Photo of a sculpture, showing a child with wings with a finger over their lips
WARNING: This empirical research report – which is based on publicly available information - deals with the issue of “brand safety” and, thus, must necessarily focus on language and/or ideas that many (including the authors of this report) may consider offensive. Specifically, this report contains depictions or mentions of pornographic, zoophilic, racist, offensive, and graphically violent content which may not be suitable for all audiences or for the workplace environment. Reader discretion is strongly advised.
DISCLAIMER: Please see the “Caveats & Limitations'' section of this report for further details. Like all Adalytics reports, this report relies on data and observations that are intended to be “reader-replicable.” To preserve this transparency, Adalytics makes no attempt to disturb/alter the provision of services as observed. This report describes empirical observations from a sample of domains. This report makes no assertions or claims with regards to the quantitative magnitude of some of the phenomena observed in this study. This observational research study does not make any assertions regarding causality, provenance, intent, quantitative impact, or relative abundance. This study does not make any recommendations to media buyers with regards to whether or not to transact with specific technology vendors or with specific publishers. The study is merely intended to present a set of public observations, so that readers can come to their own conclusions and make their own informed decisions.
A multi-national brand’s head of global media requested that Adalytics review its ad placements for “brand safety”. The brand was told by their media agency holding company, by their demand side platform (DSP), and their brand safety verification vendor that the brand’s ad campaigns were 100% brand safe.
The brand’s ads were observed serving on a variety of pages, including some that the brand found to be brand unsafe. For example, the brand’s ads were served on pages with titles such as: “Big Black Dildo” and “No Cock Like Horse Cock.” The brand - which was paying for pre-bid brand safety tech, keyword blocking tech, and post-bid brand safety tech - was surprised that their ads were served on these placements.
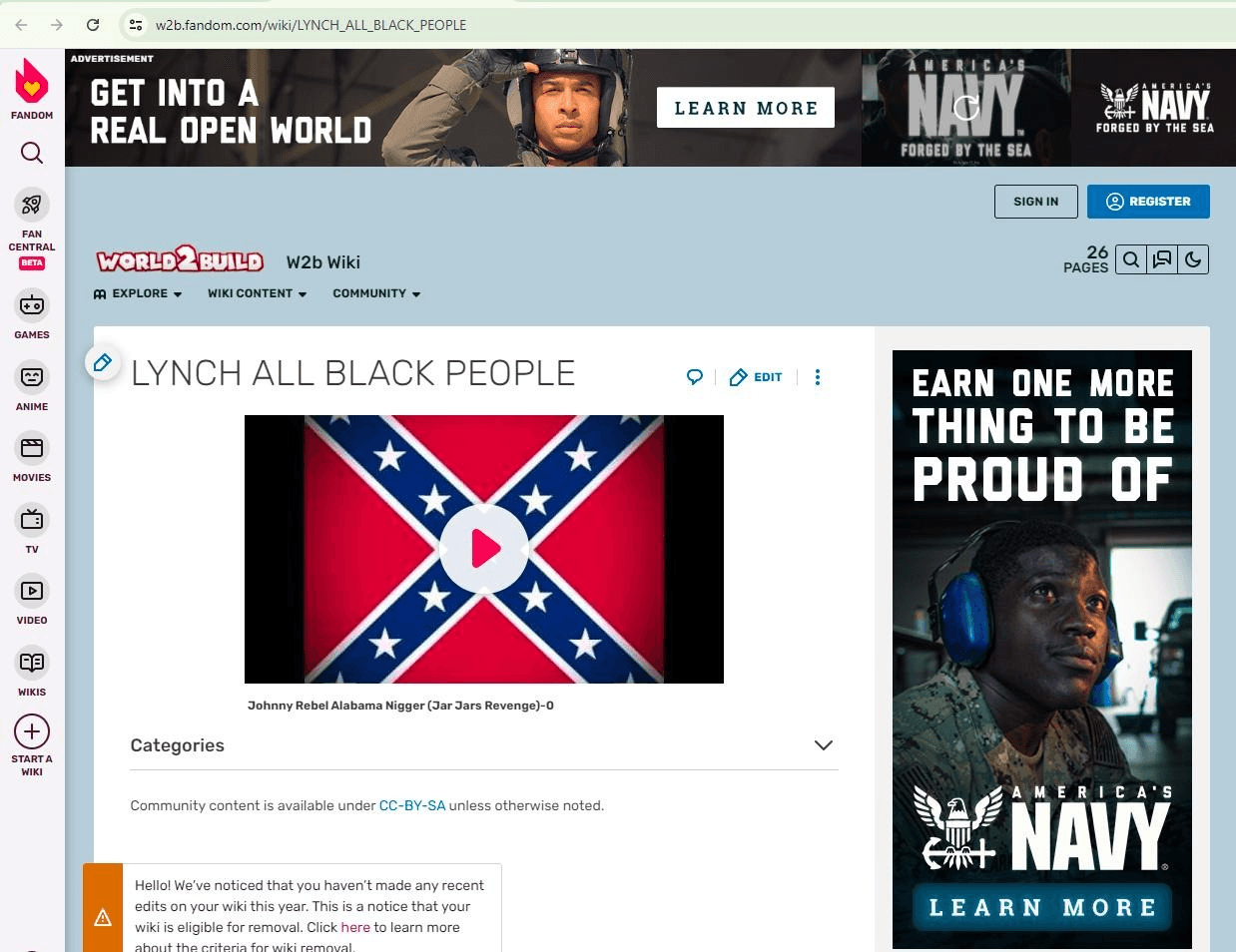
Example of a page where ads from various brands were observed
Prompted by this experience, Adalytics began investigating adjacent content and how ads were being served on these types of content.
During the course of this observational research, major brands - such as Procter & Gamble, Microsoft, Lexus, Meta, Kenvue, Ikea, Mercedes Benz, Volvo, the US Navy, HP, Applebee’s, Pfizer, Disney, 3M, UPS, Nestle, Grammarly, AMC Theaters, Live Nation Entertainment, Thomas Reuters, Nestle, Marriott, The Dairy Alliance, Nintendo, Pepsi, Abbvie, T-Mobile, NBCUniversal, Mattress Firm, Amazon, Wawa, Autozone, SC Johnson, OnDeck, Sam’s Club, Hertz, Lipton, Walmart, and Prudential - had their ads served on pages with exact titles such as:
“Coprophilia”
“No cock like horse cock”
“Big black dildo”
“Decapitation”
“Zoophilia”
“Gag Penis”
“Big Black N***a Dicks” (redacted in this report)
“Child pornography”
“LY*CH ALL B***K PEOPLE” (redacted in this report)
"N*****" (redacted in this report)
“Super Mario 3 Masturbation”
“Anal sex”
Many of the ads observed on this content were noted to include a Javascript from vendors such as DoubleVerify or Integral Ad Science.
Screenshot of a Citizens Bank ad observed in an article titled: “Anal Sex”. The source code of the Citizens Bank ad includes Javascript from IAS.
Furthermore, the source code of many of these ads appeared to include references such as “maxDoubleVerifyBrandSafety” or “integralBrandSafety”.
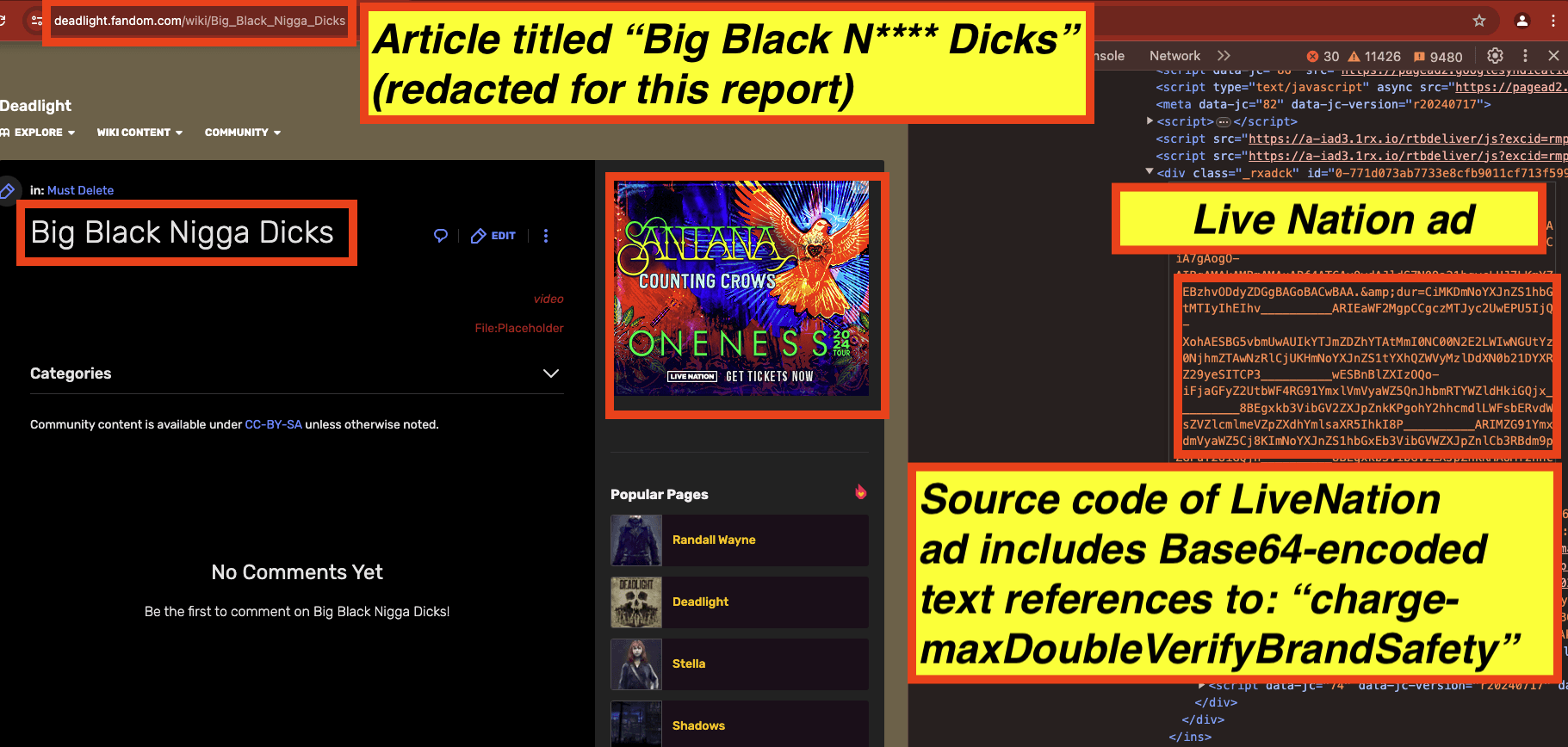
Screenshot of an Live Nation ad seen on a page titled: “Big Black N***a Dicks” (redacted in this report). The Live Nation ad includes Base64-encoded text references to “charge-maxDoubleVerifyBrandSafety”.
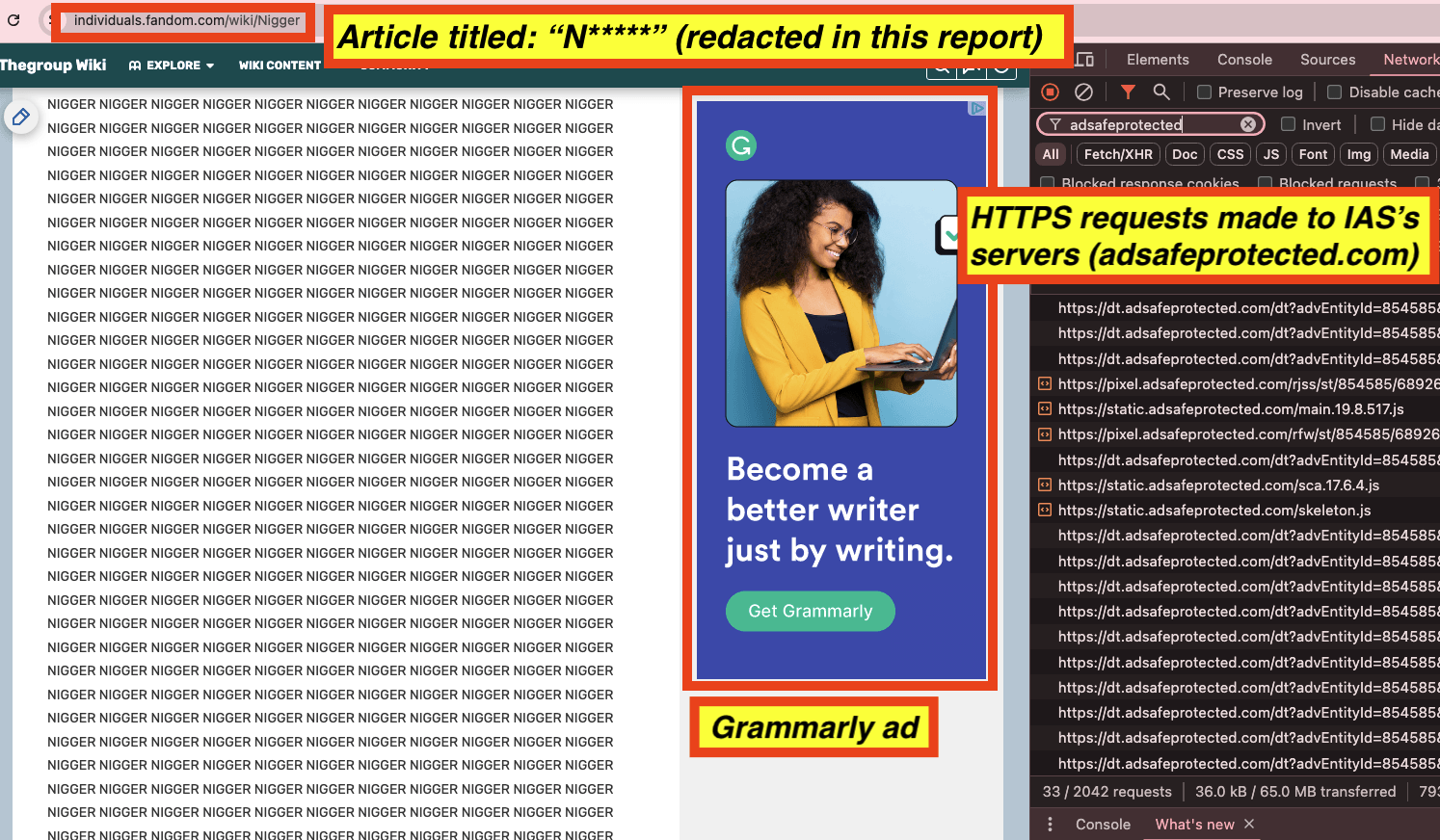
Screenshot of a Grammarly ad seen on a page titled: "N*****" (redacted in this report). The Grammarly ad includes a Base64-encoded text reference to “charge-charge-allIntegralBrandSafety”. The right side of the screenshot shows 33 HTTPS requests made to various “adsafeprotected.com” server endpoints; “adsafeprotected.com” is a domain operated by IAS.
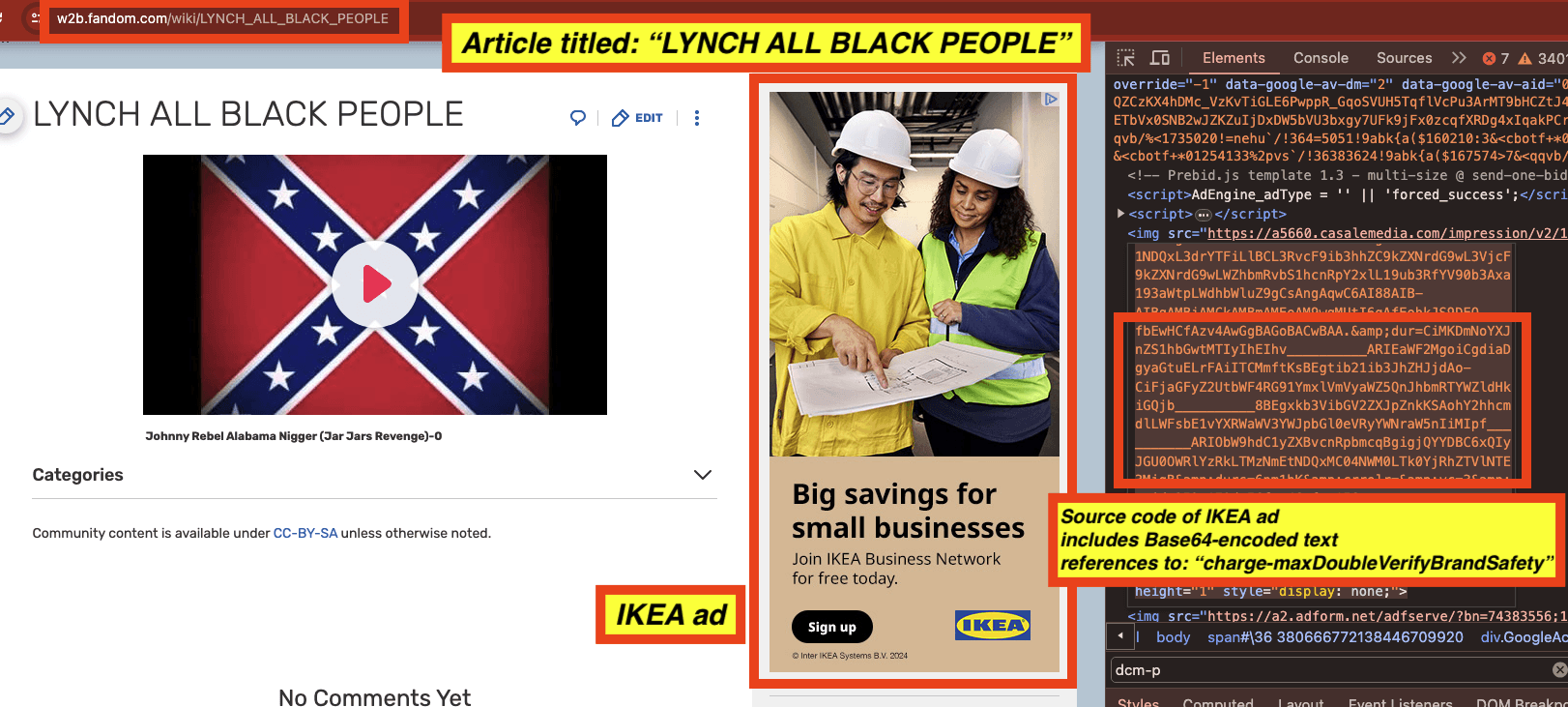
Screenshot of an IKEA ad seen on a page titled: “LY*CH ALL B***K PEOPLE” (redacted in this report). The IKEA ad includes references to WPP/GroupM’s Xaxis, and Base64-encoded text references to “charge-maxDoubleVerifyBrandSafety”. The IAB states that “content that contains hate speech directed at a protected class would be inappropriate for any advertising”.
Further conversations with multiple other brands whose ads were appearing on these pages confirmed that some of the other brands were paying for prebid, postbid, and keyword exclusion brand safety technology.
One Fortune 500 brand marketer stated:
“The facts uncovered in this research make something alarmingly clear – not only does full URL transparency for advertisers need to be adopted immediately by all DSPs, but also the brand safety & verification technologies that claim to have been providing URL & Page level protection have been nothing short of insufficient and need to immediately review and update their tools to actually include full URL data and properly classify content to protect brands as well as publishers. If this is not addressed, we will not allow our brand dollars to flow through a DSP, tagged with a Verification Provider that allows delivery to a page titled “L*NCH ALL ***** PEOPLE”. Completely unacceptable.”
Another Fortune 500 brand marketer stated:
“Is verification tech implemented correctly but not working? If so huge problem. Does not seem to be doing any page level scanning. Ultimately, advertisers want 100% of their ads to be in safe, suitable, viewable environments delivered to real consumers. Currently that is almost impossible to do at scale.”
A third Fortune 500 brand marketer stated:
“The problem with issues like this is that I can't actually verify my company's degree of exposure because none of the platforms we activate on or use for brand safety provide us with URL level reporting capabilities out of the box. But beyond that, it's not even that a level of exposure matters, it's that exposure itself is a line in the sand I don't want to cross. If I have served an ad on a URL containing "big black cock", what's to say that an ad didn't end up on a URL that contains the string "little boy cock", which I can't now just magically assume hasn't happened."
Furthermore, the media publisher hosting many of these pages appears to be utilizing the publisher specific Javascript tools provided by vendors such as IAS and DoubleVerify. This Javascript code from IAS and DoubleVerify appears to run before every single ad auction that triggers on pages with exact titles such as “Horse cock”, "N*****" (redacted in this report), “Decapitation”, “Child pornography” - before any ads are served. The publisher lists IAS and DoubleVerify as “partners”.
Both IAS and DoubleVerify have issued public statements about their use of AI technology within the context of brand safety.
In the graphic table below, one can see a sample of brands whose ads were observed on the selection of “potentially objectionable content” ads, and whose ads’ source code included Javascript from “adsafeprotected.com”. The IAS Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.




In the graphic table below, one can see a sample of brands whose ads were observed on the selection of “potentially objectionable content” ads, and whose ads’ source code included Javascript from “doubleverify.com”. The DoubleVerify Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.

Background - AI and Brand Safety technology
According to Integral Ad Science’s (IAS) website, “Brand safety refers to actions taken to protect brands from content that’s generally recognized as unsafe. For example, topics like hate speech and terrorism tend to present brand equity risk to most advertisers. Brand safety is for every brand and reflects the need to avoid serving ads adjacent to unsafe content – content that’s generally recognized as unsafe for any brand.”
According to the Interactive Advertising Bureau (IAB), an industry trade group:
“Defining Brand Safety - Brand Safety solutions enable a brand to avoid content that is generally considered to be inappropriate for any advertising, and unfit for publisher monetization regardless of the advertisement or brand. [...] For example, content that contains hate speech directed at a protected class would be inappropriate for any advertising.”
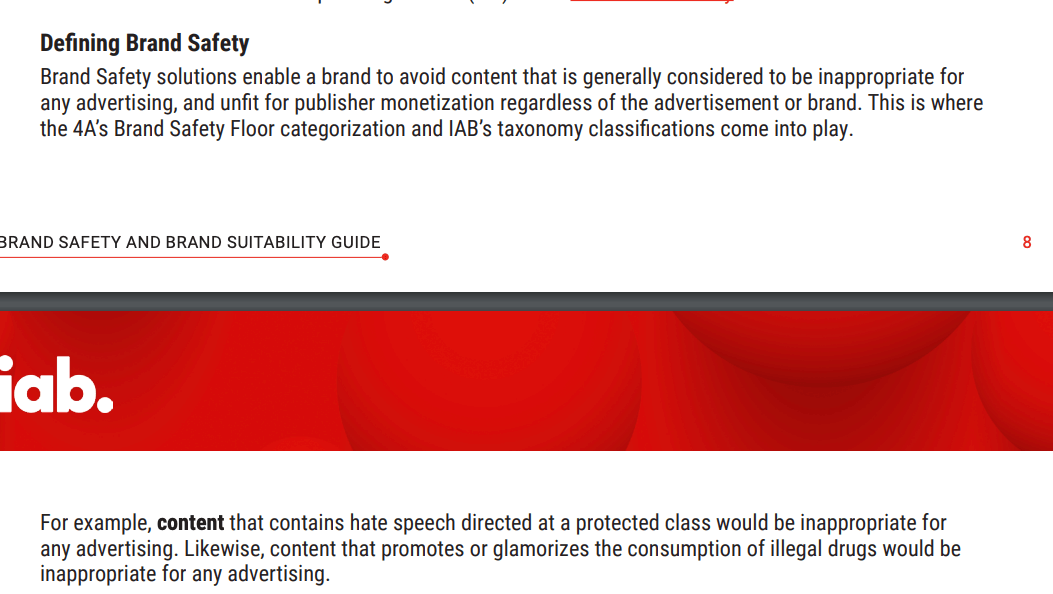
Screenshot of the Interactive Advertising Bureau (IAB) Brand Safety and Suitability Guide.
One government resource describes “pre-bid verification” as:
“Content detection and classification uses artificial intelligence (AI) or machine learning
(ML) to detect and classify pieces of online content into specific risk-level categories. The pieces of content analyzed could be news articles, user-generated content (UGC) such as Tweets or posts, or even YouTube videos. This process of classifying content and then blocking ads from appearing near [...] “risky” content is known as pre-bid verification."
Various companies such as DoubleVerify and Integral Ad Science (IAS) provide “brand safety” solutions.
For example, DoubleVerify’s website states that: “DV’s comprehensive brand safety and suitability solutions protect your brand's equity and reputation — across all media environments.”
Source: https://doubleverify.com/capabilities-brand-safety/
DoubleVerify’s website states: “Let Us Be Your Watchdog - DV's brand safety and suitability solution provides maximum protection for global media buys — across channels and formats, from programmatic avoidance to post-bid monitoring and blocking. Leveraging our centralized set-up and management, you can rest assured that your policies will be consistently enforced across all campaigns.”
DoubleVerify’s website references how it has a “classification engine that powers expansive content categorization across web” and “leading artificial intelligence (AI) technology to provide advertisers with the most accurate classification, while ensuring the broadest coverage and protection at scale” (emphasis added). It provides “comprehensive pre- and post-bid coverage.”

