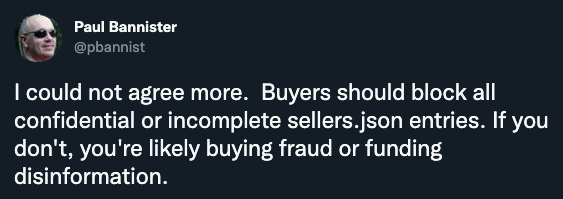
One ad tech industry thought leader specifically said: “Buyers should block all confidential or incomplete sellers.json entries. If you don't, you're likely buying fraud or funding disinformation.”
Adalytics reached out to The Trade Desk, one of the world’s largest open web programmatic ad platforms, to ask how they view the risks or concerns associated with confidential sellers. Jud Spencer, Marketplace Quality Engineer at the Trade Desk, responded:
“Ad tech is a financial marketplace and being able to determine where payments are transacted increases trust in that marketplace. A confidential entity is essentially an unknown entity which loses that same trust. Well-designed systems will ensure that untrusted entities/sellers are blocked everywhere, not just the paths where previous issues were discovered. It’s no different than the situation that we had before sellers.json. I can’t imagine going back to a world where we didn’t know all of the entities that our customers are transacting through.”
Given the observations in this study, the prevalence of confidential seller IDs in Google’s Sellers.json, and the recommendations of various (non-Google) industry professionals, one may reasonably ask: “How easy is it to avoid buying from confidential sellers on Google’s ad buying platforms?”
Adalytics posed this question to six experienced media agency ad buyers and traders.
One European ad buyer (who reported they have five years of direct experience with Google’s ad buying tools), responded: "I don't know how to block confidential sellers. I use Google Adwords, and I never saw a setting related to ads.txt".
Adalytics reached out to an experienced international media agency digital media buyer. This media buyer reported they had 10 years of experience in programmatic advertising, and 6 years of experience with Google's DV360 ad buying platform (or its predecessors).
Adalytics asked the media buyer if they could think of a way to block all confidential or incomplete sellers.json entries from their ad buy via Google's DV360 DSP. The media agency professional responded:
“DV360 allows a buyer to choose whether the inventory where ads are to be served is either portrayed as DIRECT, RESELLER or either in the domains ads.txt and even if the site does not have an actual ads.txt. That said, the actual link to the sellers.json and decisioning over it is not in the buyer's hands through the interface. This means buyers are forced to go back to the ancient method of inclusion list, which is tedious but the only applicable solution.There isn't any other way than an inclusion list, DV360 does not provide you the tools to prevent from running in confidential sellers.json entries in the platform.”
Another programmatic ad tech specialist, with several years of experience with Google’s DV360 platform, responded:
- “DV360's standard console reporting does not provide information about sellers (seller IDs or seller names). So, for example, a buyer can know it purchased [sic] an impression on vice.com but cannot know if the impression was sold directly by Vice or by an intermediary like EX.CO.”
- “DV360 buyers can get this information in Ads Data Hub.”
- “DV360 also does not allow buyers to block specific sellers. It's possible to deprioritize certain sellers by building a custom bidding model, but it's not possible to completely block a seller.”
- “Most Google seller accounts appear to be unavailable to non-Google DSPs.”
Based on the responses provided by these users of Google’s ad buying tools, it appears that it is not possible (or at least, not widely known) how an ad buyer could specifically avoid buying from confidential Google seller accounts. This may possibly be a limitation in Google’s DV360 and Adwords dashboards. Furthermore, it appears that Google’s standard DV360 reporting does not include information on which specific seller IDs were involved in an ad buy - this may only be accessible through Ads Data Hub or Data Transfer v2.0 log files.
Google’s DV360 dashboard does have a setting called: “Authorized seller targeting in Display & Video 360”. This setting allows a media buyer to select one of three options: “Authorized Direct Sellers”, “Authorized Direct Sellers and Resellers”, or “Authorized and Non-Participating Publishers”. These three options make no mention of confidential seller accounts.
Adalytics also reached out to The Trade Desk for their perspective on confidential seller IDs. Specifically, Adalytics inquired whether Trade Desk allows their clients to make ad buying decisions based on publisher seller IDs. Anna Wolk, Lead Director of Marketplace Quality, responded:
“The Trade Desk strives for total supply chain transparency for our clients. We manage seller restrictions and we also offer targeting and reporting features for our buyers based on sellers.json. Without a non-confidential sellers.json entry, we restrict any transaction on confidential sellers by default."
Notably, throughout the course of this study, there were no ads observed on some of the aforementioned OFAC sanctioned websites purchased via the Trade Desk. It is ostensibly plausible that The Trade Desk’s default restrictions on confidential seller IDs helped safeguard their clients ads from serving on sanctioned websites that were primarily using confidential IDs.
A Google DV360 ad buy shows large numbers of “Unknown” ad placements
One of the Google DV360 ad buyers Adalytics spoke with shared some data from an ad campaign they conducted. This campaign involved a seven-figure USD ad budget (e.g., more than $1,000,000 in ad spend).
The ad buyer generated a report using DV360’s standard reporting tools to show on which websites the ads ran on.
When the spreadsheet was sorted in descending order, the top website by ad impressions was yahoo.com. 13% of the ads in this campaign served on yahoo.com. 11% of the ads served on Youtube.
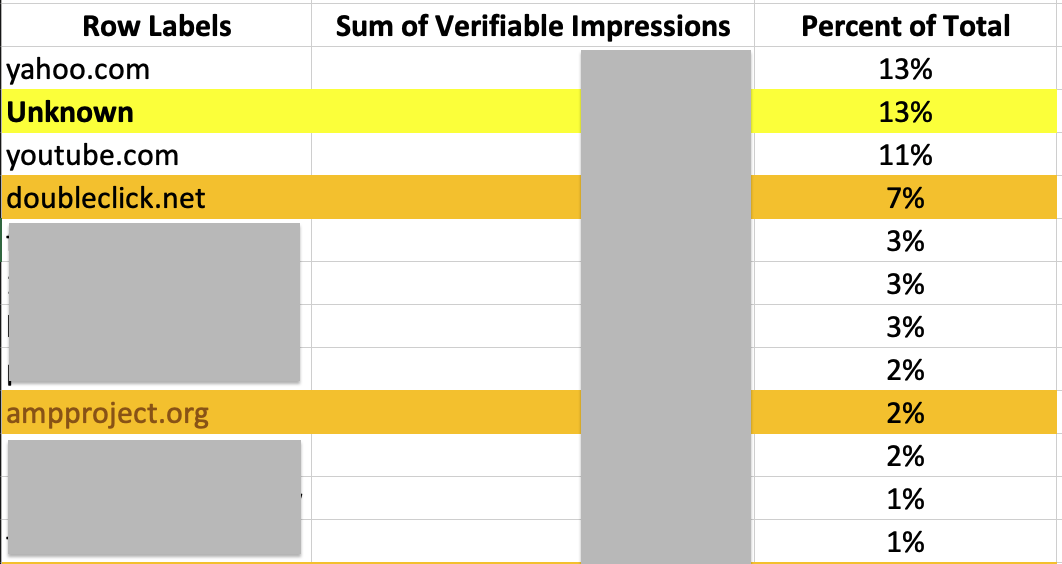
However, for 13% of impressions in this ad campaign, DV360 reported the website on which the ads ran as “Unknown”.
Furthermore, 7% of the ads ran on “doubleclick.net”. This is not an actual website, but rather, an ad serving domain used by Google. Doubleclick was an ad exchange that Google acquired in 2008. Lastly, for 2% of the ads, the reported website was “ampproject.org”. This is also not a “publisher” website, but rather, a domain that gets invoked when websites serve content for mobile devices.
This would suggest that for at least 22% of the ads purchased in this $1M+ USD ad campaign, the media buyer does not know where the ads ran or who and what entities were funded by their ad buy because Google does not appear to make the data readily available.