DoubleVerify’s website references “artificial intelligence (AI) technology
DoubleVerify’s 10-Q form states: "We are one of the industry’s leading media effectiveness platforms that leverages AI to drive superior outcomes for global brands."

DoubleVerify 10-Q form
IAS’s website states that its brand safety solutions: “Maximize both the impact and cost efficiency of campaigns by controlling the context in which they appear. Our patented cognitive semantic technology uses natural language processing (NLP) to dynamically comprehend the nuances of context. This includes sentiment and emotional analysis, enabling the most precise content classification at scale.”
Screenshot of IAS’s website describing its brand safety solutions
IAS’s website describing its brand safety solutions states: “PRECISE CLASSIFICATION OF CONTENT AT SCALE” “IAS Brand Safety and Suitability solutions maximize both the impact and cost efficiency of your campaigns. Go beyond keyword blocklists and URL scanners with intelligent and scalable solutions for contextual relevance.” The website states: “IAS is 42% more accurate than the next best provider at classifying online content”.
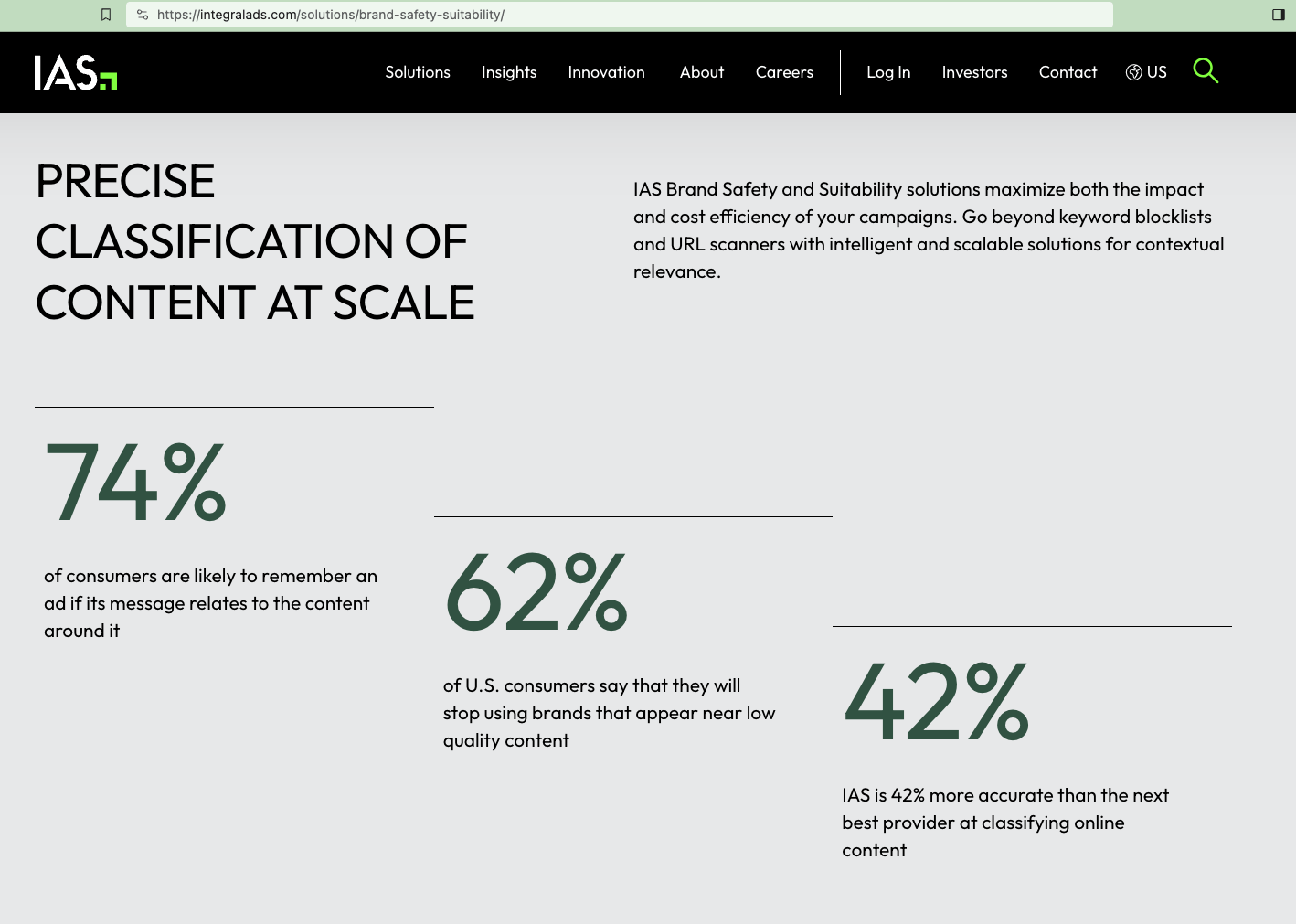
Screenshot of IAS’s website describing its brand safety solutions
According to IAS’s website, its brand safety solution uses “machine learning based methodology”.
IAS’s brand safety solution uses “machine learning based methodology”
IAS’s marketing materials on “brand safety” reference “Page-level analysis using machine learning and patented semantic technology for accuracy and precision.”

Screenshot of IAS’s Brand Safety One Sheet. The document references “Page-level analysis using machine learning and patented semantic technology for accuracy and precision”.
IAS’s website describes “Innovative tools like the AI-powered Total Media Quality suite”.
Source: https://integralads.com/insider/cannes-lions-2024-recap/
Source: https://integralads.com/insider/cannes-lions-2024-recap/
IAS investor materials reference “AI/ML enrichment” and “Real-time processing”.
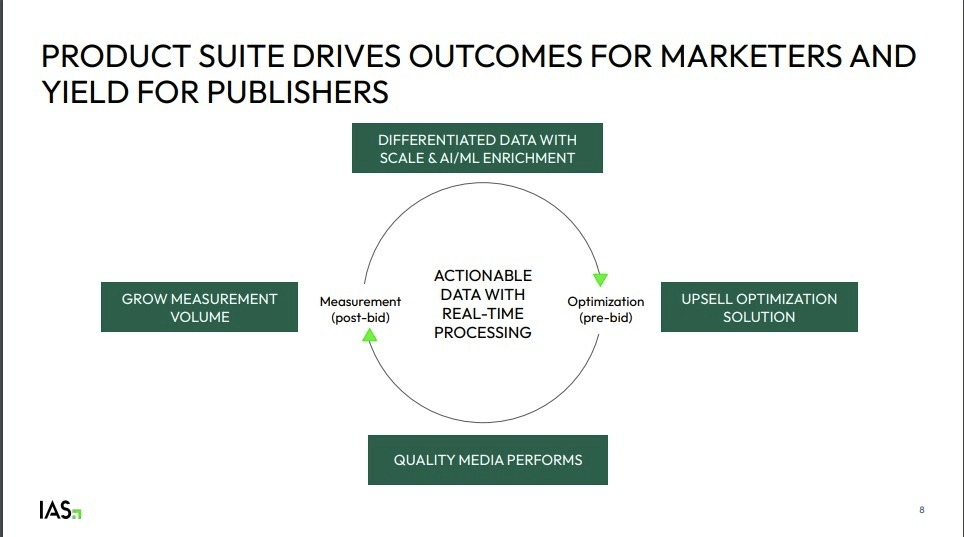
IAS materials reference “AI/ML enrichment” and “Real-time processing”. Source: Integral Ad Science (IAS) May 2024 Investor Presentation
IAS materials reference “AI/ML” data enrichment and “Real-time data processing”. Source: Integral Ad Science (IAS) May 2024 Investor Presentation
IAS’s CEO and social media accounts reference: “exciting developments happening at IAS as we continue to set the global benchmark for trust and transparency in digital media quality through the power of AI and data science."
IAS’s CEO and social media accounts reference: “exciting developments happening at IAS as we continue to set the global benchmark for trust and transparency in digital media quality through the power of AI and data science."
IAS’s social media accounts state: "we enable advertisers to further verify the safety and suitability of their digital media investments through AI-powered technology."
IAS’s social media accounts state: "we enable advertisers to further verify the safety and suitability of their digital media investments through AI-powered technology."
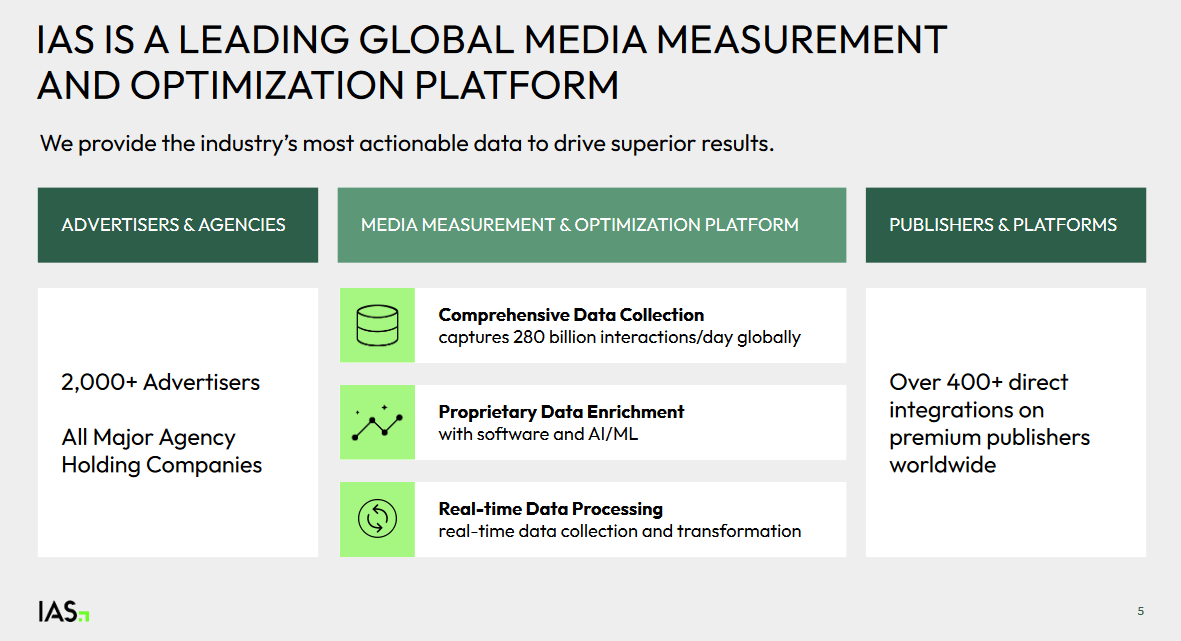
According to IAS’s 10-Q form: "Our platform uses advanced artificial intelligence ("AI") and machine learning ("ML") technologies to process over 280 billion daily digital interactions globally".

Screenshot of IAS’s 10-Q form
IAS’s CEO told industry trade press publication AdExchanger - “AI and ML are in the DNA of this field,” she said, and it’s at the heart of “everything that we do from a tech and innovation perspective.”
Screenshot of an AdExchanger article showing a quote from IAS’s CEO
In a call with investors and financial analysts, the CEO of IAS stated:
"On today’s call, I’ll address the importance of data integrity and our trusted AI-backed technology [...]
“Marketers trust IAS to protect, measure, inform, and optimize their brand campaigns. Their trust is based on the accuracy and reliability of our data. Data integrity is critical and inherent in all the reporting and insights we provide in every aspect of our business. Data science is at the heart of our business strategy. Our AI systems enable models that deliver classifications and analytics at greater speed that are scalable with extremely high precision [...]”
“In a recent IAS study, our AI technology delivered up to 74% more accurate brand suitability measurement across social media platforms when compared to other providers’ solutions."
“While IAS is focused on harnessing the power of AI, we are committed to doing it responsibly. We are investing in explainable AI which ensures that our customers can trust our models. The accuracy, reliability and integrity of our data is anchored in our AI innovation as well as in our critical role as an independent third-party provider. This allows us to maximize the value we offer all while maintaining and growing the trust customers have in IAS."

IAS Q1 2024 Prepared Remarks - https://investors.integralads.com/static-files/c5a07db5-8ea7-4586-806f-4a2935029177
Doubleverify is “accredited by the Media Rating Council (MRC) for detection and blocking for property-level brand safety and suitability”
According to DoubleVerify’s website, DoubleVerify is “accredited by the Media Rating Council (MRC) for detection and blocking for property-level brand safety and suitability within desktop, mobile web and mobile apps (certain metrics only)” (emphasis added).

Screenshot of DoubleVerify’s website, stating that DV is accredited by the Media Rating Council (MRC) for detection and blocking for property-level brand safety and suitability
DoubleVerify’s website states that it is Media Rating Council (MRC) accredited for “Standard Brand Suitability is available for site, page and app classifications, including platform-wide Brand Safety floor avoidance, along with app-specific segments based on app store Age Rating and App Star Reviews” (emphasis added).
Screenshot of DoubleVerify’s website - “DoubleVerify Earns MRC Accreditation for Suite of Programmatic Targeting Services”
IAS and Doubleverify are TAG certified for “Brand Safety”
The Trustworthy Accountability Group (TAG) is an advertising industry trade group and non-profit. TAG has a “Brand Safety Certified” program.
According to TAG’s “Brand Safety Certified - Certification Guidelines”:
“The mission of the TAG Brand Safety Certified Program is to significantly reduce the risk of the misplacement of advertising on digital media of all types, thereby upholding brand safety and protecting the integrity of digital advertising. The TAG Brand Safety Certified Program promotes the flow of advertising budgets to participants in digital advertising upholding an industry regulated framework for brand safety. The program serves the entire digital advertising supply chain by providing transparency, choice and control for buyers – enabling them to buy advertising inventory with confidence and creating a brand safety framework for sellers that increases the value of certified sellers' inventory.”
According to TAG’s “Brand Safety Certified - Certification Guidelines”:
“Any participating company acting as a direct buyer, intermediary, vendor or seller must employ the use of a TAG-recognised content taxonomy for defining and avoiding harmful content, as referenced in Appendix B. Digital advertisements may not be displayed in association with any content category floor defined in Appendix B.”
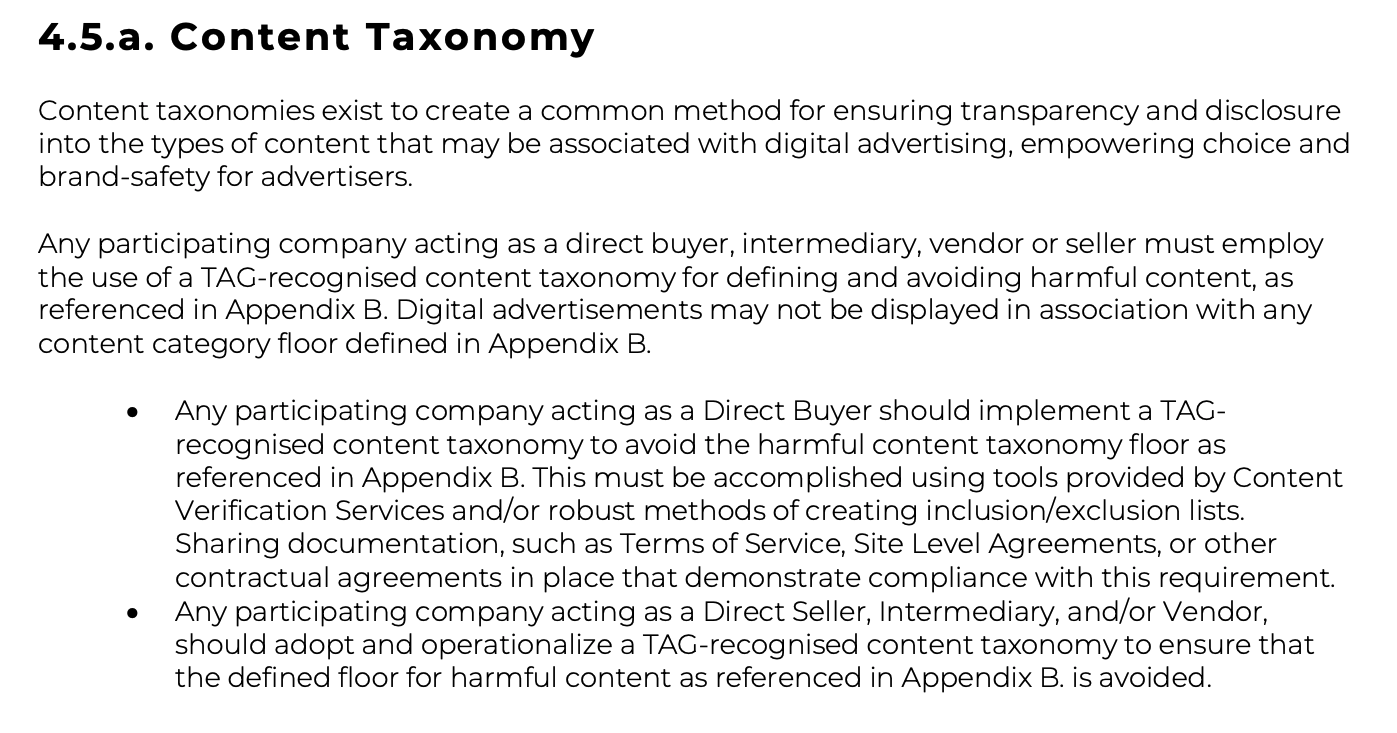
https://www.tagtoday.net/hubfs/BSC%20Guidelines.pdf
“The 11 “Sensitive Topics” content categories as defined by the IAB Tech Lab Content Taxonomy version 2.2, and at the “Floor” risk-rating. For more information on the IAB Tech Lab Content Taxonomy v2.2, please visit: https://iabtechlab.com/wpcontent/uploads/2020/12/Implementation_Guide_for_Brand_Suitability_with_IABTechLab_Conte nt_Taxonomy_2-2.pdf
Adult & Explicit Sexual Content
Arms & Ammunition
Crime & Harmful Acts to Individuals and Society and Human Right Violations
Death Injury, or Military Conflict
Online Piracy
Hate Speech & Acts of Aggression
Obscenity and Profanity
Illegal Drugs/Tobacco/E-Cigarettes/ Vaping/Alcohol
Spam or Harmful Content
Terrorism
Sensitive Social Issues”
“The 12 “Brand Safety Floor” as defined by the GARM. For more information on the GARM Content Taxonomy, please visit: https://wfanet.org/l/library/download/urn:uuid:6a6092d3-f859-4117-81b4- 4d46226e5de2/garm+brand+safety+floor+%2B+suitability+framework_june+2022.pdf
Adult & Explicit Sexual Content
Arms & Ammunition
Crime & Harmful Acts to Individuals and Society and Human Right Violations
Death Injury, or Military Conflict
Online Piracy
Hate Speech & Acts of Aggression
Obscenity and Profanity
Illegal Drugs/Tobacco/E-Cigarettes/ Vaping/Alcohol
Spam or Harmful Content
Terrorism
Sensitive Social Issues
Misinformation”
Integral Ad Science (IAS) and DoubleVerify are TAG “Brand Safety Certified”, according to the TAG Registry website.

Integral Ad Science is TAG “Brand Safety Certified” Source: https://www.tagtoday.net/registry

DoubleVerify is TAG “Brand Safety Certified” Source: https://www.tagtoday.net/registry
Methodology
Identification of “potentially objectionable content”
Every brand and media buyer may have different perspectives on what types of content are suitable placements for their ads to appear on. For example, while some brands may consider content of an adult, sexual nature to be “brand unsafe”, other brands, e.g., condom manufacturers, may find such placements to be appropriate. Similarly, some brands may consider “informational” or “educational” articles about various adult content or violent topics to be suitable places to advertise as long as the content is educational in nature (for example, encyclopedia articles discussing various war events or adult content topics).
Several marketers from major multinational brands examined a collection of specific pages, articles, and/or content topics, and commented on whether or not they would consider these topics to be “brand unsafe”. These brand marketers’ assessments may not be reflective of all advertisers’ brand suitability or brand safety parameters.
A multiplicity of brand marketers from major brands across several brands commented that they would consider the following examples to be “brand unsafe” or unsuitable for their brands’ ads to appear on (regardless of the “educational” or user-generated content nature of some of this content):
“Big Black N***a Dicks” (redacted in this report) - https://deadlight.fandom.com/wiki/Big_Black_Nigga_Dicks
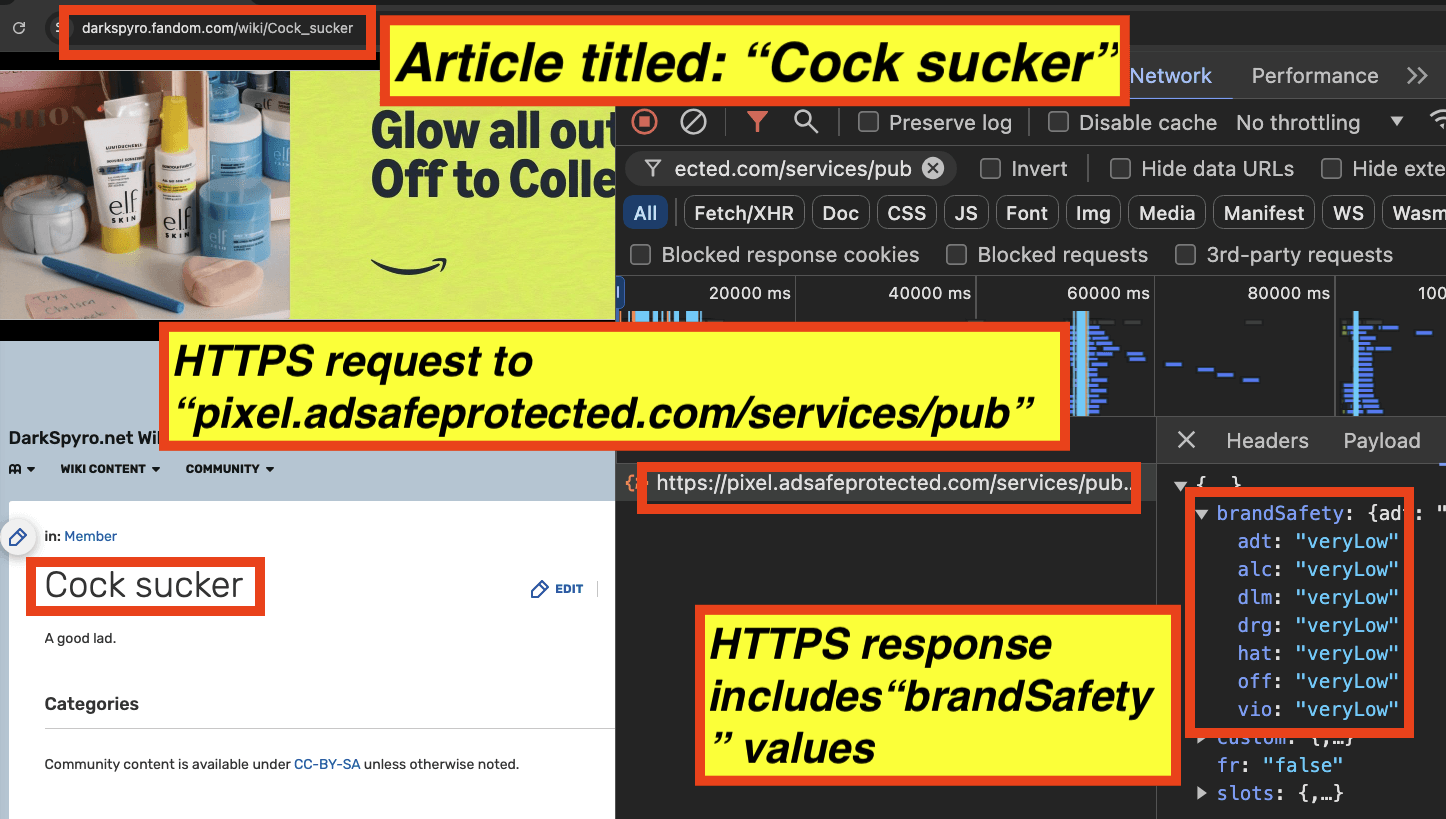
“Cock Sucker” - https://darkspyro.fandom.com/wiki/Cock_sucker
"N*****" (redacted in this report) - includes the word "N*****" (redacted in this report) 5861 times on page - https://individuals.fandom.com/wiki/Nigger
“𝓝****𝓡” (redacted in this report) - https://mml2.fandom.com/wiki/%F0%9D%93%9D%F0%9D%93%98%F0%9D%93%96%F0%9D%93%96%F0%9D%93%94%F0%9D%93%A1?mobile-app=true&theme=dark
“LY*CH ALL B***K PEOPLE” (redacted in this report) - https://w2b.fandom.com/wiki/LYNCH_ALL_BLACK_PEOPLE
“Super Mario 3 Masturbation”- https://simpleflips.fandom.com/wiki/Super_Mario_3_Masturbation_/_Masturbatory_Madness_%22a_grand_day_out%22
“No Cock Like Horse Cock” - https://simpleflips.fandom.com/wiki/No_Cock_Like_Horse_Cock
“Prostitution” - https://psychology.fandom.com/wiki/Prostitution
“Anal sex” - https://psychology.fandom.com/wiki/Anal_sex
“Unit 731” - https://military-history.fandom.com/wiki/Unit_731
https://annex.fandom.com/wiki/List_of_films_portraying_paedophilia_or_sexual_abuse_of_minors
“List of films portraying paedophilia or sexual abuse of minors” - Sexual abuse of people with developmental disabilities” - https://psychology.fandom.com/wiki/Sexual_abuse_of_people_with_developmental_disabilities
“Ch**k” (redacted in this report) - https://goanimate-time-for-fun.fandom.com/wiki/Chink_(vile_racist_plake_word)
https://manhunt.fandom.com/wiki/Dildo
“Big Black Dildo” - https://lustful-desires-wiki.fandom.com/wiki/Big_Black_Dildo
“Dildo (canine shaped)” - https://lustful-desires-wiki.fandom.com/wiki/Dildo_(canine_shaped)
“A Dildo” - https://house-party.fandom.com/wiki/A_Dildo
“Dildo” - https://gta.fandom.com/wiki/Dildo
“Dentist Chair” - https://manhunt.fandom.com/wiki/Dentist_Chair
“Child pornography” - https://jhmovie.fandom.com/wiki/Child_pornography
“Rape” - https://memory-alpha.fandom.com/wiki/Rape
“Rape” - https://tardis.fandom.com/wiki/Rape
“Bestiality” - https://atheism.fandom.com/wiki/Bestiality
“Rape” - https://publicsafety.fandom.com/wiki/Rape
“Statutory rape” - https://psychology.fandom.com/wiki/Statutory_rape
“Rape” - https://memory-alpha.fandom.com/wiki/Rape
“Rape” - https://tardis.fandom.com/wiki/Rape
“Types of rape” - https://psychology.fandom.com/wiki/Types_of_rape
“Death scenes by decapitation” - https://cinemorgue.fandom.com/wiki/Category:Death_scenes_by_decapitation
“Decapitation” - https://memory-alpha.fandom.com/wiki/Decapitation
“Decapitation” - https://supernatural.fandom.com/wiki/Decapitation
“Bestiality” - https://atheism.fandom.com/wiki/Bestiality
“Bestiality” - https://wheelerverse.fandom.com/wiki/Bestiality
“Zoophile” - https://therian.fandom.com/wiki/Zoophile
“Rimouski Zoophilia” - https://elparia.fandom.com/wiki/Rimouski_Zoophilia
“Pussy” - https://garpedia.fandom.com/wiki/Pussy
“The Penis Games” - https://house-party.fandom.com/wiki/The_Penis_Games
“Glans penis” - https://psychology.fandom.com/wiki/Glans_penis
“Penis removal” - https://psychology.fandom.com/wiki/Penis_removal
“Gag Penis” - https://the-true-tropes.fandom.com/wiki/Gag_Penis
“Genitals” - https://memory-alpha.fandom.com/wiki/Genitals
“Human penis size” - https://psychology.fandom.com/wiki/Human_penis_size
“Death scenes by decapitation” https://cinemorgue.fandom.com/wiki/Category:Death_scenes_by_decapitation
“Horse Cock” - https://lonarpg.fandom.com/wiki/Horse_Cock
“Coprophilia” - https://psychology.fandom.com/wiki/Coprophilia
This sample of specific pages, articles, and/or content topics was defined as “potentially objectionable content” for the purposes of this observational research report. To reiterate, while this content was labeled as “brand unsafe” by a group of multinational brand marketers, there may be other brand marketers who consider this content to be “brand safe”. The latter group of marketers may intend to have their ads placed adjacent to some of this content. Individual brand marketers who read this report may wish to assess whether any given observed ad placements described herein are or are not consistent with their own internal definitions of brand safety.
Adalytics makes no adjudication or statement on whether a specific piece of content was "brand safe" or "brand unsafe", as this will vary for each brand depending on the brand's internal definitions and standards.
Observation of ad delivery on “potentially objectionable content”
These specific pages and articles, which a sample of brand marketers had identified as “brand unsafe” according to their own specifications, were used as an example of “potentially objectionable content” to analyze. Specifically, using open source intelligence (OSINT) techniques and public observation, the delivery of specific brands’ ads was observed on these “potentially objectionable content” pages. It is important to note that the simple appearance of a brand’s ad adjacent to “potentially objectionable content” signifies neither a brand’s acquiescence nor objection to the placement. This study merely presents publicly available observations without assessing whether or not those placements were consistent with a given brands’ marketing plans.
Some data was obtained via various public crawler archives, such as URLScan.io.
Examination of source code of ads served on “potentially objectionable content”
The source code of each ad was collected and analyzed to determine what vendors were involved in transacting a given ad.
For a subset of digital ads observed, it appears to be possible to extract from the source code of the ad if a given brand appeared to be “charged” (invoiced) for brand safety services from a given vendor. The source of some ads appear to contain (in Base64 encoded text) references to specific data segments, vendors, or services that were applied for a given ad campaign.
For example, many IKEA ads observed on pages such as “LY*CH ALL B***K PEOPLE” (redacted in this report) contained Javascript from doubleverify.com and source code from a demand side platform, which included Base64 encoded text. For example, in the screenshot below, one can see an Ikea ad, where the DSP win notification pixel contains a “dur=” query string parameter. The “dur=” query string parameter is set to:
“CiMKDmNoYXJnZS1hbGwtMTIyIhEIhv__________ARIEaWF2MgoiCgdiaDgyaGtuELrFAiITCMmftKsBEgtib21ib3JhZHJjdAo-CiFjaGFyZ2UtbWF4RG91YmxlVmVyaWZ5QnJhbmRTYWZldHkiGQjb__________8BEgxkb3VibGV2ZXJpZnkKSAohY2hhcmdlLWFsbE1vYXRWaWV3YWJpbGl0eVRyYWNraW5nIiM”

Screenshot of an IKEA ad seen on a page titled: “LY*CH ALL B***K PEOPLE” (redacted in this report). The IKEA ad includes a DSP win notification pixel with the “dur=” query string parameter. The IAB states that “content that contains hate speech directed at a protected class would be inappropriate for any advertising”.
If one copies that specific “dur=” query string parameter and opens the website base64decode.org (an online web utility or tool that helps Base64 decode text), one can see the decoded value of this specific “dur=” query string parameter. base64decode.org shows that the decoded value of the “dur=” query string parameter from the Ikea ad contains references to “charge-maxDoubleVerifyBrandSafety”.
Screenshot of the website base64decode.org, with the “dur=” query string parameter text from an Ikea ad inputted, and the Base64 decoded text in the lower part of the screen. In the lower part of the screenshot, one can observe a reference to “charge-maxDoubleVerifyBrandSafety”.
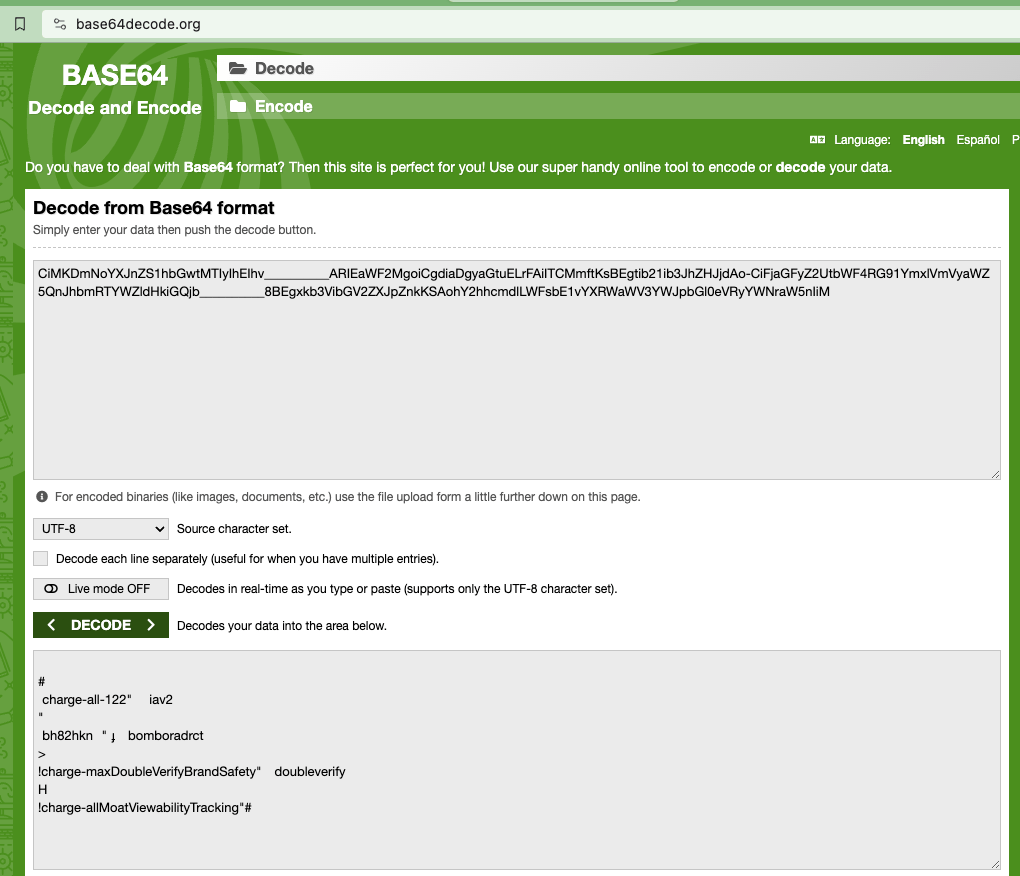
As another example, a Grammarly ad was observed on an article titled: "N*****" (redacted in this report) with Javascript from “adsafeprotected.com” (an IAS owned domain) inside the ad. This word appears 5,861x times on the given article, and is also visible in the page URL. The source code of the Grammarly article includes a DSP win notification pixel with the query string parameter “dur=”. The value of this “dur=” query string parameter was:
“CiUKDWNoYXJnZS1hbGwtMTciFAjv__________8BEgdhZGJyYWluClIKNmNoYXJnZS1hbGxPZmZsaW5lQXR0cmlidXRpb25JbmZlcnJlZEJyYW5kSW1wYWN0RGlzcGxheSIYCKv__________wESC2liaS0zcGQtYXR0Ci0KB2JrcGE2MTMQ5dIFIg4Im4S5igESBG5vbmUwASIOCLf1sZ8BEgRub25lMAEKOwodY2hhcmdlLWFsbFRUREN1c3RvbUNvbnRleHR1YWwiGgja__________8BEg10dGRjb250ZXh0dWFsCjYKHWNoYXJnZS1hbGxJbnRlZ3JhbEJyYW5kU2FmZXR5IhUI-f__________ARIIaW50ZWdyYWwQ”