Furthermore, the full site placement list is several thousands of domains long, following a long tail distribution. One of the Russian domains in this media buyer’s DV360 placement report is currently explicitly mentioned on a US Treasury sanctions list.
There was also a few impressions which were served on an pornographic adult content website. Google’s Publisher Policies do not allow sexually explicit content. It is unclear how much money was allocated to each publisher in this DV360 placement report. If one makes a (likely false or over-simplified) assumption that the average spend rate on each website was roughly uniform, that means that at least 22% of $1,000,000+ USD could not be fully accounted for, in terms of which media organization was paid for these ads.
Which brands & advertisers had their ads served on potentially sanctioned websites?
The ads of many advertisers, both large and small, were observed on some of the aforementioned potentially sanctioned websites. Several brands had their ads served on sites that were explicitly listed on the US Department of Treasury Office of Foreign Assets Control (OFAC) Specially Designated Nationals And Blocked Persons (SDN) List. Some of the advertisers’ ads were also observed on websites that may potentially be sanctioned, because those sites are possibly owned or operated by entities in regions that are under “comprehensive” sanctions, such as Iran, Syria, Crimea, and the Donetsk People's Republic.
The vast majority of these advertisers appeared to be using either Google DV360 or Google Adwords (Ads) software tools for purchasing ads.
In addition to the large numbers of small and medium businesses whose ads were observed on some of the aforementioned websites, a few of the larger companies and organizations whose ads ran on these sites via Google’s ad exchange include:
- Huawei
- Google itself (chromeenterprise.google)
- Bankers Compliance Consulting (bankerscompliance.com)
- Yale University School of Management (depot.som.yale.edu)
- Oxford University Business School
- Citibank
- Husqvarna Group (Swedish machine & equipment manufacturer)
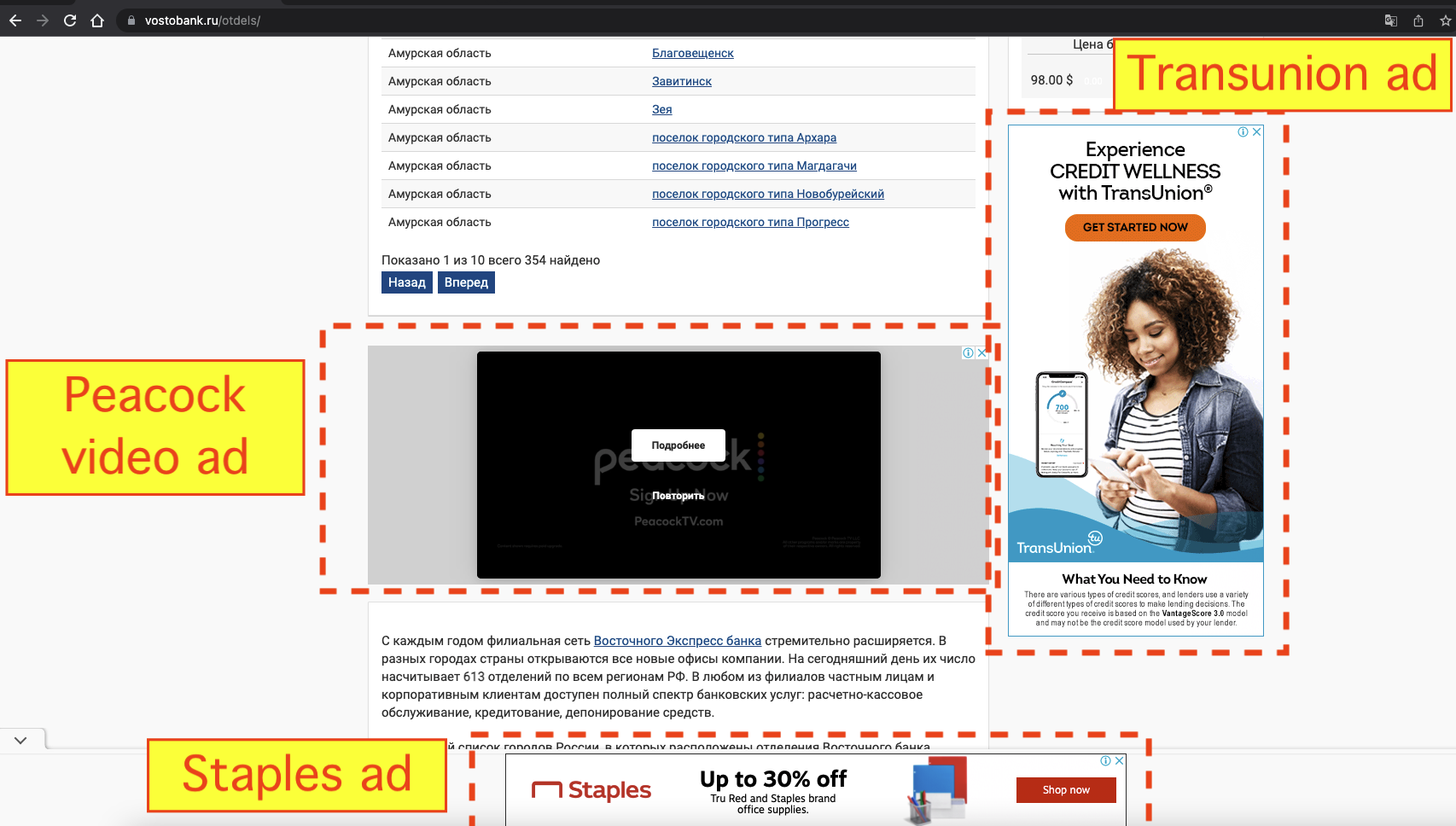
- Transunion
- PayPal (joinhoney.com browser extension)