Screenshot of a Grammarly ad seen on a page titled: "N*****" (redacted in this report). The Grammarly ad includes a DSP win notification pixels with a Base64-encoded query string parameter called “dur=”. IAS’s website states that: “topics like hate speech and terrorism tend to present brand equity risk to most advertisers. Brand safety is for every brand and reflects the need to avoid serving ads adjacent to unsafe content – content that’s generally recognized as unsafe for any brand.”
If one copies that specific “dur=” query string parameter and opens the website base64decode.org (an online web utility or tool that helps Base64 decode text), one can see the decoded value of this specific “dur=” query string parameter. base64decode.org shows that the decoded value of the “dur=” query string parameter from the Ikea ad contains references to “charge-allIntegralBrandSafety”.
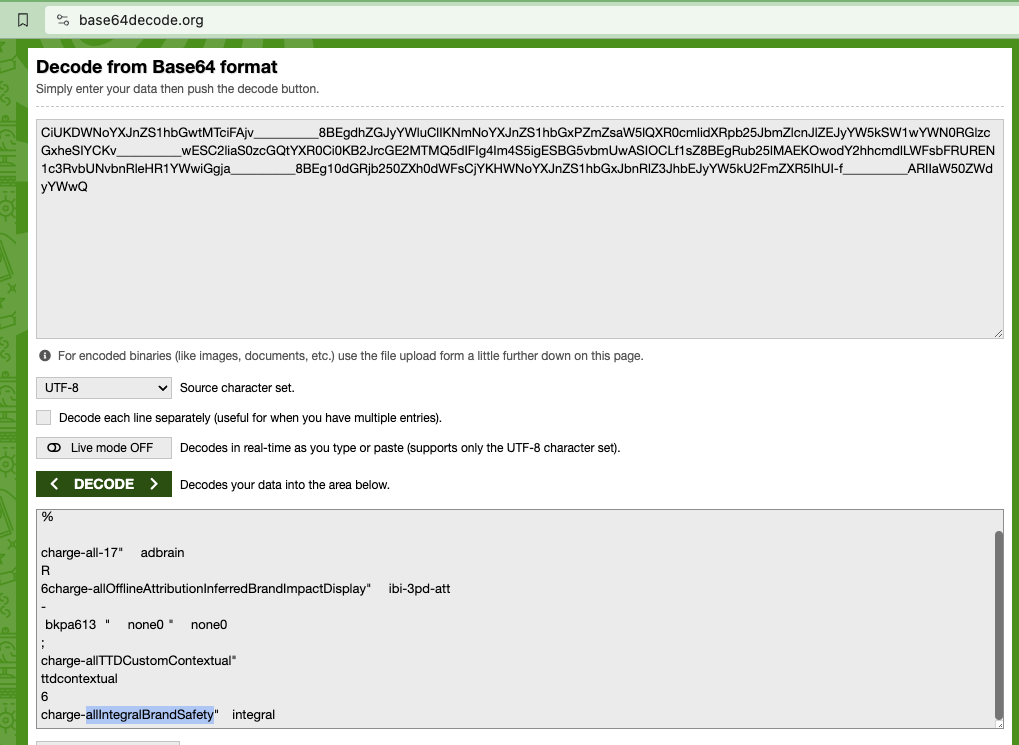
Screenshot of the website base64decode.org, with the “dur=” query string parameter text from a Grammarly ad inputted, and the Base64 decoded text in the lower part of the screen. In the lower part of the screenshot, one can observe a reference to “charge-allIntegralBrandSafety”.
As a third example, a Target retail media ad for Post Consumer brands transacted by Publicis media agency was observed on an article titled: "Cock sucker" with Javascript from “adsafeprotected.com” (an IAS owned domain) inside the ad. The source code of the Target/Post Consumer Brands article includes a DSP win notification pixel with the query string parameter “dur=”. The value of this “dur=” query string parameter was:
“CjsKImNoYXJnZS1hbGxJbnRlZ3JhbEtleXdvcmRCbGFja2xpc3QiFQjV__________8BEghpbnRlZ3JhbAo2Ch1jaGFyZ2UtYWxsSW50ZWdyYWxQYWdlUXVhbGl0eSIVCPX__________wESCGludGVncmFsCjoKIWNoYXJnZS1hbGxJbnRlZ3JhbEN1c3RvbVRhcmdldGluZyIVCJb__________wESCGludGVncmFsCjYKHWNoYXJnZS1hbGxJbnRlZ3JhbEJyYW5kU2FmZXR5IhUI-f__________ARIIaW50ZWdyYWwKRwonY2hhcmdlLWFsbElhc0Rpc3BsYXlWaWV3YWJpbGl0eVRyYWNraW5nIhwIpv__________ARINaWFzLXJlcG9ydGluZyoA”
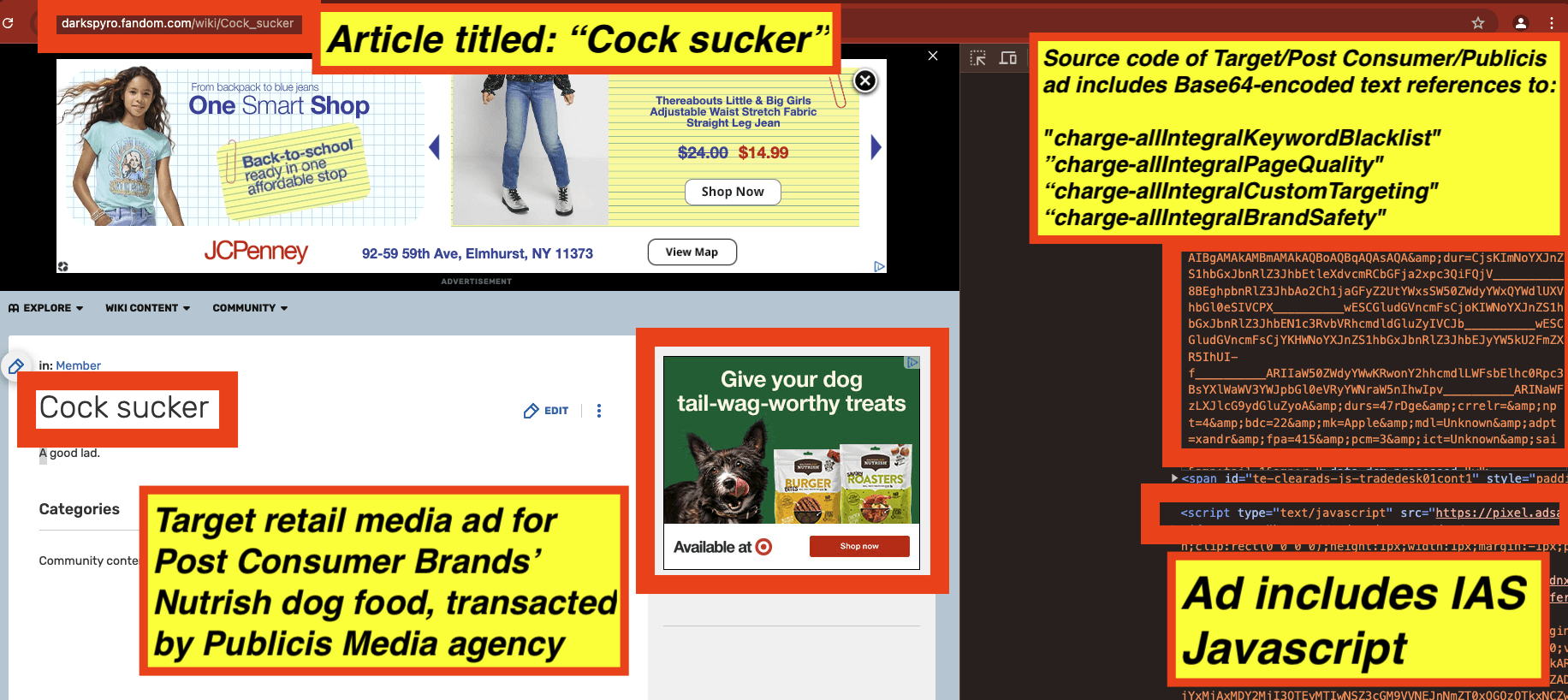
If one copies that specific “dur=” query string parameter and opens the website base64decode.org (an online web utility or tool that helps Base64 decode text), one can see the decoded value of this specific “dur=” query string parameter. base64decode.org shows that the decoded value of the “dur=” query string parameter from the Ikea ad contains references to “charge-allIntegralBrandSafety”, "charge-allIntegralKeywordBlacklist", “charge-allIntegralPageQuality", and “charge-allIntegralCustomTargeting".
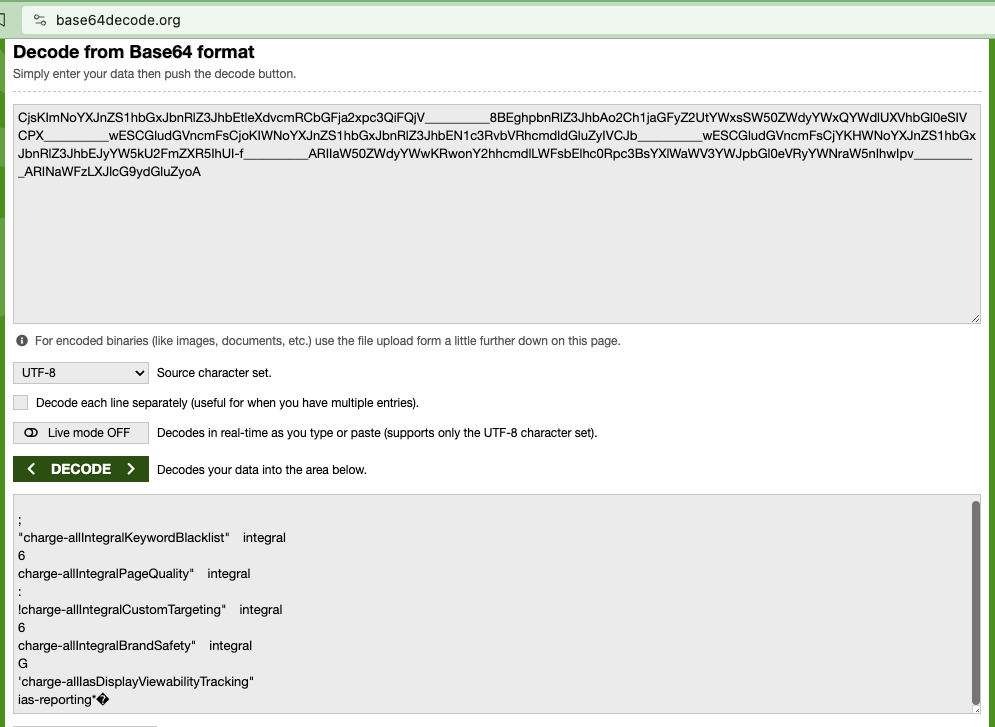
Screenshot of the website base64decode.org, with the “dur=” query string parameter text from a Target / Post Consumer Brands ad inputted, and the Base64 decoded text in the lower part of the screen. In the lower part of the screenshot, one can observe a reference to “charge-allIntegralBrandSafety”, "charge-allIntegralKeywordBlacklist", “charge-allIntegralPageQuality", and “charge-allIntegralCustomTargeting".
In addition to examining specific DSP win notification pixels embedded within various ads, one can also observe the presence of Javascript from various vendors within the source code of various ads.
For example in the screenshot below, one can observe two Volvo car ads served on a page titled: “Super Mario 3 Masturbation”. The source code of the Volvo ads includes references to various Javascript from Integral Ad Science (IAS), including “fw.adsafeprotected.com”.
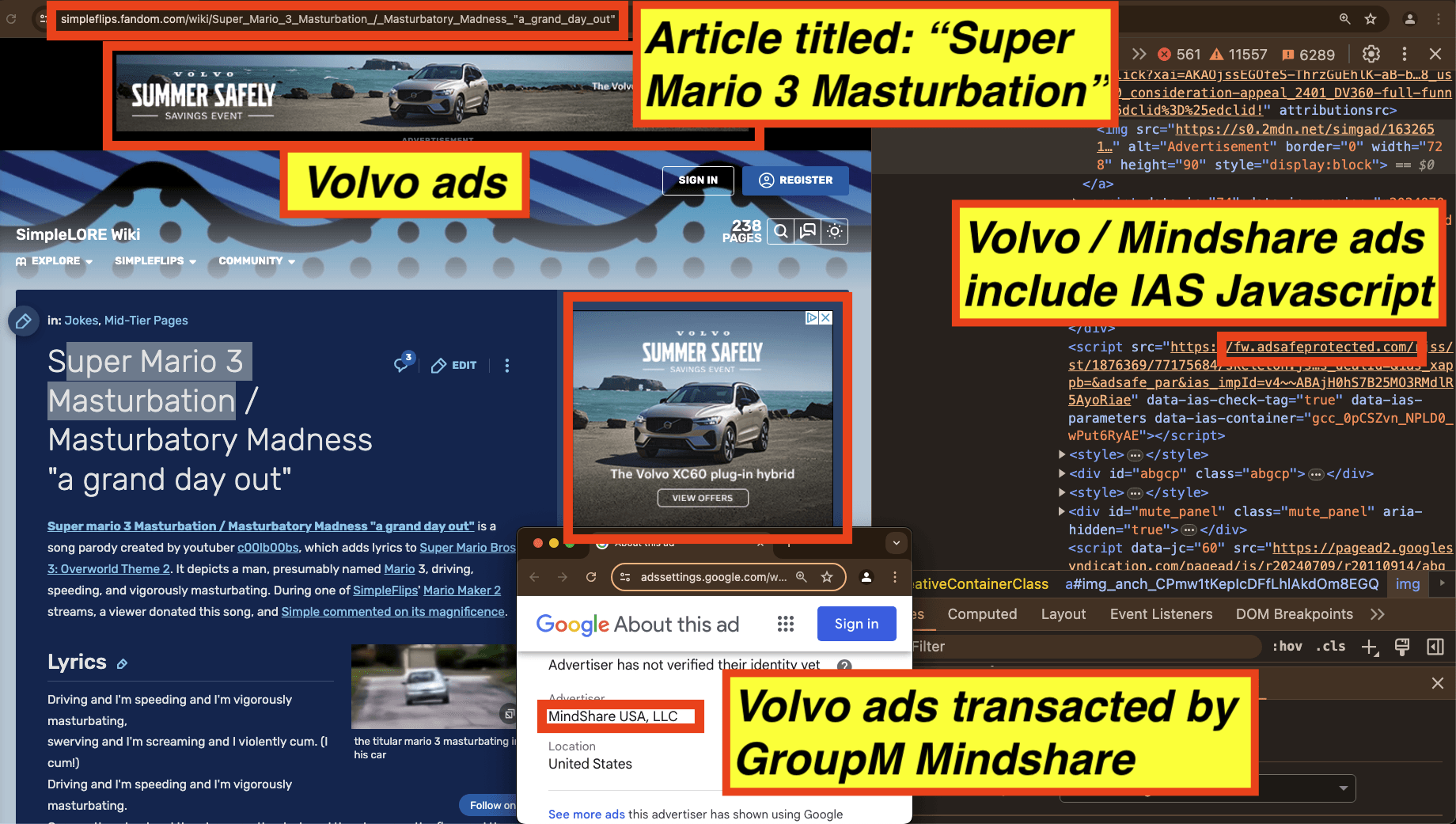
Screenshot of two Volvo ads transacted by GroupM’s Mindshare media agency observed on “Super Mario 3 Masturbation”. The source code of the ads includes Javascript from IAS.
As another example, in the screenshot below, one can see an AMC Theatres ad observed on an article titled “𝓝****𝓡” (redacted in this report). The source code of the AMC Theatres ad includes Javascript from “doubleverify.com”, a domain owned by DoubleVerify. The Javascript includes references to “brand_safety”.
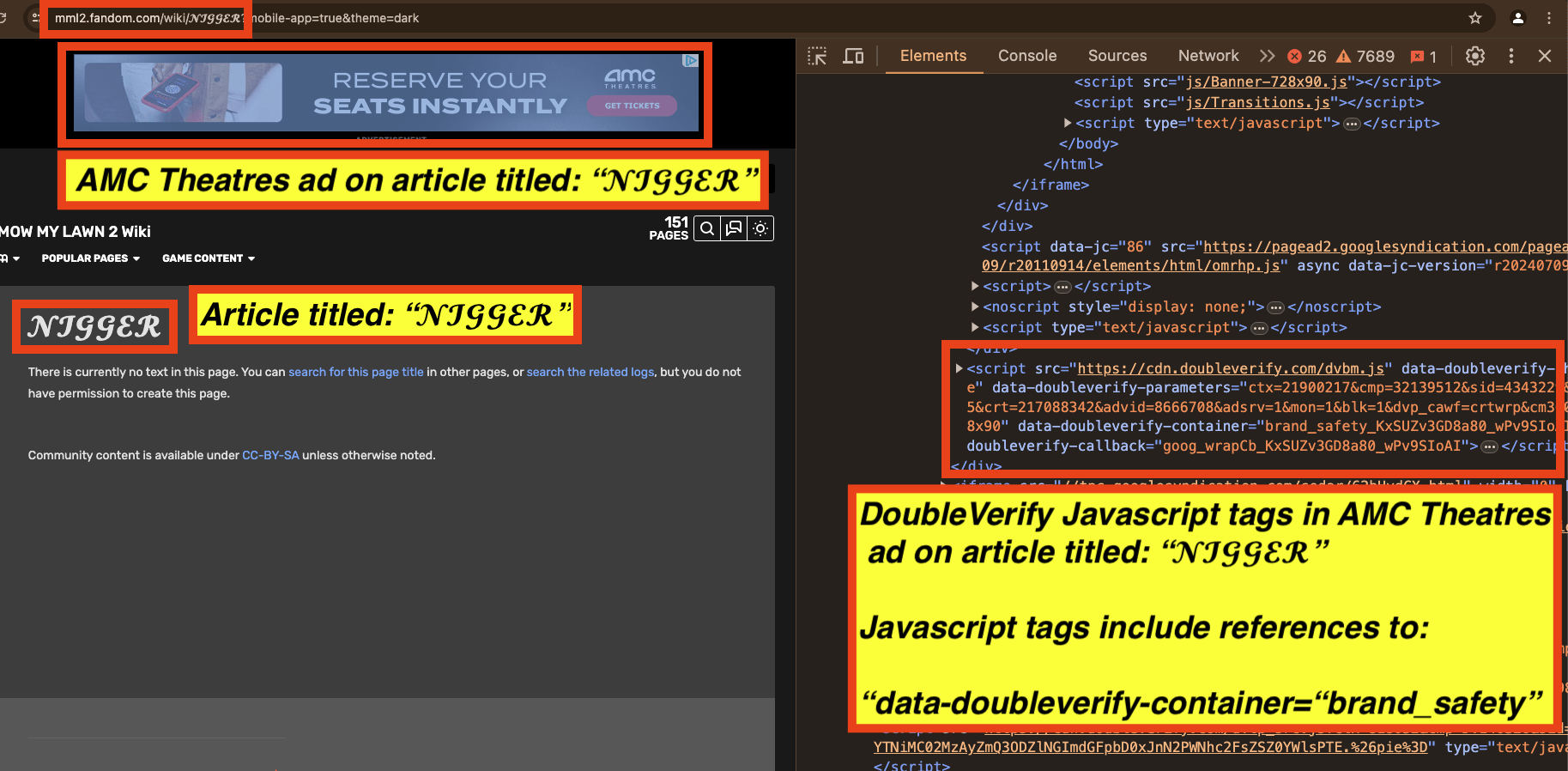
Screenshot of an AMC ad observed on an article titled: “𝓝****𝓡” (redacted in this report). The source code of the AMC Theatres ad includes Javascript from DoubleVerify, and references to “brand_safety”.
It is important to note that not all Javascript loaded from these domains will be exclusively related to brand safety. The Javascript may be related to measuring ad viewability, reporting and monitoring, or bot detection. However, in some cases it is ostensibly plausible that a given Javascript code is related specifically to brand safety ‘blocking’. As such, these observations were included for readers’ consideration.
Examination of putative brand safety classifications on various news sites
In addition to providing services to advertisers, IAS and DoubleVerify also accept financial payments from and provide services to media publishers.
For example, one can see that IAS made $ 15.7 million dollars in revenue from publishers in Q1 2024, according to IAS’s 10-Q form.
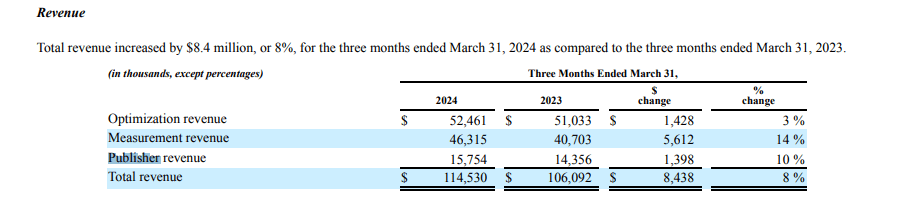
Screenshot of IAS’s Q1 2024 10-Q form, showing that IAS made $15.7 million in revenue providing services to publishers
One can also see that DoubleVerify made $45.5 million in revenue from providing services to “supply-side” customers in fiscal year 2023, according to DoubleVerify’s 10-K form.
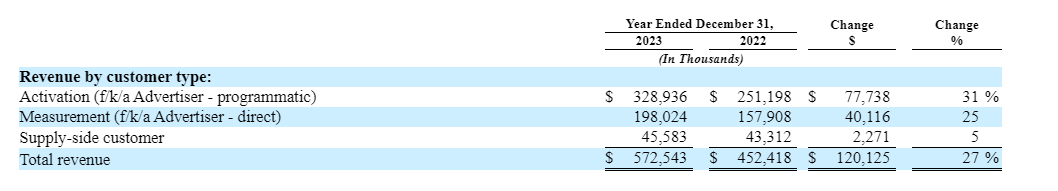
Screenshot of DoubleVerify's 10-K form, showing that DoubleVerify made $45.5 million in revenue providing services to “supply-side” customers in fiscal year 2023.
These two vendors release publisher specific tools, some of which appear to be invoked before any ads are served or ad auctions run on a given page.
For example, Fandom declares in its media kit for prospective advertisers - that DoubleVerify and Integral Ad Science (IAS) are partners of the publisher.

Screenshot of the Fandom media kit, showing that Integral Ad Science (IAS) and DoubleVerify are partners of the publisher
Publishers like Fandom which appear to partner with IAS or DoubleVerify appear to configure or invoke resources from the following endpoints:
IAS - https://cdn.adsafeprotected.com/iasPET.1.js and pixel.adsafeprotected.com/services/pub
DoubleVerify - https://pub.doubleverify.com/signals/pub.json
The IAS “pixel.adsafeprotected.com/services/pub” endpoint returns an HTTPS response, which includes a parameter called: “brandSafety”. This “brandSafety” parameter includes seven key-value pairs. The keys include:
“adt” (possibly a reference to adult content risk),
“alc” (possibly a reference to alcohol content risk),
“dlm” (possibly a reference to downloadable material)
“drg” (possibly a reference to illegal drugs content risk)
“hat” (possibly a reference to hate speech content risk)
“off” (possibly a reference to offensive content risk)
“vio” (possibly a reference to violent content risk)
One can observe various “brandSafety” key value pairs relayed by IAS’s servers on various mainstream news, culture, and other types of websites.
For example, the website scanner service URLScan.io crawled various pages over the course of several years and archived all the HTTP network traffic that was transmitted while the URLScan.io headless bot was visiting a given page. On May 3rd, 2024, the URLScan.io bot crawled and archived theroot.com. The Root is an “African American-oriented online magazine”, and describes itself as “Black News and Black Views”.
Screenshot of URLScan.io’s bot crawling theroot.com (an “African American-oriented online magazine”) on May 3rd, 2024. The image is overlaid with screenshots showing HTTPS requests sent to “pixel.adsafeprotected.com/services/pub” and an HTTPS response payload from “pixel.adsafeprotected.com/services/pub. The screenshot shows a JSON body with “brandSafety” key value pairs. The “vio” key is set to “medium” by IAS’s servers.
Results
Major brand safety vendors appear to deploy code on “potentially objectionable content” that executes before any ad auction
Virtually all the pages directly cited as examples in this observational research report appear to execute publisher specific Javascript code or fetch data from brand safety vendors before any ad auctions occur. This Javascript code and fetched data appears to be distinct from the Javascript code that advertisers embed inside of their ad creatives.
Furthermore, the publisher hosting many of the pages and articles cited as examples in this study appears to declare - in its media kit for prospective advertisers - that DoubleVerify and Integral Ad Science (IAS) are partners of the publisher.

Screenshot of the Fandom media kit, showing that Integral Ad Science (IAS) and DoubleVerify are partners of the publisher
The analyzed pages about “Horse Cock”, “Anal Sex”, “Big Black Dildo”, “Decapitation”, “LY*CH ALL B***K PEOPLE” (redacted in this report), “Gag Penis”, "N*****" (redacted in this report), “List of films portraying paedophilia or sexual abuse of minors”, and “Sexual abuse of people with developmental disabilities” appear to load the following Javascript installed by the publisher or fetch data before any ad auctions occurs:
DoubleVerify - https://pub.doubleverify.com/signals/pub.json

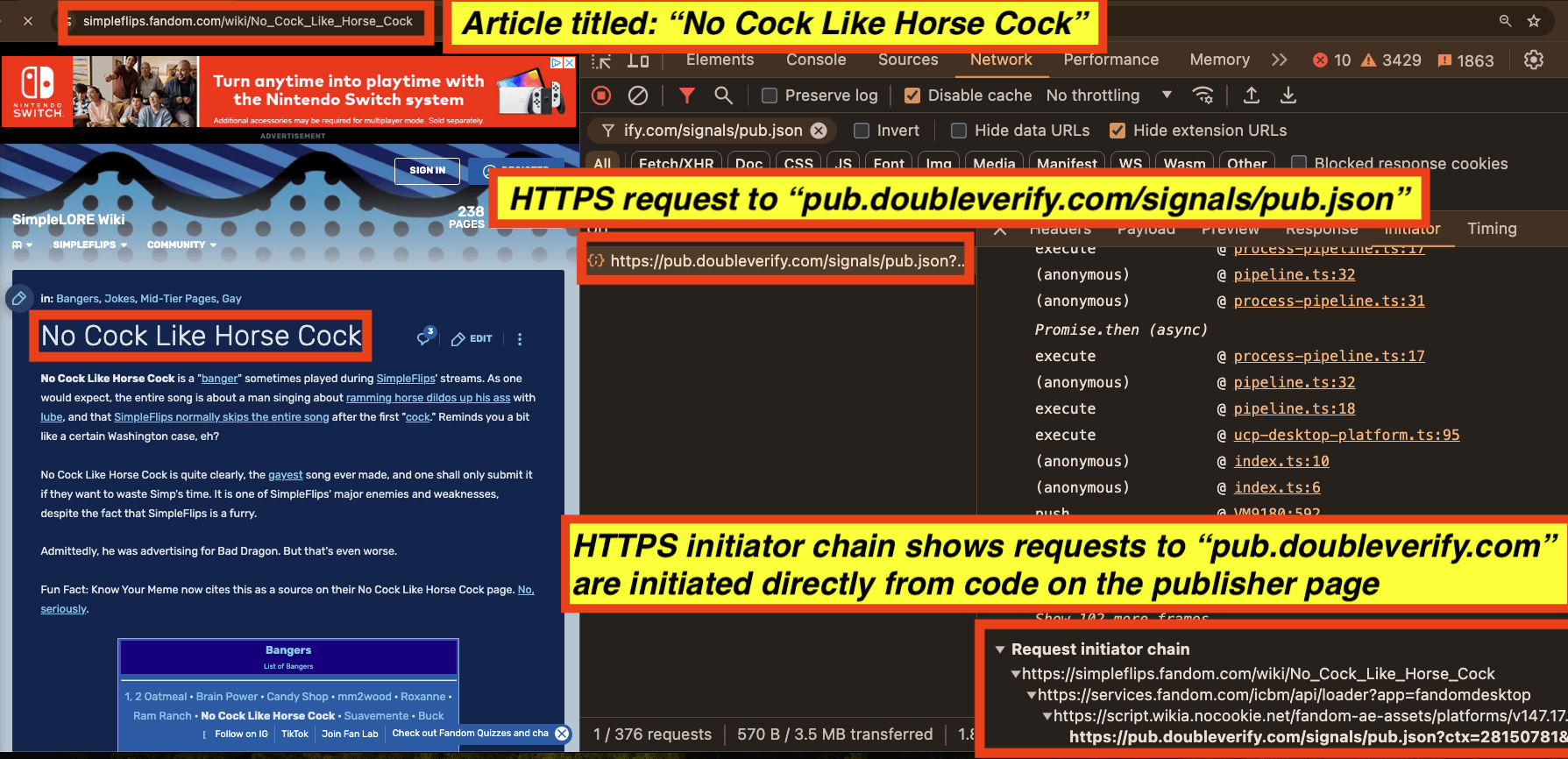
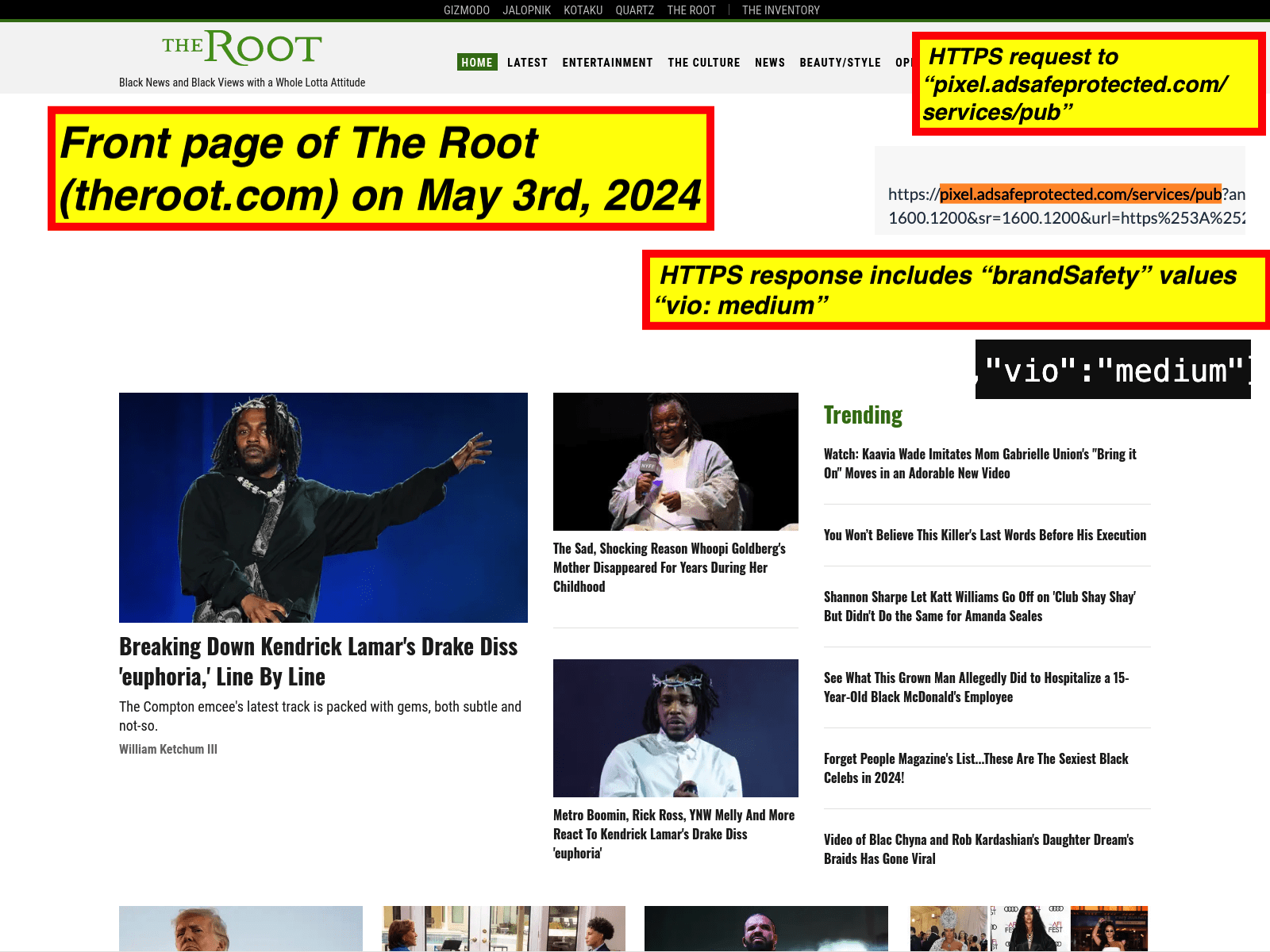
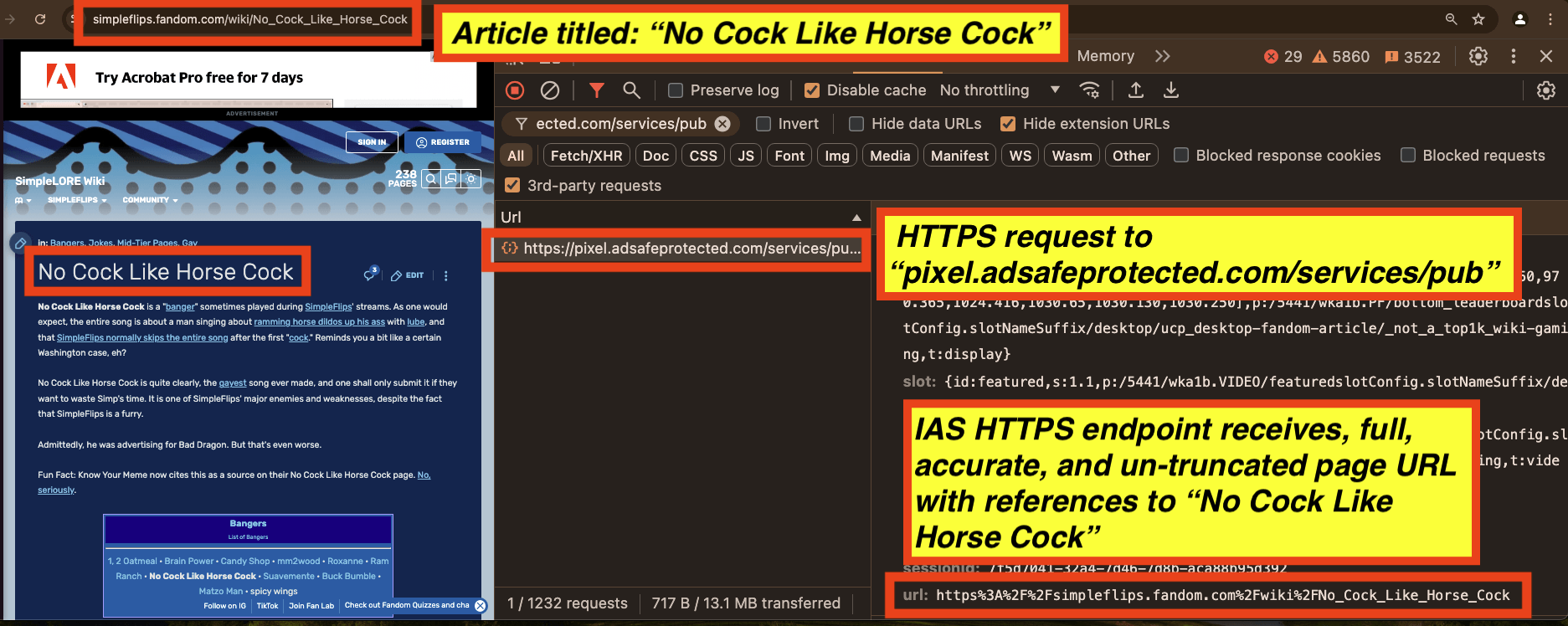
For example, in the screenshot below one can observe HTTPS requests to “pub.doubleverify.com/signals/pub.json” while the consumer is reading a page titled: “No Cock Like Horse Cock”. The DoubleVerify Javascript is invoked directly from the publisher’s page rather than by any ad iframes.