- Adidas
- California Department of Social Services (CalFresh - calfresh.dss.ca.gov)
- US Department of Agriculture (paying for CalFresh ads - calfresh.dss.ca.gov)
- Thermo Fisher Scientific
- Dunkin Donuts
- IONOS
- Twilio
- Washington State Department of Health (doh.wa.gov)
- New York Life Insurance Company
- Lending Tree
- NBCUniversal (Peacock)
- Paramount Global (Nick JR)
- Alibaba
- Hello Fresh
- Inland Revenue Authority of Singapore (iras.gov.sg)
- GoDaddy (web domain registrar)
- Hertz car rental
- Proofpoint
- Subaru
- Teradata
- Kayak (travel agency)
- Bestbuy
- LATAM airlines
- Semrush
- University of Miami Health System
A few visual examples are provided below.
Which media agencies may have transacted upon potentially sanctioned websites?
Many media agency holding companies have announced recently that they are in “the process of exiting Russia”. British holding company WPP announced it was ceasing trading in Russia. Interpublic Group (IPG) announced it was suspending its operations in Russia. The CEO of Publicis Groupe, Arthur Sadoun, said in a statement that the agency was “immediately stopping all of our operations, engagement and investment in Russia”. Dentsu International and Omnicom similarly announced they were ceasing or reducing operations in Russia.
However, some advertising industry thought leaders have asked whether these agencies' statements also signify that the agencies will be reducing their ad buys from Russian linked entities.
Omar Oakes, Editor at the The Media Leader, wrote on March 21, 2022:
“Much of the world's ad fraud is known to operate in Russia, either through state-backed disinformation activity or organised crime.
It’s one thing for media buyers to forego traditional media billings in Russia for the sake of complying with sanctions. But if they are continuing to invest in online advertising inventory that effectively keeps money flowing to Russia, then there is a real risk that their clients – the brands who are not supposed to be spending media in Russia – will be exposed. There is an argument that, much like being hooked on Russian gas and oil, it is too difficult or too costly to do what is necessary to tackle Russia-based ad fraud.