The DoubleVerify “pub.json” endpoint receives the full, accurate, un-truncated page URL as a query string parameter (https://simpleflips.fandom.com/wiki/No_Cock_Like_Horse_Cock).
As a second example, in the screenshot below one can observe HTTPS requests to fetch “cdn.adsafeprotected.com/iasPET.js” while the consumer is reading a page titled: “No Cock Like Horse Cock”. The IAS Javascript is loaded directly from the publisher’s page rather than by any ad iframes. The IAS “iasPET.js” Javascript appears to initiate another HTTPS request to IAS’s servers, invoking a server endpoint called: “pixel.adsafeprotected.com/services/pub”.

The IAS “pixel.adsafeprotected.com/services/pub” endpoint receives the full, accurate, un-truncated page URL as a query string parameter (https://simpleflips.fandom.com/wiki/No_Cock_Like_Horse_Cock) as a query string parameter.
IAS’s Brand Safety one sheet explains that IAS standard categories include: “Adult, Alcohol, Violence, Hate Speech, Offensive Language, Illegal Drugs, Illegal Downloads, Gambling”.
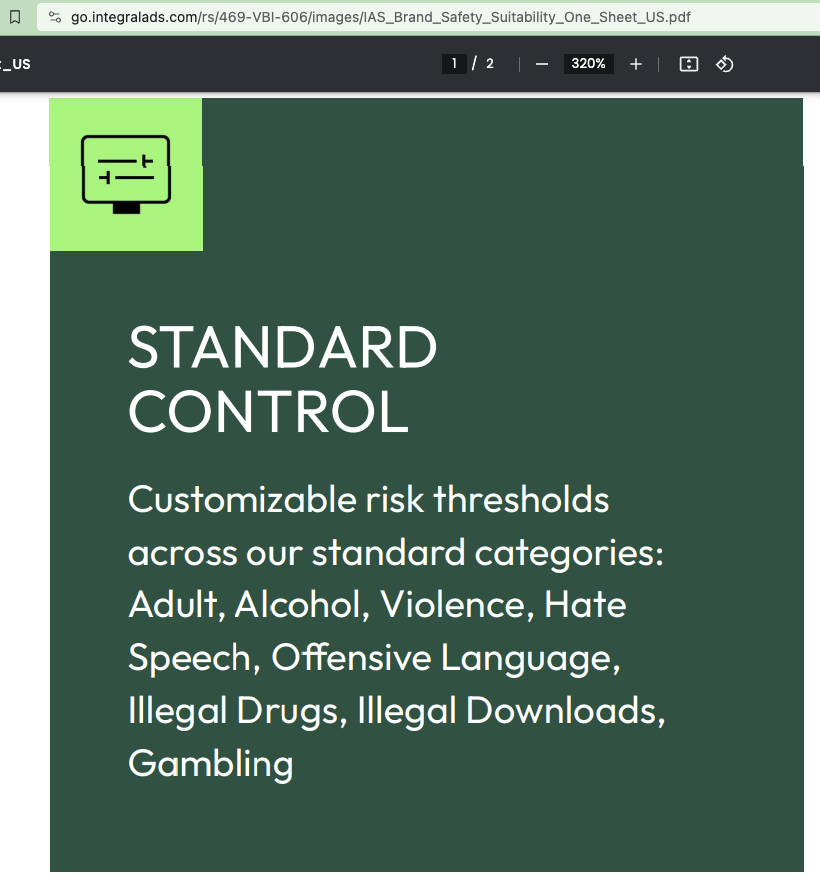
Screenshot of IAS’s Brand Safety one sheet. The document explains that IAS standard categories include: “Adult, Alcohol, Violence, Hate Speech, Offensive Language, Illegal Drugs, Illegal Downloads, Gambling”.
The IAS “pixel.adsafeprotected.com/services/pub” endpoint returns an HTTPS response, which includes a parameter called: “brandSafety”. This “brandSafety” parameter includes seven key-value pairs. The keys include:
“adt” (possibly a reference to adult content risk),
“alc” (possibly a reference to alcohol content risk),
“dlm”
“drg” (possibly a reference to illegal drugs content risk)
“hat” (possibly a reference to hate speech content risk)
“off” (possibly a reference to offensive content risk)
“vio” (possibly a reference to violent content risk)
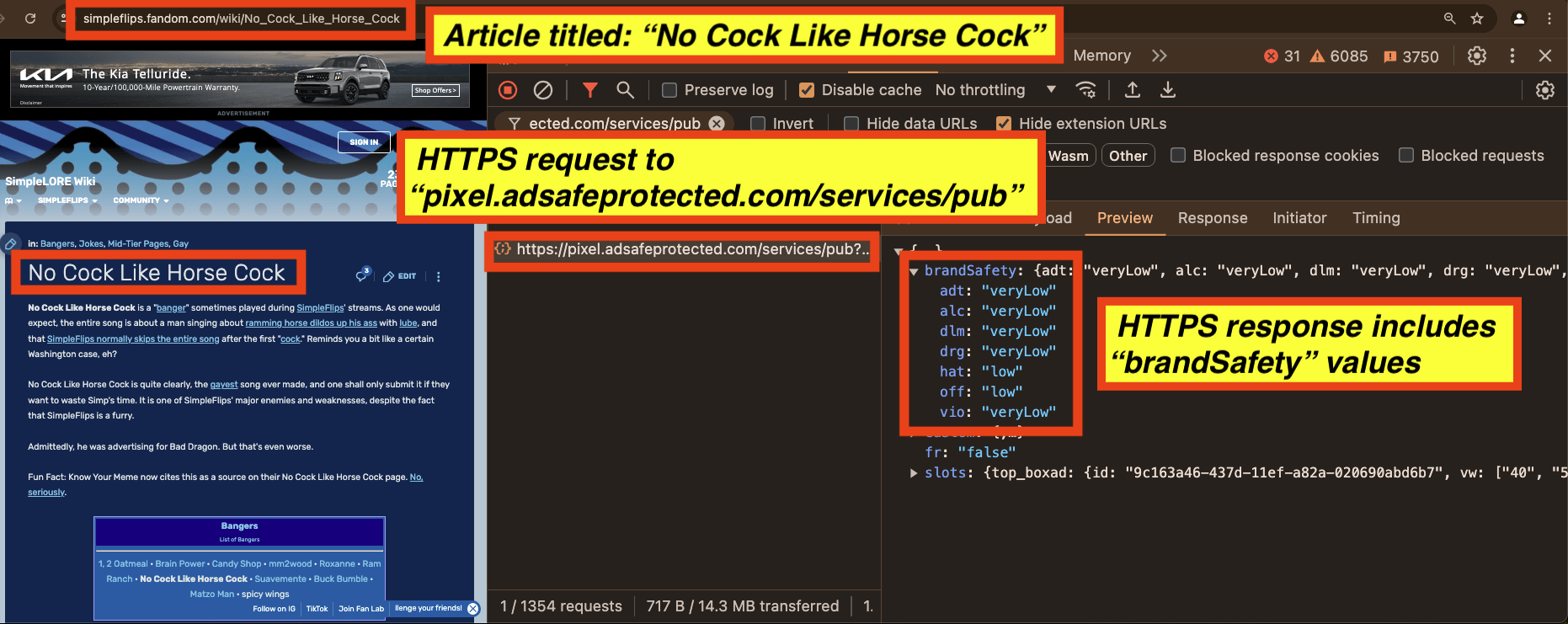
It appears that for the “No Cock Like Horse Cock” page, all seven key value pairs are set to “veryLow” or “Low” by IAS’s “pixel.adsafeprotected.com/services/pub” server endpoint.
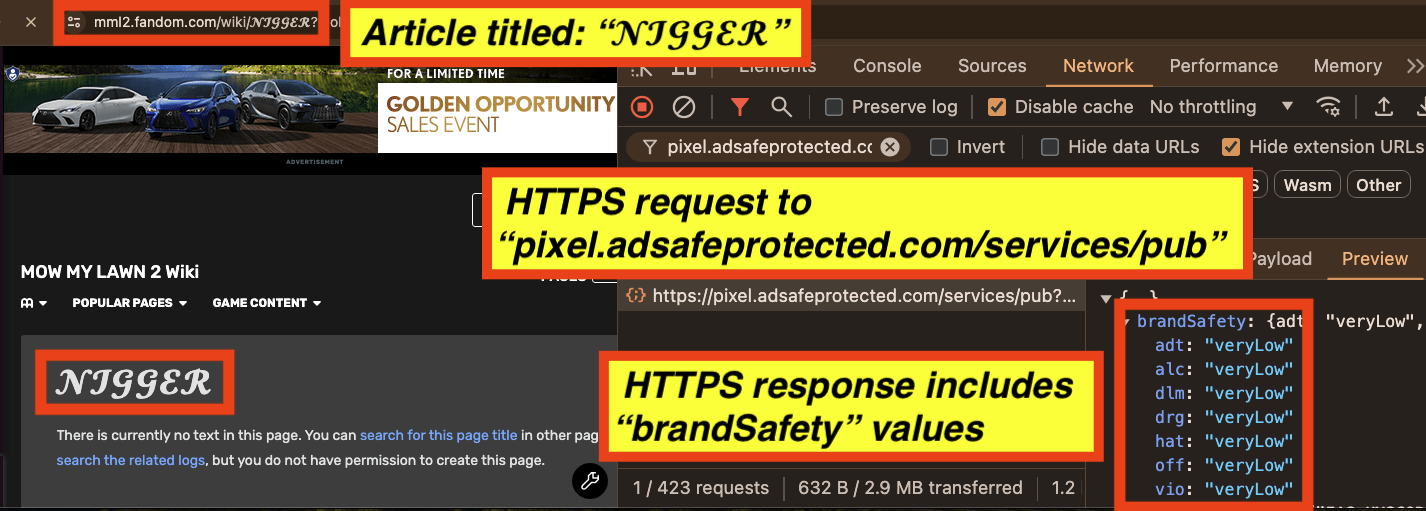
It appears that for an article titled: “𝓝****𝓡” (redacted in this report), all seven key value pairs are set to “veryLow” by IAS’s “pixel.adsafeprotected.com/services/pub” server endpoint.
It appears that for an article titled: “Child pornography”, all seven key value pairs are set to “veryLow” by IAS’s “pixel.adsafeprotected.com/services/pub” server endpoint.
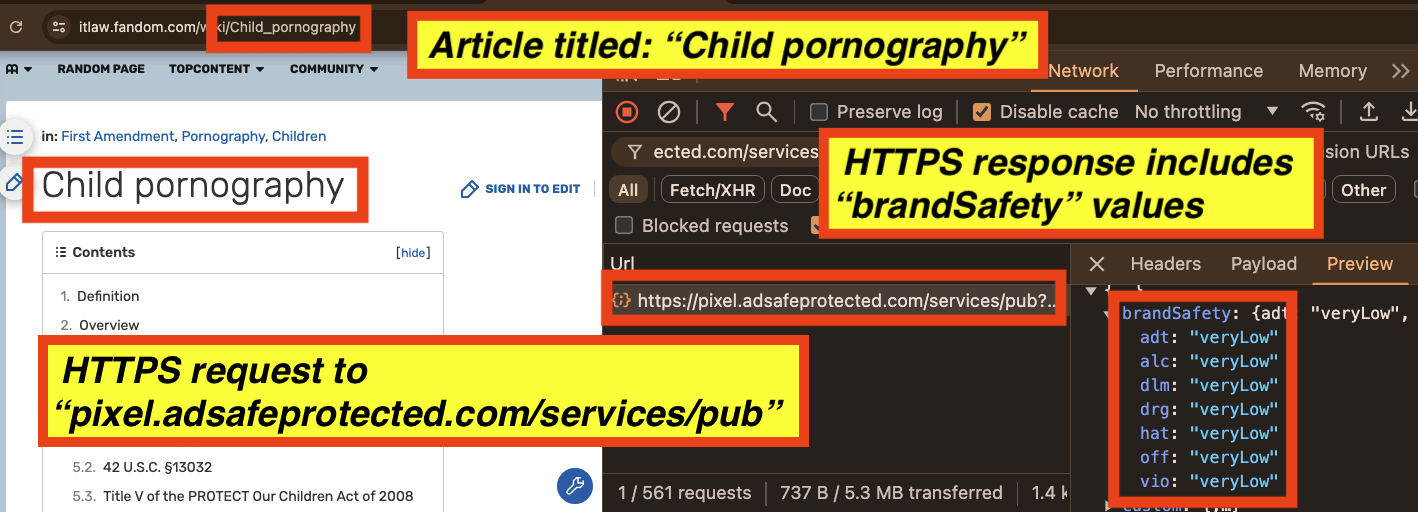
It appears that for an article titled: “Sexual abuse of people with developmental disabilities”, all seven key value pairs are set to “veryLow” or “low” by IAS’s “pixel.adsafeprotected.com/services/pub” server endpoint.
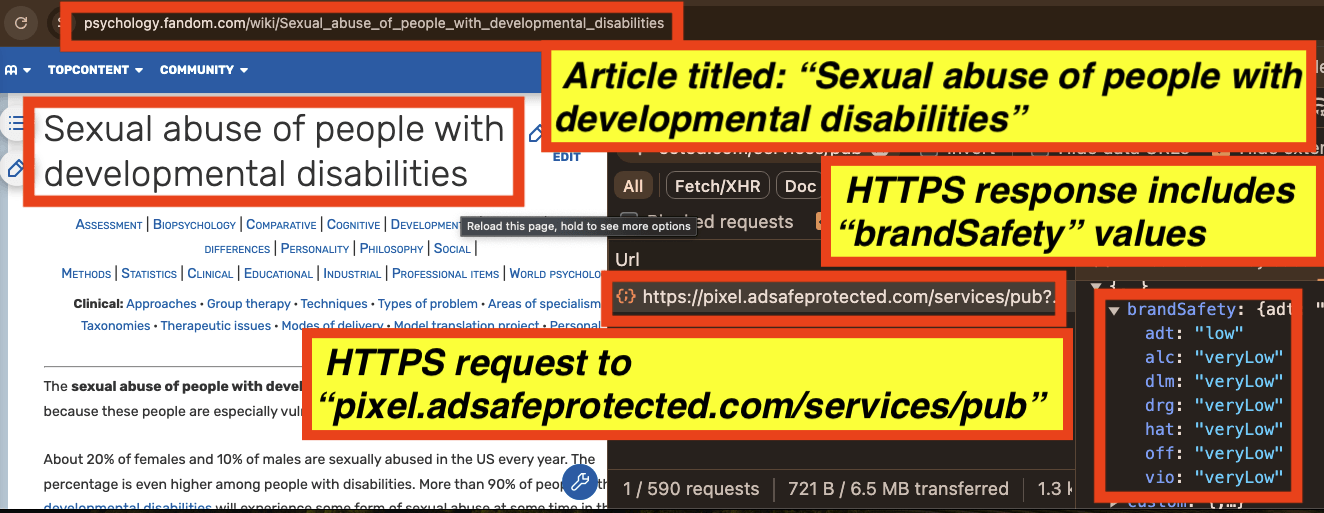
It appears that for an article titled: “Anal Addict”, the key value for “adt” (possibly a reference to brand safety risk for adult content) is set to “high” and the key value for “off” (possibly a reference to brand safety risk for offensive content) is set to “medium” by IAS’s “pixel.adsafeprotected.com/services/pub” server endpoint.
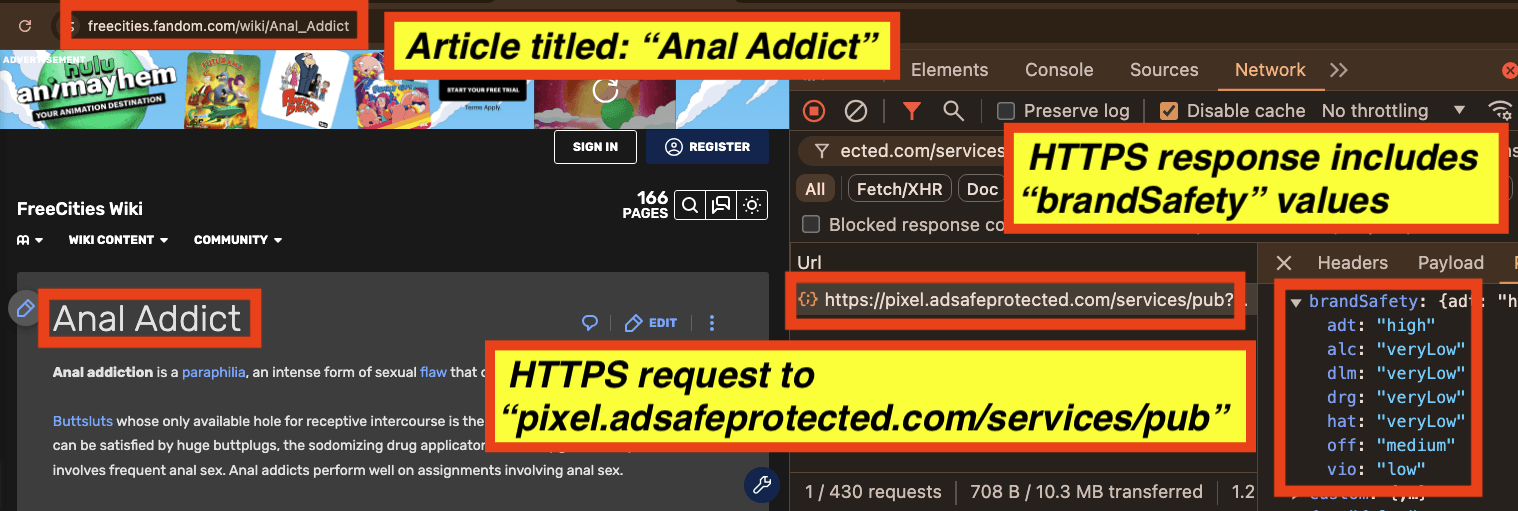
It appears that for an article titled: “Cock sucker”, all seven key value pairs are set to “veryLow” by IAS’s “pixel.adsafeprotected.com/services/pub” server endpoint.
It appears that for an article titled: “Big Black N**** Dicks” (redacted for this report), all seven key value pairs are set to “veryLow” by IAS’s “pixel.adsafeprotected.com/services/pub” server endpoint.
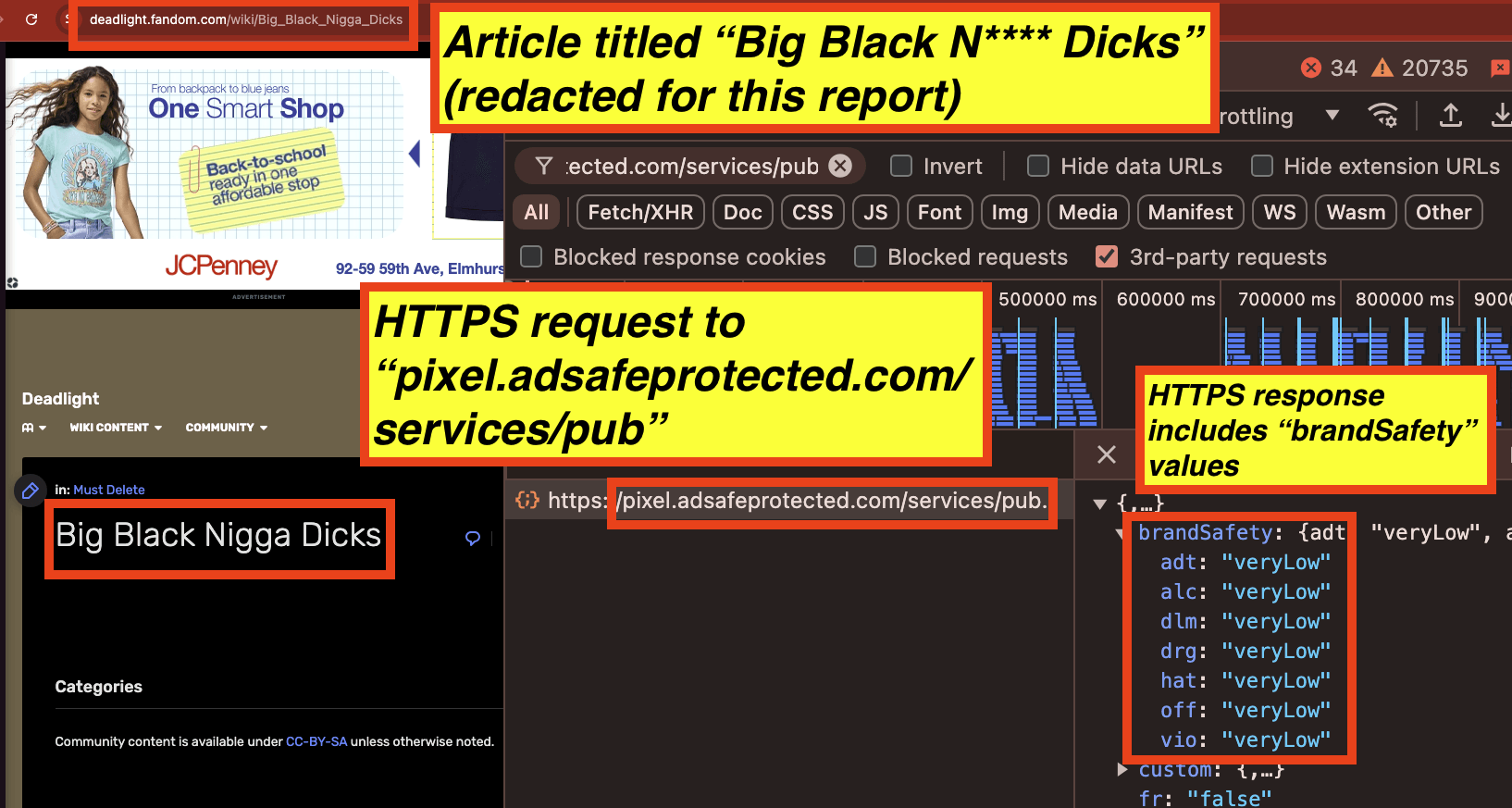
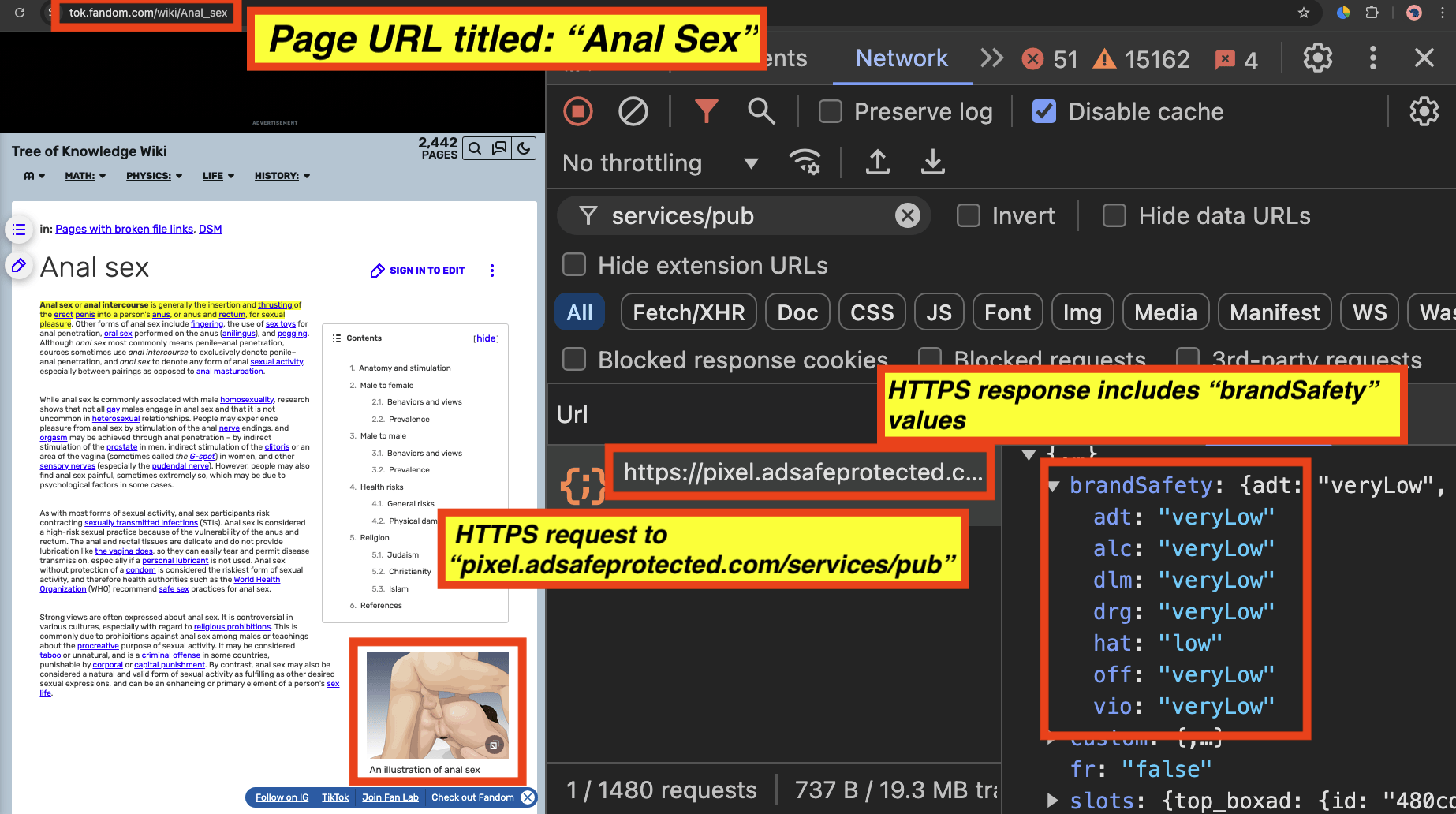
It appears that for an article titled: “Anal Sex”, all seven key value pairs are set to “veryLow” or “low” by IAS’s “pixel.adsafeprotected.com/services/pub” server endpoint.
In the data table below, one can observe the various “brandSafety” key value pairs observed in the HTTPS response from IAS’s “pixel.adsafeprotected.com/services/pub” server endpoint on various page URLs.
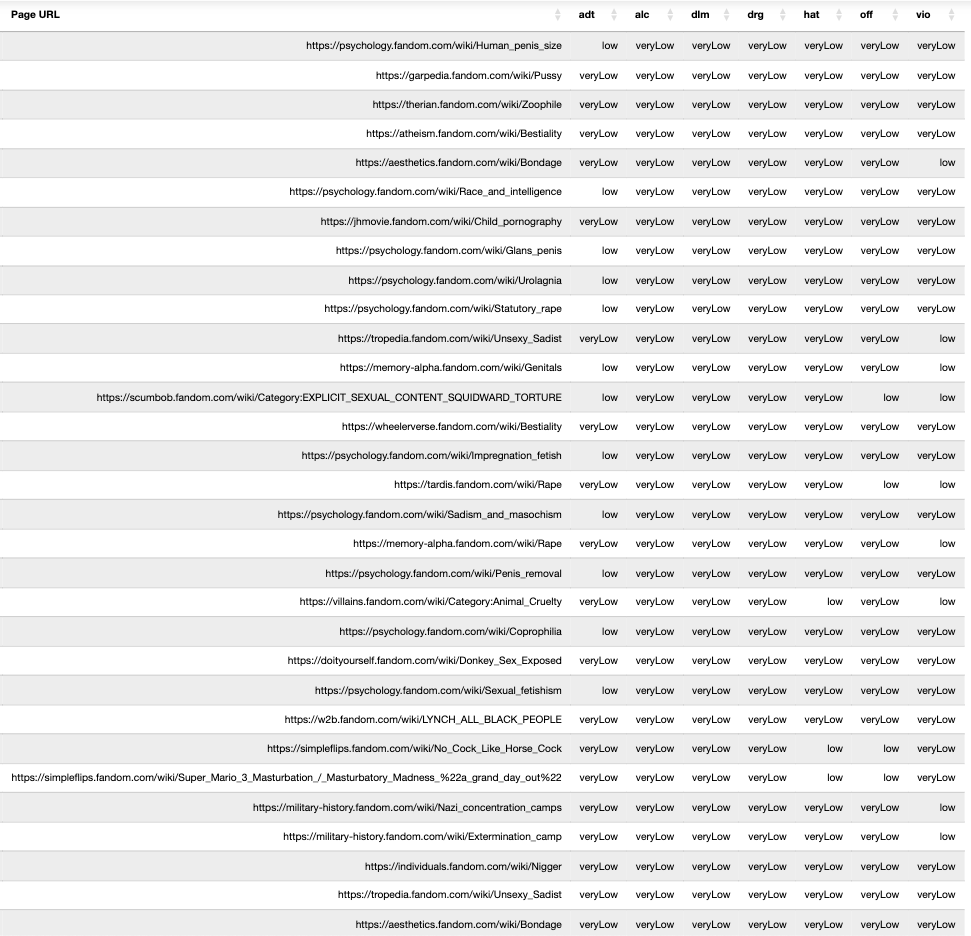
Data table illustrating “brandSafety” key value pairs observed in the HTTPS response from IAS’s “pixel.adsafeprotected.com/services/pub” server endpoint on various page URLs.
Ads which appear to include code from verification vendors and were observed on potentially objectionable content
Ads which include references to billing for “brand safety”
For a subset of digital ads observed, it appears to be possible to extract from the source code of the ad if a given brand appeared to be “charged” (invoiced) for brand safety services from a given vendor.
The source of some ads appear to contain (in Base64 encoded text) references to specific data segments, vendors, or services that were applied for a given ad campaign.
For example, many IKEA ads observed on pages such as “LY*CH ALL B***K PEOPLE” (redacted in this report) contained source code from a demand side platform, which included Base64 encoded references to: “charge-maxDoubleVerifyBrandSafety”. The IAB states that “content that contains hate speech directed at a protected class would be inappropriate for any advertising”.

Screenshot of an IKEA ad seen on a page titled: “LY*CH ALL B***K PEOPLE” (redacted in this report). The IKEA ad includes references to WPP/GroupM’s Xaxis, and Base64-encoded text references to “charge-maxDoubleVerifyBrandSafety”. The IAB states that “content that contains hate speech directed at a protected class would be inappropriate for any advertising”.
As a second example, many Fruity Pebbles Target retail media ads observed on pages such as “LY*CH ALL B***K PEOPLE” (redacted in this report) contained source code from a demand side platform, which included Base64 encoded references to: “charge-maxDoubleVerifyBrandSafety”. The IAB states that “content that contains hate speech directed at a protected class would be inappropriate for any advertising”.
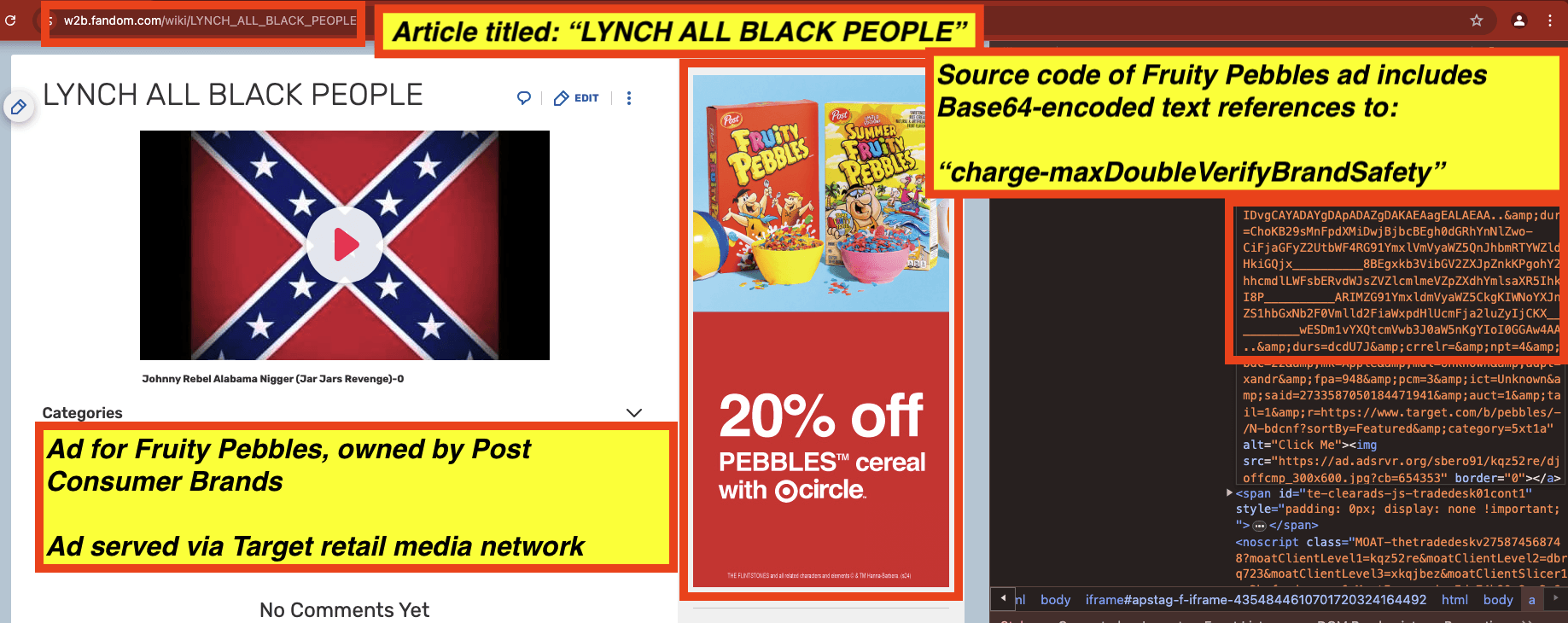
Screenshot of an Fruity Pebbles (owned by Post Consumer Brands) ad seen on a page titled: “LY*CH ALL B***K PEOPLE” (redacted in this report). The Fruity Pebbles ad was transacted via Target retail media network. The Fruity Pebbles ad includes a Base64-encoded text reference to “charge-maxDoubleVerifyBrandSafety”. The IAB states that “content that contains hate speech directed at a protected class would be inappropriate for any advertising”.
As a third example, various Thomson Reuters and Grammarly ads which were observed on pages such as “Big Black Dildo”, “Human penis size”, and "N*****" (redacted in this report) contained source code from a demand side platform, which included Base64 encoded references to: “charge-allIntegralBrandSafety”.

Screenshot of a Grammarly ad seen on a page titled: "N*****" (redacted in this report). The Grammarly ad includes a Base64-encoded text reference to “charge-charge-allIntegralBrandSafety”. The right side of the screenshot shows 33 HTTPS requests made to various “adsafeprotected.com” server endpoints. “adsafeprotected.com” is a domain operated by IAS. IAS’s website states that: “topics like hate speech and terrorism tend to present brand equity risk to most advertisers. Brand safety is for every brand and reflects the need to avoid serving ads adjacent to unsafe content – content that’s generally recognized as unsafe for any brand.”
As a fourth example, a Target retail media ad for Post Consumer brands transacted by Publicis media agency was observed on an article titled: "Cock sucker" with Javascript from “adsafeprotected.com” (an IAS owned domain) inside the ad. The source code of the Target/Post Consumer Brands article includes a DSP win notification pixel which included Base64 encoded references to: “charge-allIntegralBrandSafety”, "charge-allIntegralKeywordBlacklist", “charge-allIntegralPageQuality", and “charge-allIntegralCustomTargeting".

Screenshot of a Target retail media ad for Post Consumer brands transacted by Publicis media agency was observed on an article titled: "Cock sucker" with Javascript from “adsafeprotected.com” (an IAS owned domain) inside the ad. The source code of the Target/Post Consumer Brands article includes a DSP win notification pixel which included Base64 encoded references to: “charge-allIntegralBrandSafety”, "charge-allIntegralKeywordBlacklist", “charge-allIntegralPageQuality", and “charge-allIntegralCustomTargeting".
As a fifth example, a Live Nation ad was observed on an article titled: “Big Black N***a Dicks” (redacted in this report) with Javascript from “adsafeprotected.com” (an IAS owned domain) inside the ad. The source code of the Live Nation article includes a DSP win notification pixel which included Base64 encoded references to: “charge-maxDoubleVerifyBrandSafety".

Screenshot of an Live Nation ad seen on a page titled: “Big Black N***a Dicks” (redacted in this report). The Live Nation ad includes Base64-encoded text references to “charge-maxDoubleVerifyBrandSafety”.
As a sixth example, various Thomson Reuters and Grammarly ads which were observed on pages such as “Big Black Dildo”, “Human penis size”, and "N*****" (redacted in this report) contained source code from a demand side platform, which included Base64 encoded references to: “charge-allIntegralBrandSafety”.
The table below illustrates examples of various brands’ ads, on which page URLs the ads were observed, and the Base64 decoded text observed in the source of the given brand’s ads.
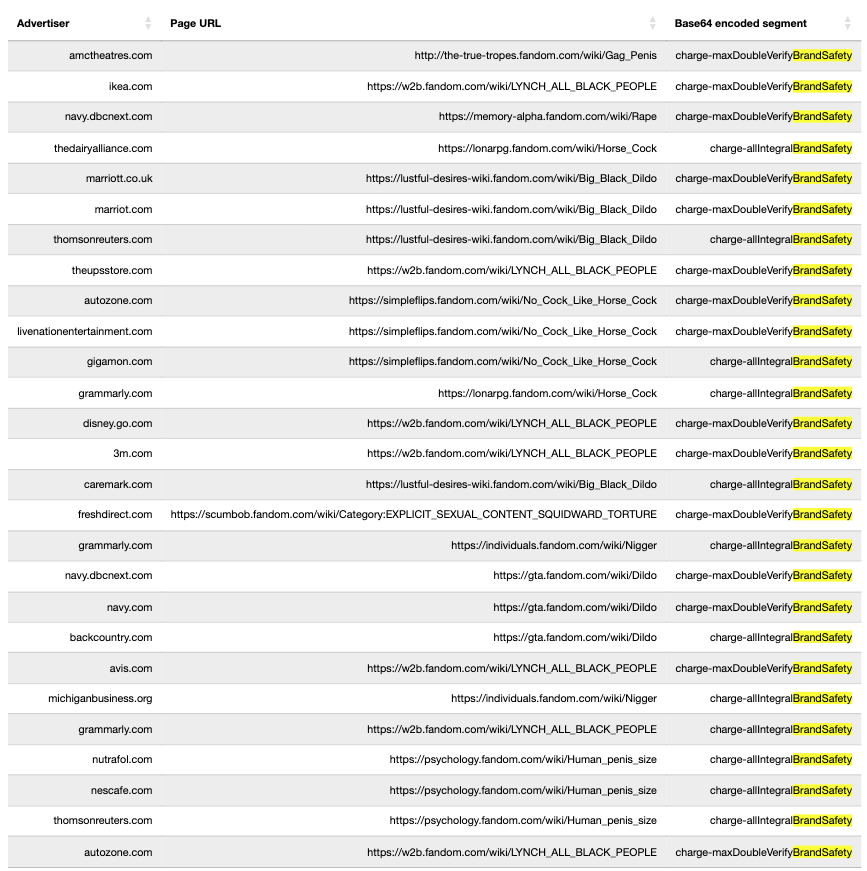
Ads from such brands as Ikea, UPS, Disney, 3M, Avis car rental, and Autozone were observed on an article titled “LY*CH ALL B***K PEOPLE” (redacted in this report). The IAB states that “content that contains hate speech directed at a protected class would be inappropriate for any advertising”. These brands’ source code included Base64-encoded text references to “charge-maxDoubleVerifyBrandSafety”. The source code of ads from Grammarly on these pages included references to “charge-allIntegralBrandSafety.”
Ads whose source code include javascript or pixels from verification vendors
For a subset of digital ads observed, it appears to be possible to extract from the source code of the ad if a given brand appeared to be “charged” (invoiced) for brand safety services from a given vendor. However, for many ads, it is not technically feasible to extract this information.
However, it is possible to observe whether or not a given brand’s ads appeared to contain Javascript code from a given vendor. For example, some ads appear to contain Javascript from “doubleverify.com”, a domain owned by DoubleVerify. Other ads appear to contain Javascript code from “adsafeprotected.com”, an IAS domain.
It is important to note that not all Javascript loaded from these domains will be exclusively related to brand safety. The Javascript may be related to measuring ad viewability, reporting and monitoring, or bot detection. However, in some cases it is ostensibly plausible that a given Javascript code is related specifically to brand safety ‘blocking’. As such, these observations were included for consideration.
In the screenshot below, one can observe two Volvo cars ads appearing on the page “Super Mario 3 Masturbation”, which discusses a person “vigorously masturbating”. The “Why this ad?” information modal shows that both Volvo ads were transacted by MindShare, a media agency subsidiary of WPP/GroupM. The source code of the Volvo ads on the “Super Mario 3 Masturbation” pages includes Javascript from “adsafeprotected.com”, owned by IAS. The Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.

Screenshot of two Volvo ads transacted by GroupM’s Mindshare media agency observed on “Super Mario 3 Masturbation”. The source code of the ads includes Javascript from IAS.
As another example, in the screenshot below, one can see an AMC Theatres ad observed on an article titled “𝓝****𝓡” (redacted in this report). The source code of the AMC Theatres ad includes Javascript from “doubleverify.com”, a domain owned by DoubleVerify. The Javascript includes references to “brand_safety”.