Crucially, the issue of Russian sanctions has made ad fraud and poor accounting standards a much bigger issue than media effectiveness or return on investment. We’re talking about major brand’s adspend potentially supporting the Kremlin at a time when Russia has outrageously invaded a sovereign European nation.”
Throughout the course of this research study, it appears that the ads of many of the aforementioned media agencies (and their client brands) were served on Russian publisher domains, including some domains that are explicitly mentioned on the US Treasury’s SDN sanctions list.
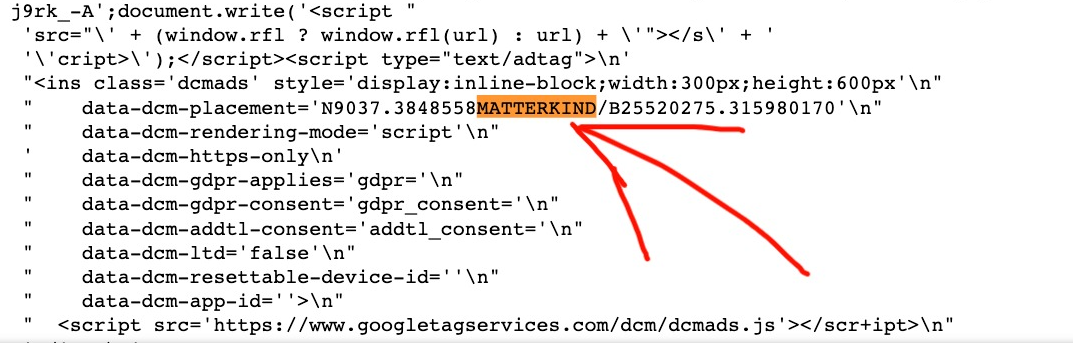
For example, the source code of the ad creatives served on some of the aforementioned SDN listed websites contained references to various media agencies. A relatively large number of ad creatives loading on these websites included Doubleclick Campaign Manager (DCM) Javascript tags that mentioned “matterkind”. Matterkind (previously Cadreon) is the agency trading desk of Mediabrands Worldwide, which itself is part of IPG.
One can also try to cross reference specific brands with their media agencies of record using public press releases. Below are some examples of brands whose ads had been observed in this study, and related press releases that mention those brands’ agencies:
- Publicis Groupe has been publicly mentioned as the media buying or agency of record for Facebook, Citibank, NBC, Dunkin Donuts, Wavemaker, part of WPP and GroupM, has been listed as the agency for ViacomCBS/Paramount and GoDaddy (in 2015).
- MediaCom, part of WPP’s GroupM, was listed as the media agency for Adidas (in 2018)
- CrossMedia lists Hertz car rental as one of its clients.
- Essence, part of WPP, was listed as the media agency for Google
- R2C was listed as the media agency for Lending Tree (in 2018).
- Kepler Group was listed as a media agency for PayPal.
- Madras Global was listed as the agency of record for Thermo Fisher (in 2018).
Adalytics received access to the brand safety “exclusion” list of one of these major media agencies. The exclusion list contained a large number of websites and mobile apps which the agency disallows their clients’ ads from running on. This was a so-called “agency global list”, which in theory is applied to all of the agency’s client campaigns (as opposed to a client-specific exclusion list).
The agency exclusion disallowed many publishers for copyright or IP violations, pornographic content, hate speech, or terrorism. However, not a single publisher or domain was disallowed because of its status as a US Treasury sanctioned entity.
Furthermore, this agency’s exclusion list did not include any of the Treasury SDN, Syrian, Iranian, Crimean, Donetsk People's Republic, or Luhansk People's Republic websites.
Adalytics reached out to several media agency executives to inquire how much formal training do agency media buyers or programmatic traders receive each year in US Treasury sanctions compliance.