Screenshot of an AMC ad observed on an article titled: “𝓝****𝓡” (redacted in this report). The source code of the AMC Theatres ad includes Javascript from DoubleVerify, and references to “brand_safety”.
As a second example, in the screenshot below, one can see a Mercedes Benz ad observed on the article titled “Super Mario 3 Masturbation”. The Mercedes Benz ad was transacted by Omnicom’s OMD media agency, according to the “Why this ad?” information modal. The source code of the Mercedes Benz ad includes Javascript from “doubleverify.com”. The Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
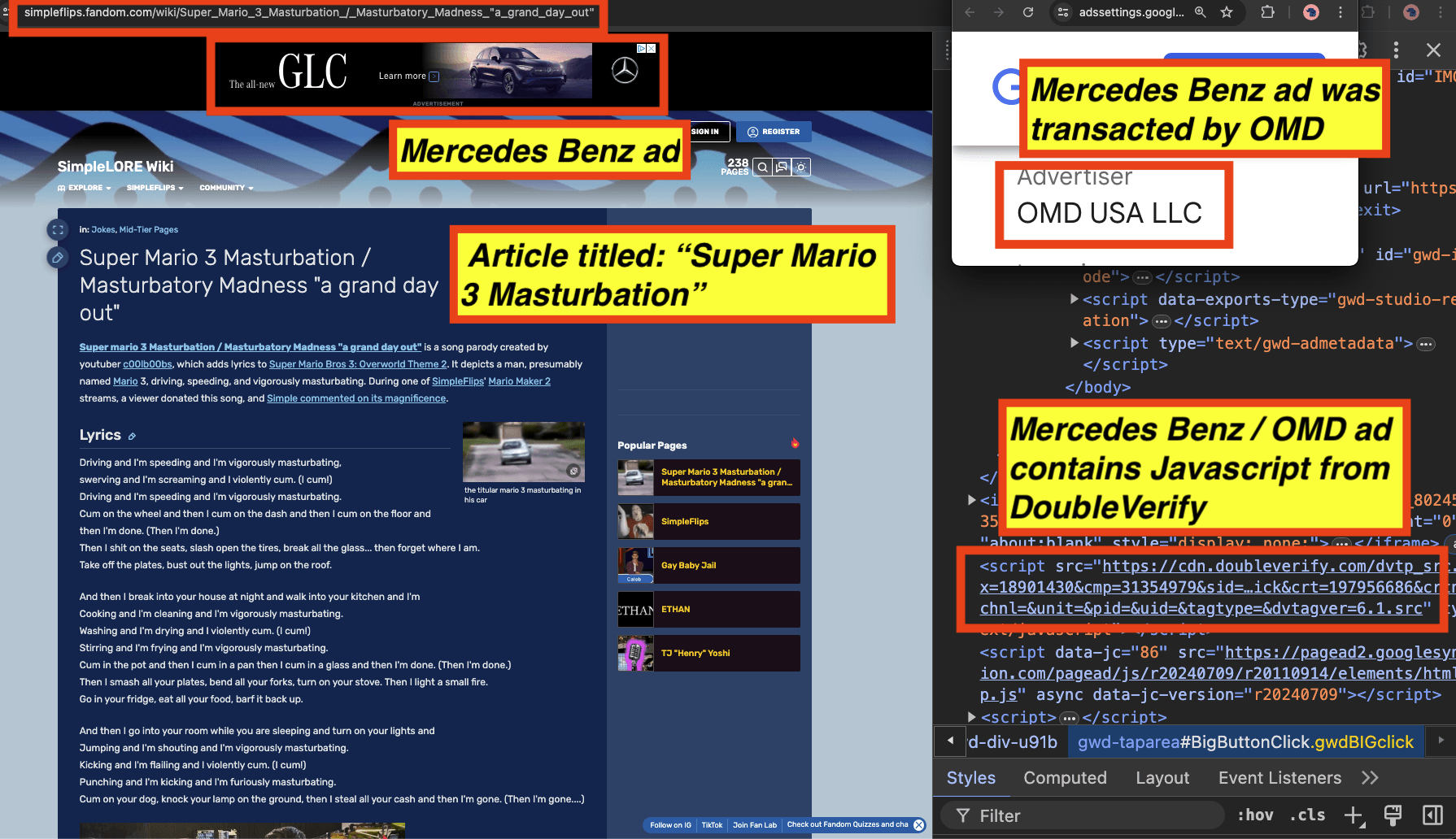
Screenshot of a Mercedes Benz ad transacted by OMD media agency observed on “Super Mario 3 Masturbation”. The source code of the ads includes Javascript from DoubleVerify.
As a third example, in the screenshot below, one can see a T-Mobile ad observed on an article titled “List of films portraying paedophilia or sexual abuse of minors”. The source code of the T-Mobile ad includes Javascript from “adsafeprotected.com”, a domain owned by IAS. The Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
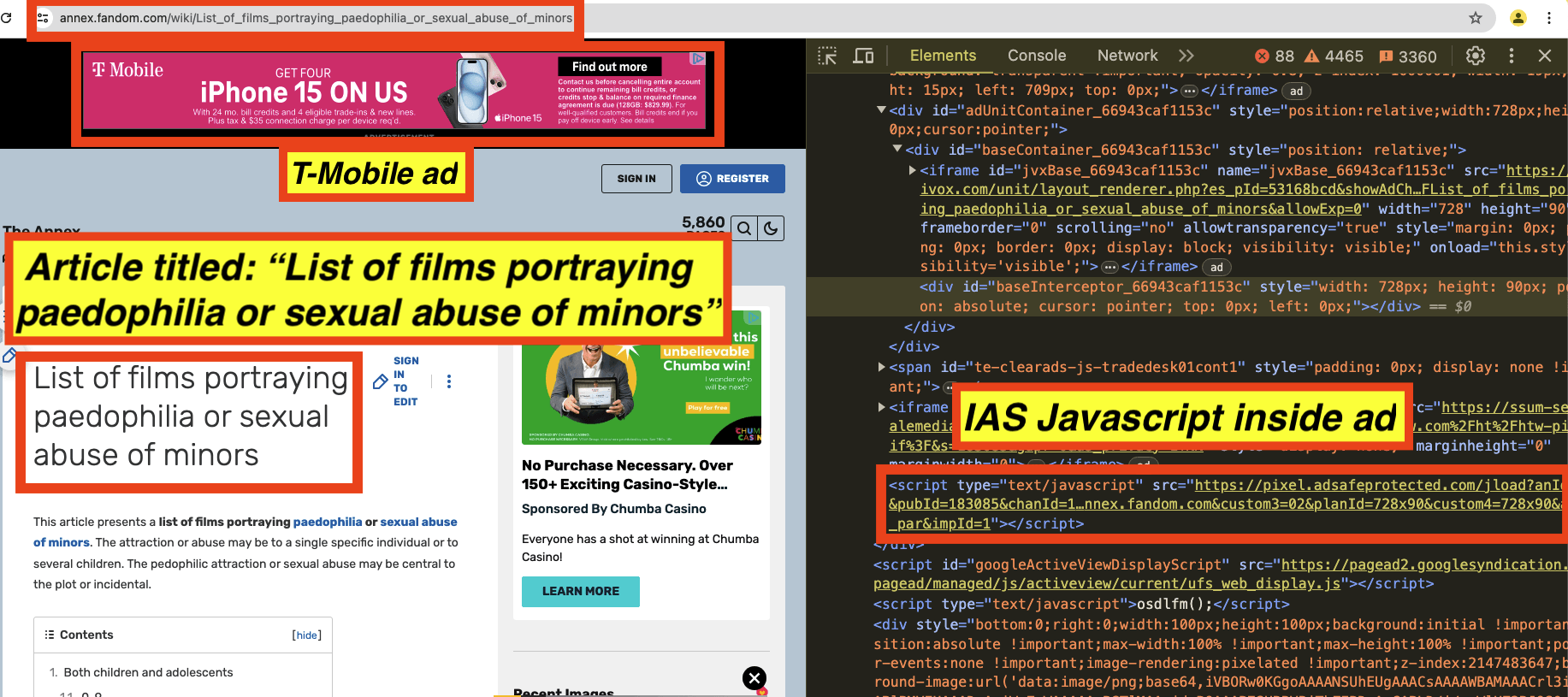
Screenshot of a T-Mobile ad observed on “List of films portraying paedophilia or sexual abuse of minors”. The source code of the ads includes Javascript from IAS.
As a fourth example, in the screenshot below, one can see a Make America Great Again (magapac.com) ad observed on an article titled “Gag Penis”. The source code of the Make America Great Again ad includes Javascript from “adsafeprotected.com”, a domain owned by IAS. The Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
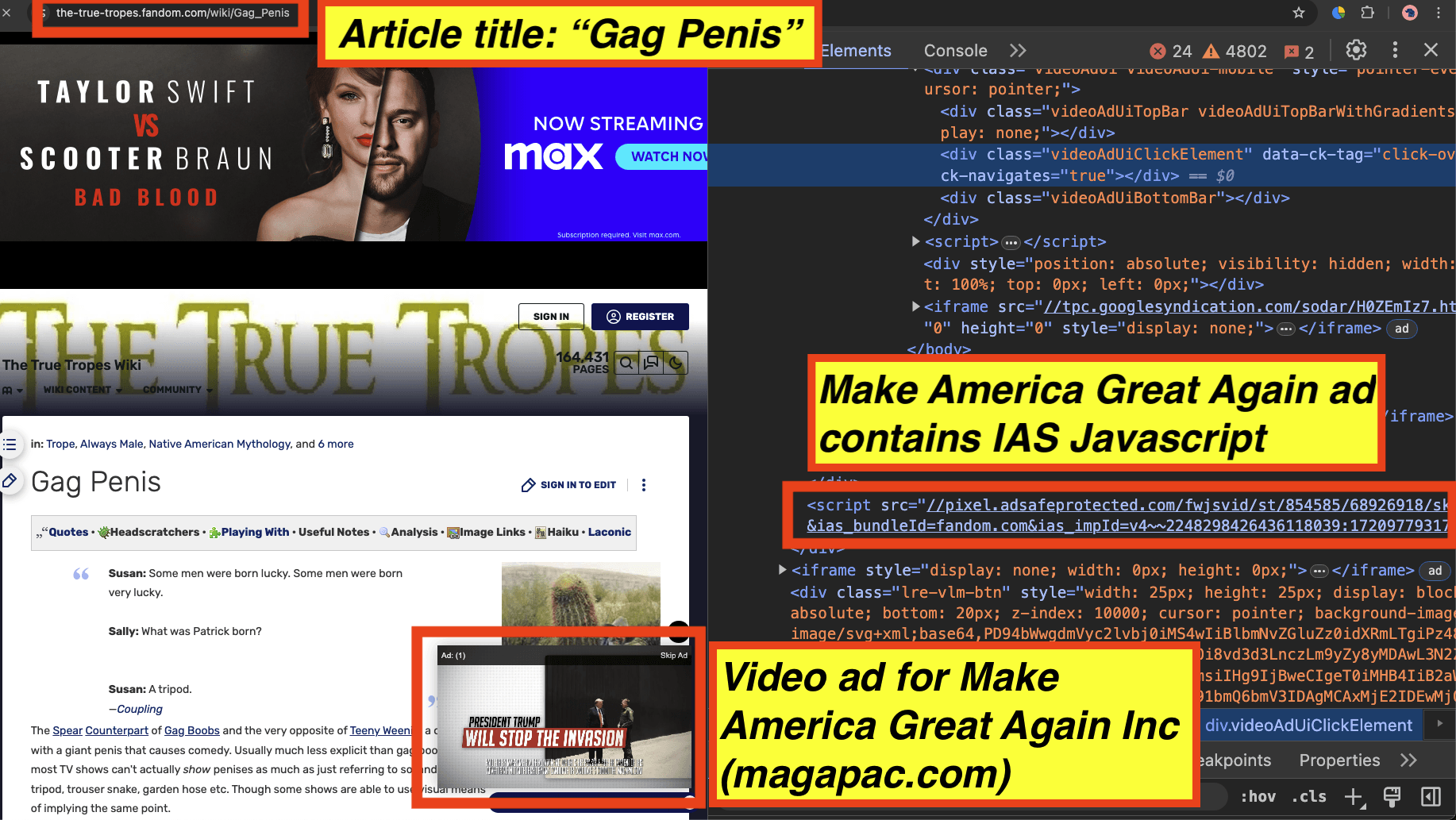
Screenshot of a Make America Great Again (magapac.com) ad observed on an article titled: “Gag Penis”. The source code of the ads includes Javascript from IAS.
As a fifth example, in the screenshot below, one can see a North Face ad observed on an article titled “Sexual abuse of people with developmental disabilities”. The source code of the North Face ad includes Javascript from “adsafeprotected.com”, a domain owned by IAS. The Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
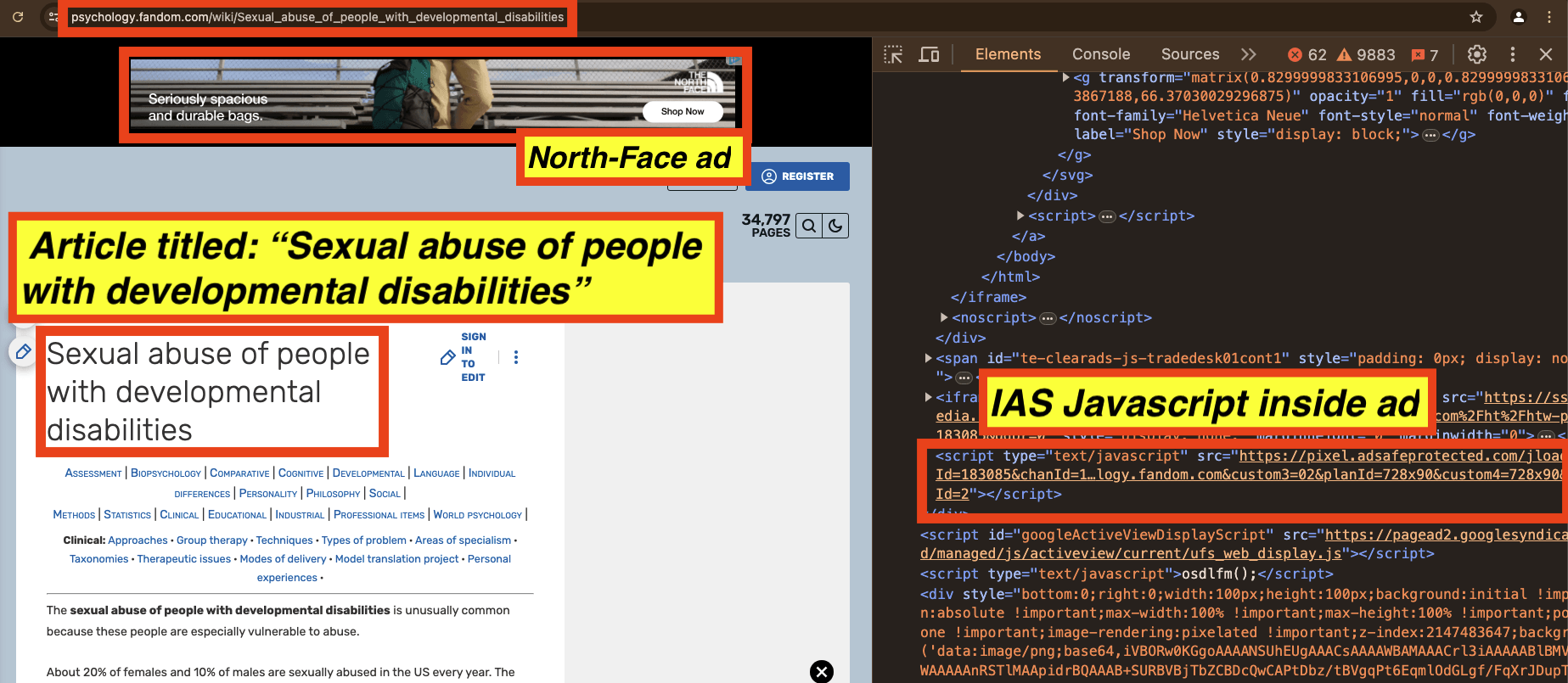
Screenshot of a North Face ad observed on an article titled: “Sexual abuse of people with developmental disabilities”. The source code of the ads includes Javascript from IAS.
As a sixth example, in the screenshot below, one can see a Kenvue Zyrtec ad observed on an article titled “No Cock Like Horse Cock”, which includes mentions of a man “ramming horse dildos up his ass with lube”. The source code of the Kenvue Zyrtec ad includes Javascript from “adsafeprotected.com”, a domain owned by IAS. The Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
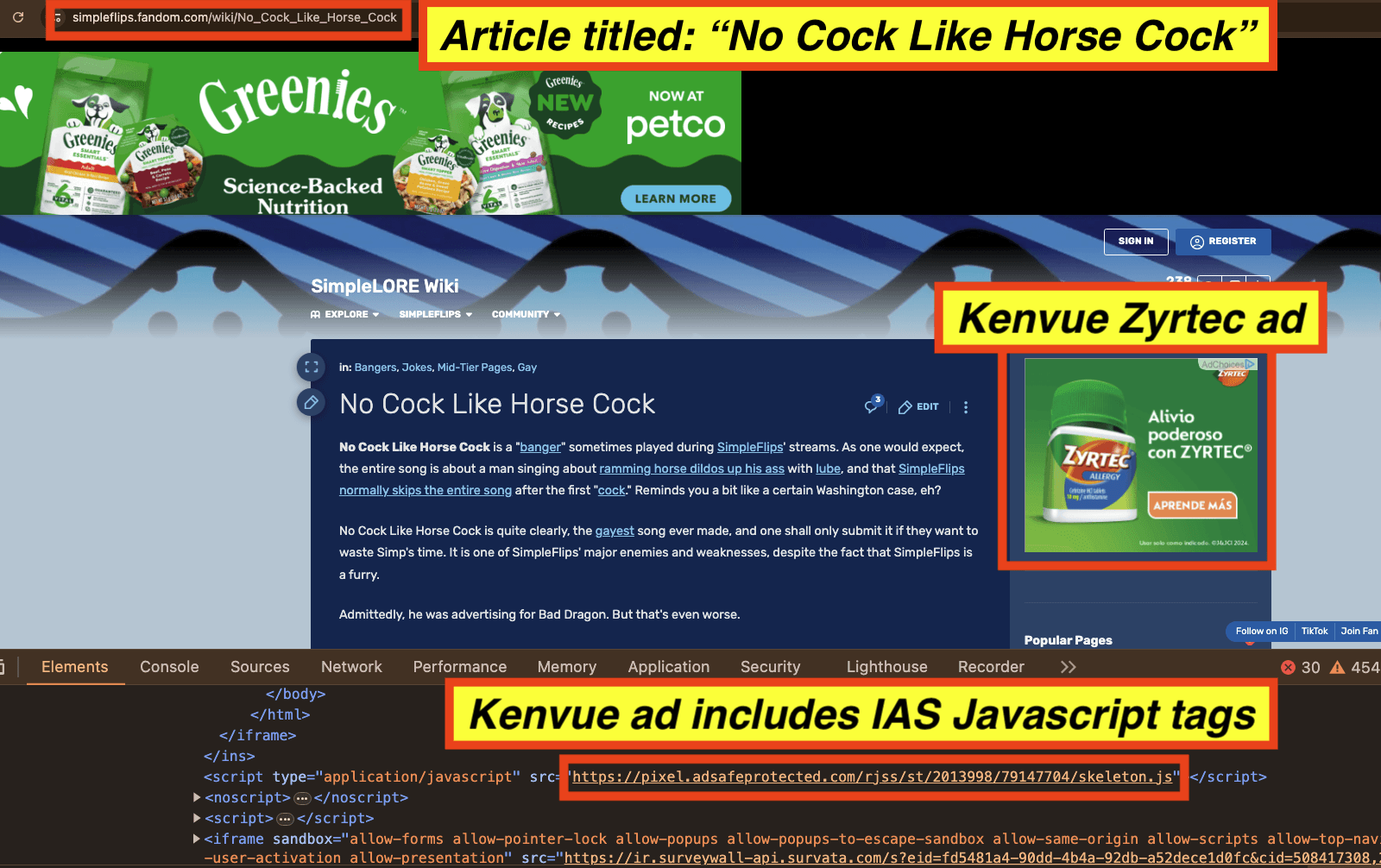
Screenshot of a Kenvue Zyrtec ad observed on an article titled: “No Cock Like Horse Cock”. The source code of the ads includes Javascript from IAS.
As a seventh example, in the screenshot below, one can see an AMC Theatres ad observed on an article titled “Sexual abuse of people with developmental disabilities”. The source code of the AMC Theatres ad includes Javascript from “doubleverify.com”, a domain owned by DoubleVerify. The Javascript includes references to “brand_safety”.
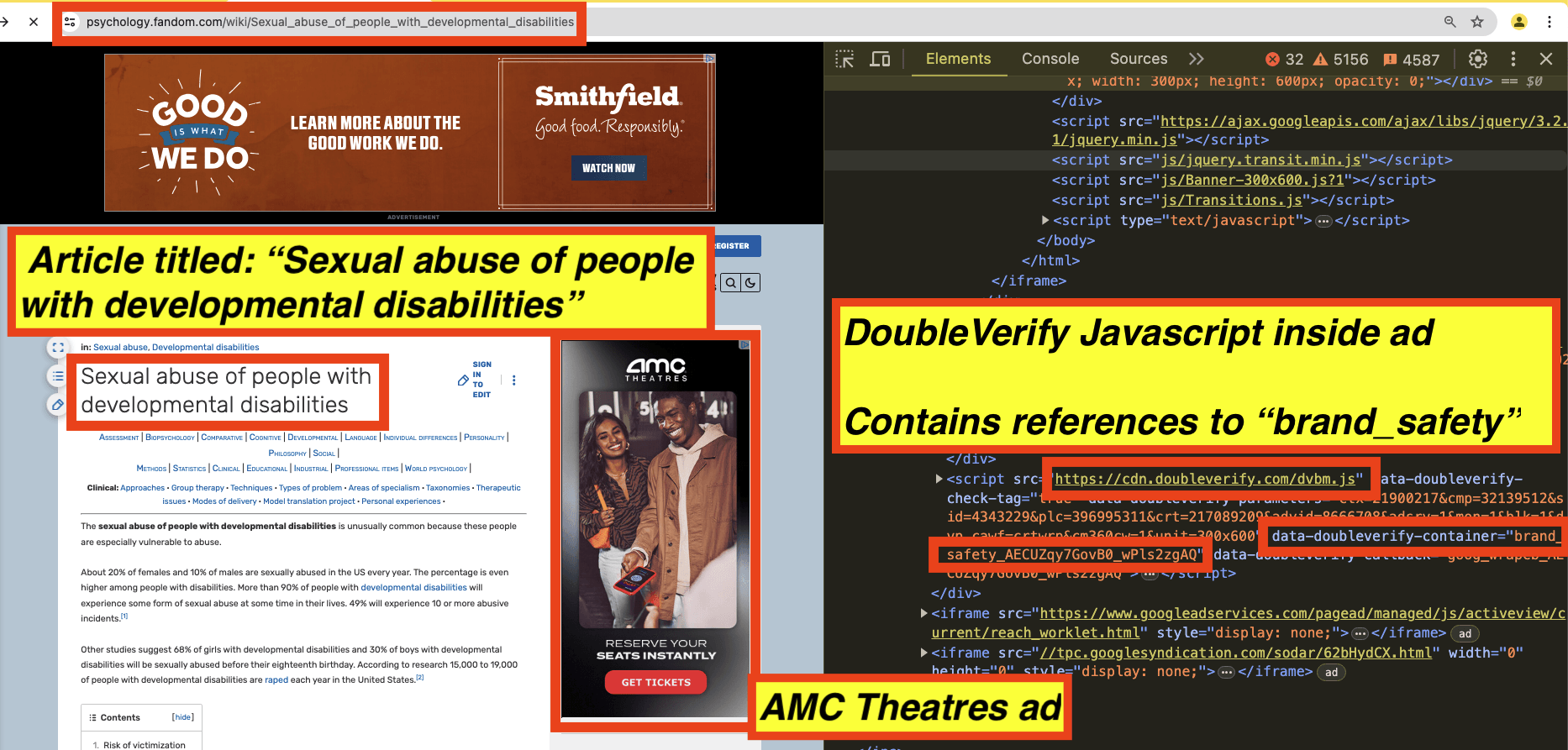
Screenshot of an AMC Theatres ad observed on an article titled: “Sexual abuse of people with developmental disabilities”. The source code of the ads includes Javascript from DoubleVerify, which includes references to “brand_safety”.
As an eighth example, in the screenshot below, one can see a Smithfield Foods ad observed on an article titled “Sexual abuse of people with developmental disabilities”. The source code of the Smithfield Foods ad includes Javascript from “adsafeprotected.com”, a domain owned by IAS. The Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
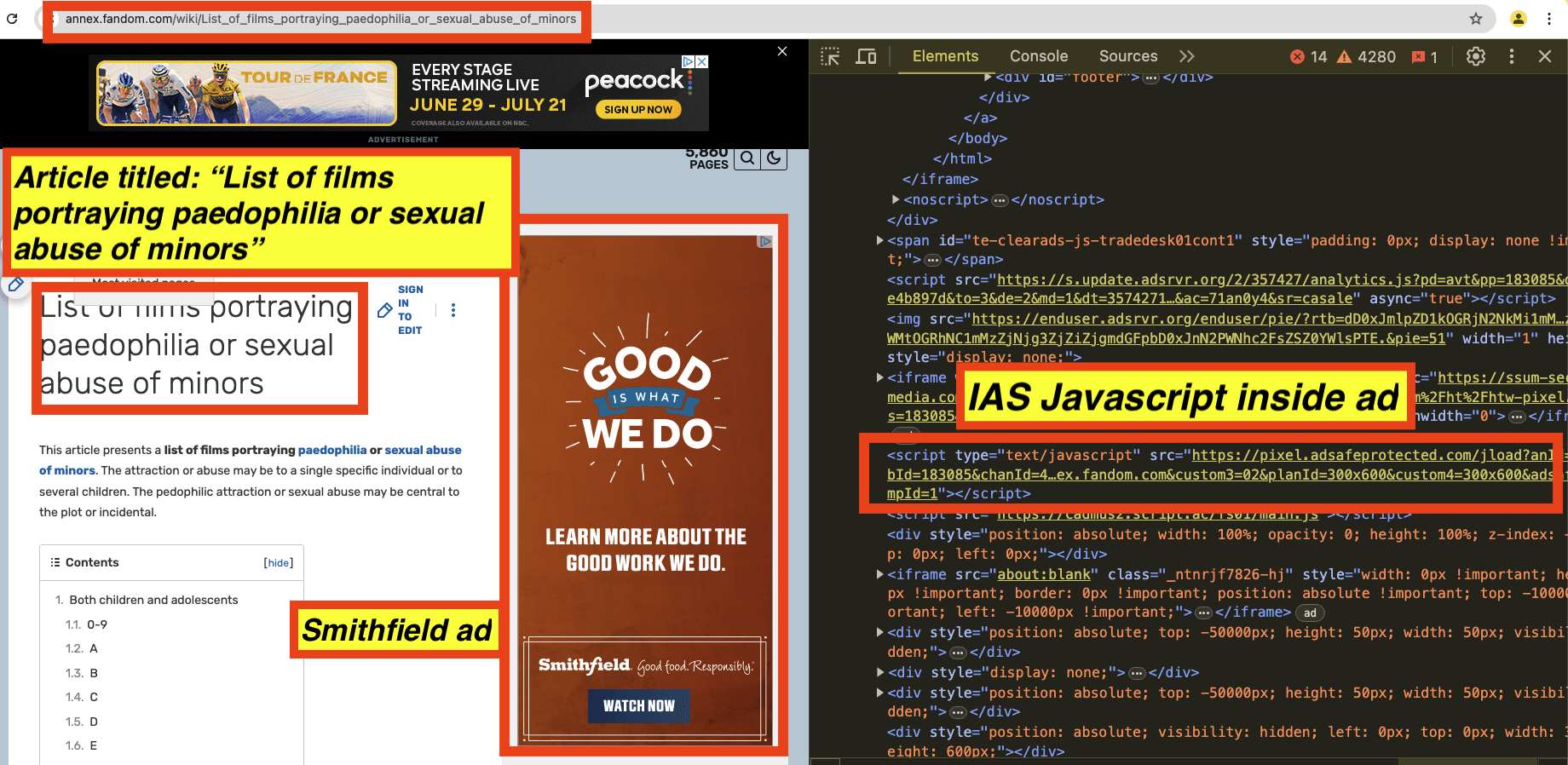
Screenshot of a Smithfield Foods ad observed on an article titled: “List of films portraying paedophilia or sexual abuse of minors”. The source code of the ad includes Javascript from IAS.
As another example, in the screenshot below, one can see a Walgreens Pharmacy ad observed on an article titled “𝓝****𝓡” (redacted in this report). The source code of the Walgreens ad includes Javascript from “doubleverify.com”, a domain owned by DoubleVerify and from “adsafeprotected.com”, a domain owned by IAS. The Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
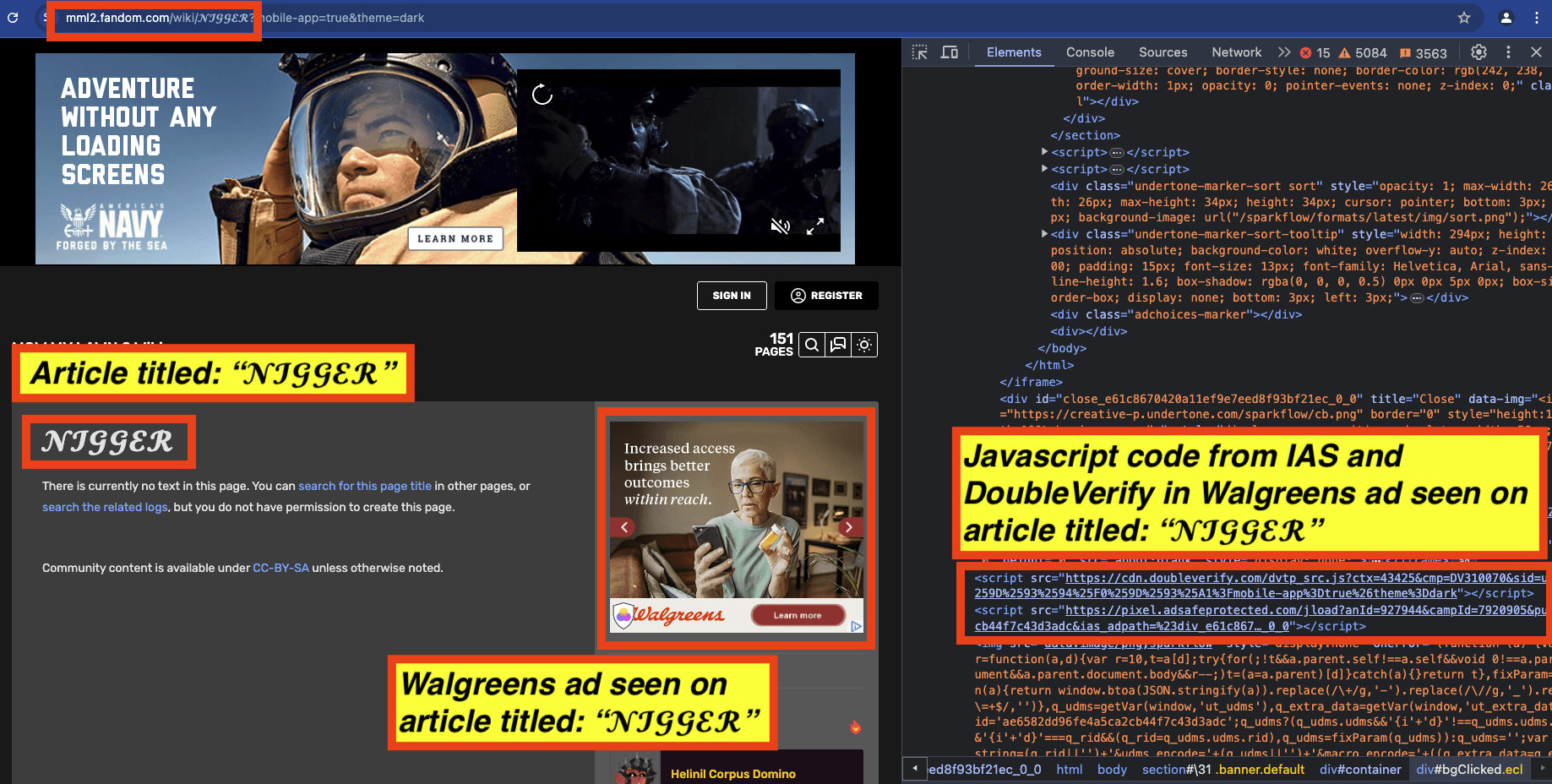
Screenshot of a Walgreens ad observed on an article titled: “𝓝****𝓡” (redacted in this report). The source code of the Walgreens ad includes Javascript from DoubleVerify and from IAS.
As another example, in the screenshot below, one can see a Nintendo ad observed on an article titled “𝓝****𝓡” (redacted in this report). The source code of the Nintendo ad includes Javascript from “adsafeprotected.com”, a domain owned by IAS. The Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
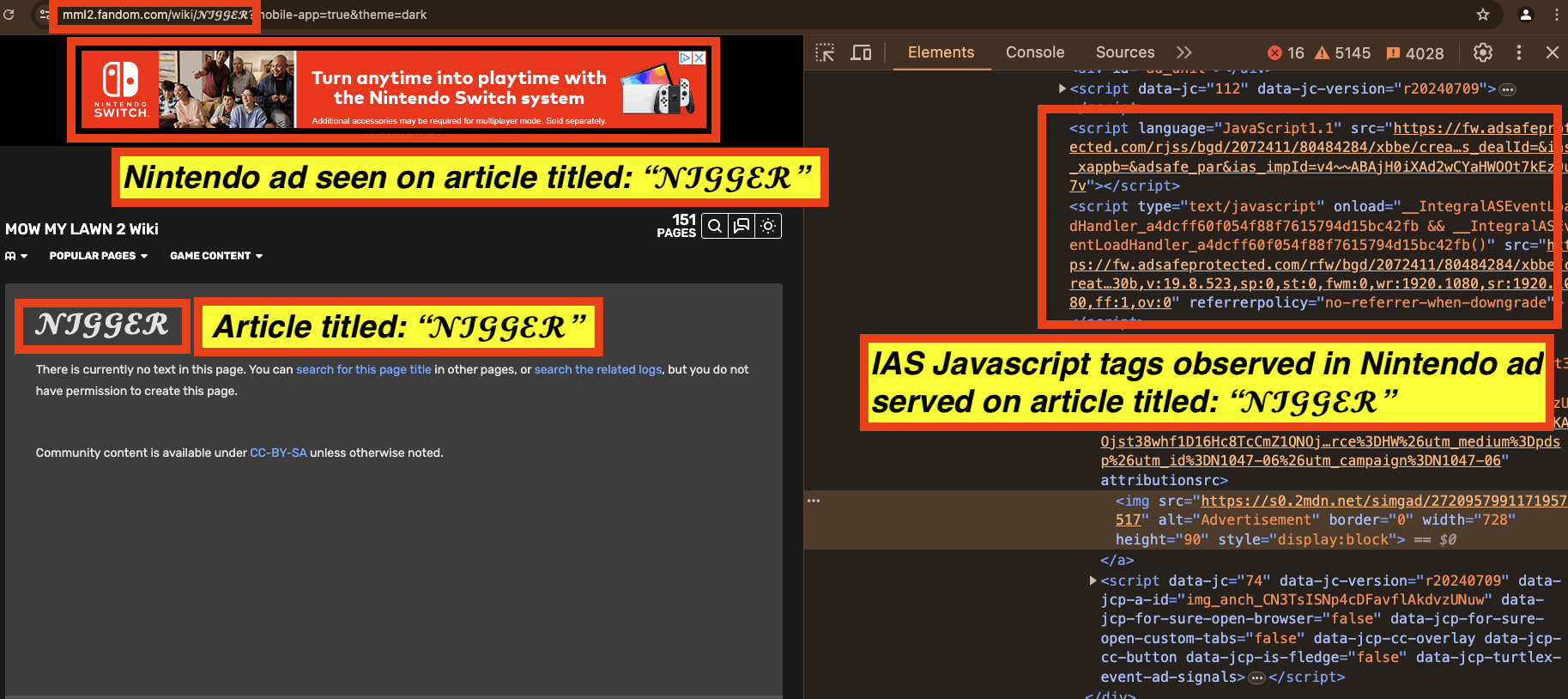
Screenshot of a Nintendo ad observed on an article titled: “𝓝****𝓡” (redacted in this report). The source code of the Nintendo ad includes Javascript from IAS.
As another example, in the screenshot below, one can see an Apple ad observed on an article titled “Anal Sex”. The source code of the Apple ad includes Javascript from “doubleverify.com”, a domain owned by DoubleVerify. The Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
Screenshot of an Apple video ad observed on an article titled: “Anal Sex”. The source code of the Nintendo ad includes Javascript from DoubleVerify.
As another example, in the screenshot below, one can see a Pizza Hut ad observed in an article titled “Anal Sex”. The source code of the Apple ad includes Javascript from “adsafeprotected.com”, a domain owned by IAS. The Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
Screenshot of a Pizza Hut video ad observed on an article titled: “Anal Sex”. The source code of the Pizza Hut ad includes Javascript from IAS.
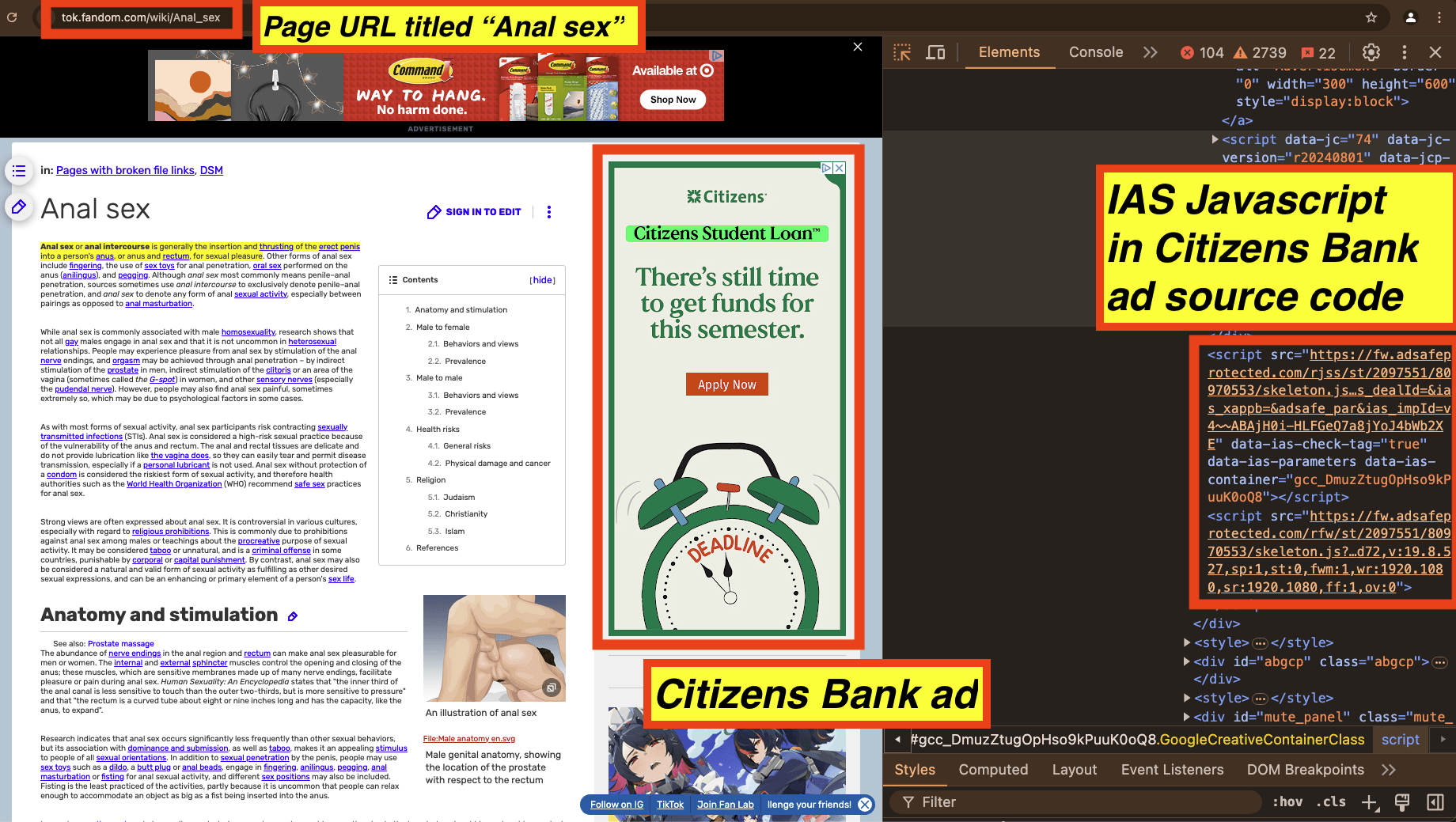
As another example, in the screenshot below, one can see a Target retail media network ad for 3M and a Citizens Bank ad observed in an article titled “Anal Sex”. The source code of the Citizens Bank ad includes Javascript from “adsafeprotected.com”, a domain owned by IAS. The Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.