One agency executive, speaking on the condition of anonymity so he could speak freely, said: "While agency buyers may be generally aware of legal requirements as it relates to OFAC, I'm not aware of any formal training or reference material in place to block those sites. Agencies often rely on publisher or platform partners, such as their DSP, SSP, or brand safety partners like IAS and DoubleVerify, to manage those requirements and ensure clients do not inadvertently show up on those sites.” Adalytics notified another senior media agency executive about the phenomenon of ads running on Treasury sanctioned websites, and asked the executive for a comment regarding how they perceived this situation. The media agency executive responded:
"It's unacceptable. It's proof that 3rd Party Verification Vendors (IAS and Double Verify), trade groups (IAB and TAG), and certifications (BSI and MRC) are not delivering on their promises."
Which brand safety vendors were observed in ad creatives loading on websites
As described in the previous section, some agency buyers rely on brand safety firms to ensure that their ads do not serve on certain websites which are inconsistent with a firm’s political, legal, social, or ethics prerogatives.
Many of the advertisers or media agencies whose ads were observed in this study appear to utilize Javascript from major brand safety vendors.
For example, many of the IPG Matterkind ad creatives appeared to contain Javascript from DoubleVerify in the source code. Business Insider previously reported that UM and GroupM were DoubleVerify users (as of 2020).
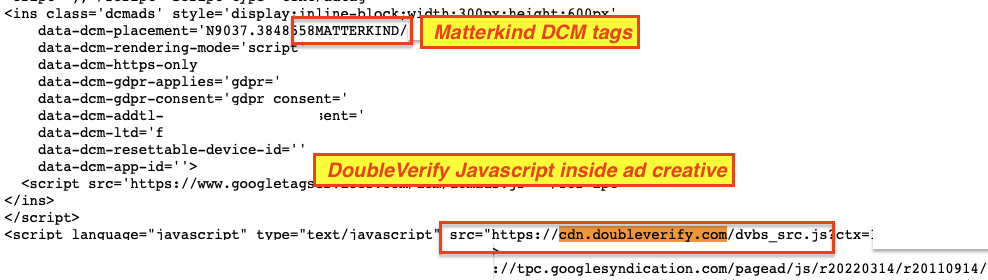
Some of the other ads observed on potentially sanctioned websites also included Javascript tags from adsafeprotected.com, a domain owned by Integral Ad Science (IAS). Other ad creatives included Javascript from Oracle Moat.
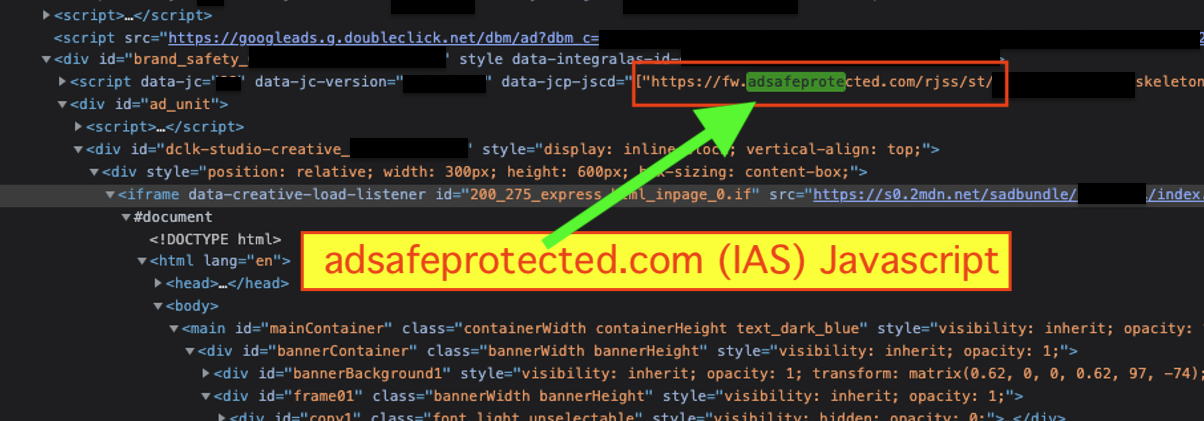
It is unclear what these Javascript tags are used for. For example, some of the observed Javascript tags from DoubleVerify or IAS may be purely used to measure the viewability of an ad slot, rather than for brand safety monitoring purposes.
Conclusion
Caveats & Limitations
Interpreting the results of this observational study requires a lot of nuance and caution. This study should not be construed as a legal commentary or opinion. This study does not allege that any entities knowingly or intentionally violated US Treasury sanctions. This study did not make any extensive consultations with sanctions law experts. The study is meant to be viewed as a highly preliminary observational analysis of publicly available information and empirical data.
Furthermore, this study was entirely based on client-side browser observations and publicly available documents, such as those of the US Treasury OFAC website and various corporate press releases. This study cannot make any confident assessments on how much money, if any, was disbursed to sanctioned or sanctions-linked entities. For example, it is possible that even though ads were displayed on various websites, none of those ads involved money being exchanged between different accounts (non-payment). One ad tech expert pointed out that: “It is typical in brand safety for the DSP that incurred the violation not to charge the advertiser, whether the DSP does in fact make a payment for ‘failed’ ads is subject to each DSP’s individual policy.” Furthermore, because this study cannot extrapolate how much ad revenue (if any) the publishers mentioned in this study make. It’s possible that all of the aforementioned websites have low level audience traffic and generate very little ad revenue.
If anyone from Google or the other mentioned ad tech companies would like to help contextualize the data observed in this research, please reach out.
The owners or operators of many of the websites examined through the course of this study could not be readily identified using publicly available information. It is possible that owners or operators of some of the websites are not themselves sanctioned entities. For example, some of the Syrian, Crimean, or Iranian websites could be operated by entities who are outside those respective sanctioned regions. If any of the website owners or operators alluded to in this study would like to make any corrections to this study, please reach out so that we can correct any mis-specifications.
Furthermore, this study relied on the accuracy and currency of the Treasury SDN list. If there are any discrepancies, miss-specifications, or oversights in the SDN list or Treasury OFAC documents, those would propagate through the assumptions made in this study.
In many cases, it may not be immediately clear who was the party which was ultimately responsible for directing an ad placement. For example, certain ads may have been observed on a given website because of automated ad buying algorithms, media agencies, a buy-side platform, or a sell-side platform. It may not be possible to distinguish which of those actors was the primary agent that made the ad placement.
Discussion
This empirical study describes several observations which in isolation may not be overtly concerning, but when assembled, point to a potentially dangerous situation.
Google’s own publisher policies state they must comply with OFAC regulations, and that they do not allow publishers from Crimea, DNR, LNR, Syria, or Iran. However, this study observed that ads, including those for Google’s own products, were serving on a domain listed in the Treasury OFAC SDN sanctions list for years. At the time this report was being published on April 20th, 2022, Google ad exchange was still servicing possible Syrian, Iranian, and Crimean domains, despite most of these regions having been sanctioned for many years. In the past, Google’s ad exchange was observed monetizing websites that were linked to the Russian military and intelligence services for several years.
Unlike other major ad exchanges, most of Google’s seller IDs are redacted as “Confidential”, which may make it impossible for attentive media buyers to verify where they are sending their ad dollars to. All the sanctioned domains observed in this study used “Confidential” Google accounts. Furthermore, many of those confidential seller IDs were re-used between sanctioned domains and other, unrelated domains. This inter-mingling of sanctioned and non-sanctioned websites makes it extremely difficult for advertisers to be certain that their media budgets are not being directed towards sanctioned organizations, such as those linked to the Russian military.
This study observed many instances where major Fortune 500 brands (such as Citibank, Facebook, PayPal, Adidas, and Google itself) and international media agency holding companies had their ads rendered on sites that were explicitly enumerated in the Treasury OFAC SDN sanctions list. Many such media buyers may depend on Google to curate its ad inventory to prevent sanctioned sites from being allowed in the first place.
It appears that for up to 22% of some ad campaigns, Google’s own ad buying tools report the ad placements as unknown. In these cases, it is impossible for the media buyers to be certain that their ad dollars were not funneled to a sanctioned Russian bank or a sanctioned entity linked to Russian military intelligence.
Lastly, Google’s own ad buying tools, such as DV360 and Adwords, do not appear to provide ad buyers with the ability to easily avoid buying from “Confidential” sellers. The tools also do not easily allow media buyers to dis-allow all Iranian, Syrian, or Crimean, sites from their ad buys. This lack of configurability and tooling makes it so that programmatic buyers may not have many avenues to protect their media investments from sanctioned entities, outside of buying on very well-defined inclusion lists. A previous article published by Wired in 2019 noted that multiple Google Ads users complained about the inability to exclude Iranian, North Korean, or Syrian consumers from being shown their ads. Other ad buying platforms, like The Trade Desk, appear to insist on transparency in their virtual supply chains.
Google has taken several steps, including pausing the monetization of Russian state-funded media (Feb. 26th), pausing “ monetization of content that exploits, dismisses, or condones the war” (March 23), and “pausing the creation of new Russian accounts on AdSense, AdMob, and Google Ad Manager.” However, researchers have continued to observe sites that condone the war in Ukraine being monetized with ads. Furthermore, as of April 2022, the majority of Google’s sellers.json is still marked as confidential with regards to publisher account ownership.
The US government is trying to crack down on efforts by the Russian government to evade the sanctions by setting up front companies. The US released a list of 21 entities that it believed were acting as fronts for sanctioned Russian companies or the Russian government. The 21 entities are thought to be linked to a sprawling network, which extends outward to include defense procurement firms, middlemen and front companies located in the U.K., Spain, Finland, Singapore, Malta and France.
One (speculative) possibility may be that some of these front companies are able to accrue Western money by creating British or French websites, signing up for ad exchange accounts, and making money from ads placed on those websites. In the past, journalist Megan Graham from CNBC demonstrated that she was able to open ad exchange accounts for a bunch of fake websites she created within a few days. A report by the World Federation of Advertisers (WFA) stated that “Ad fraud is 'second only to the drugs trade' as a source of income for organized crime”, and that it “will become so rampant that it will cost advertisers more than $50bn by 2025”.
Regulators, law makers, media agencies, and marketers may ask whether there is a need for Know Your Customer (KYC) regulations within the ad tech industry, given the billions of dollars that transact annually through its virtual supply chains.
Adalytics shared the results of this study with a Fortune 500 marketing executive, and asked for his opinion on the matter. The executive responded (anonymously): "We have teams of IT, compliance, legal and other experts that work every day to ensure that we stay within the law and also stay true to our corporate ethos.The idea that our brands and advertising dollars could be being directed to websites in sanctioned countries like Russia, Syria and Iran is very disturbing.
The complexity of the global online advertising marketplace together with the real risk of advertising dollars and valuable company brands being misdirected to sanctioned websites suggests that more strict oversight is needed by companies that manage corporate advertising like media agencies, ad tech platforms and brand safety technology providers.
Greater transparency on where our company's ad dollars are being spent is required. We cannot allow ourselves to be exposed to advertising practices by advertising vendors that are in breach of US Treasury sanctions, or for that matter, on any website connected to illegal activity or that falls outside our company's ethos."
Adalytics also shared some of the results of this study with Bob Hoffman, a marketing thought leader who has spoken to the British and European Parliaments before on digital advertising. Mr. Hoffman commented:
“Marketers do not know where their advertising is appearing, who they are paying, or what they are getting [...] Agencies are equally responsible. Despite their promises to the contrary, they do not have the ability to reliably track the money they are spending on their clients’ behalf, nor do they have the resources to determine where the ads are appearing. A recent study by the ISBA (Incorporated Society of British Advertisers) showed that, on average, a programmatic ad buy directs ads to 40,000 websites. Monitoring all this traffic is a monumental job that marketers and agencies relegate to undependable suppliers or software that does not get under the hood of these websites and cannot provide reliable information on what is running, where it is running, and who really owns the website.”