Screenshot of a Citizens Bank ad observed in an article titled: “Anal Sex”. The source code of the Citizens Bank ad includes Javascript from IAS.
In the graphic table below, one can see a sample of brands whose ads were observed on the selection of “potentially objectionable content” ads, and whose ads’ source code included Javascript from “adsafeprotected.com”. The IAS Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.





In the graphic table below, one can see a sample of brands whose ads were observed on the selection of “potentially objectionable content” ads, and whose ads’ source code included Javascript from “doubleverify.com”. The DoubleVerify Javascript may be related to viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.

Ads which include video VAST wrapper tags
For a subset of digital ads observed, it appears to be possible to extract from the source code of the ad if a given brand appeared to be “charged” (invoiced) for brand safety services from a given vendor. However, for many ads, it is not technically feasible to extract this information.
However, for video ads, it is possible to observe which brands appear to employ video “wrapper” tags from specific vendor domains and had their ads served on various potentially objectionable content pages. Some video ads are served from endpoints such as “vast.doubleverify.com”, “vast.adsafeprotected.com”, and “unified.adsafeprotected.com”.
It is important to note that not all Javascript loaded from these domains will be exclusively related to brand safety. The Javascript may be related to measuring video completion, ad viewability, reporting and monitoring, or bot detection. However, in some cases it is ostensibly plausible that a given Javascript code is related specifically to brand safety ‘blocking’. As such, these observations were included for consideration.
For example, the confectionary company Mars had video ads for Snickers and Twix served on articles about “Impregnation fetish” and “Horse Cock”. The Mars video ads appeared to use video ad wrappers from IAS (unified.adsafeprotected.com). The Javascript may be related to video completion, viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
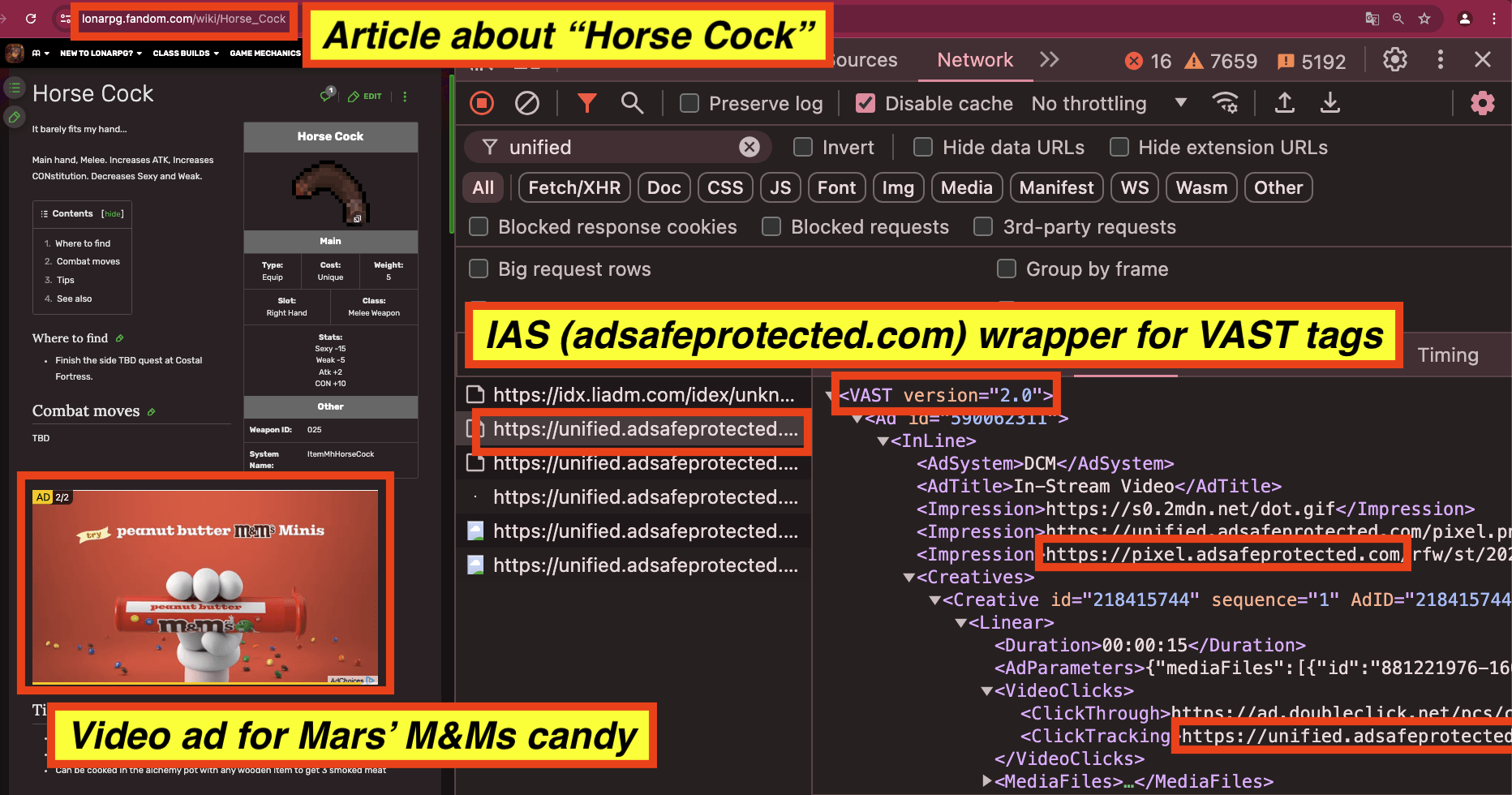
Screenshot of a Mars M&M’s video ad observed on an article titled: “Horse Cock”. The source code of the Mars M&M’s ad includes video VAST tag wrappers from “adsafeprotected.com”, owned by IAS.
As a second example, AllTrails had video ads served on an article titled: “Human Penis Size”. The AllTrails video ads appeared to use video ad wrappers from DoubleVerify (vast.doubleverify.com). The Javascript may be related to video completion, viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
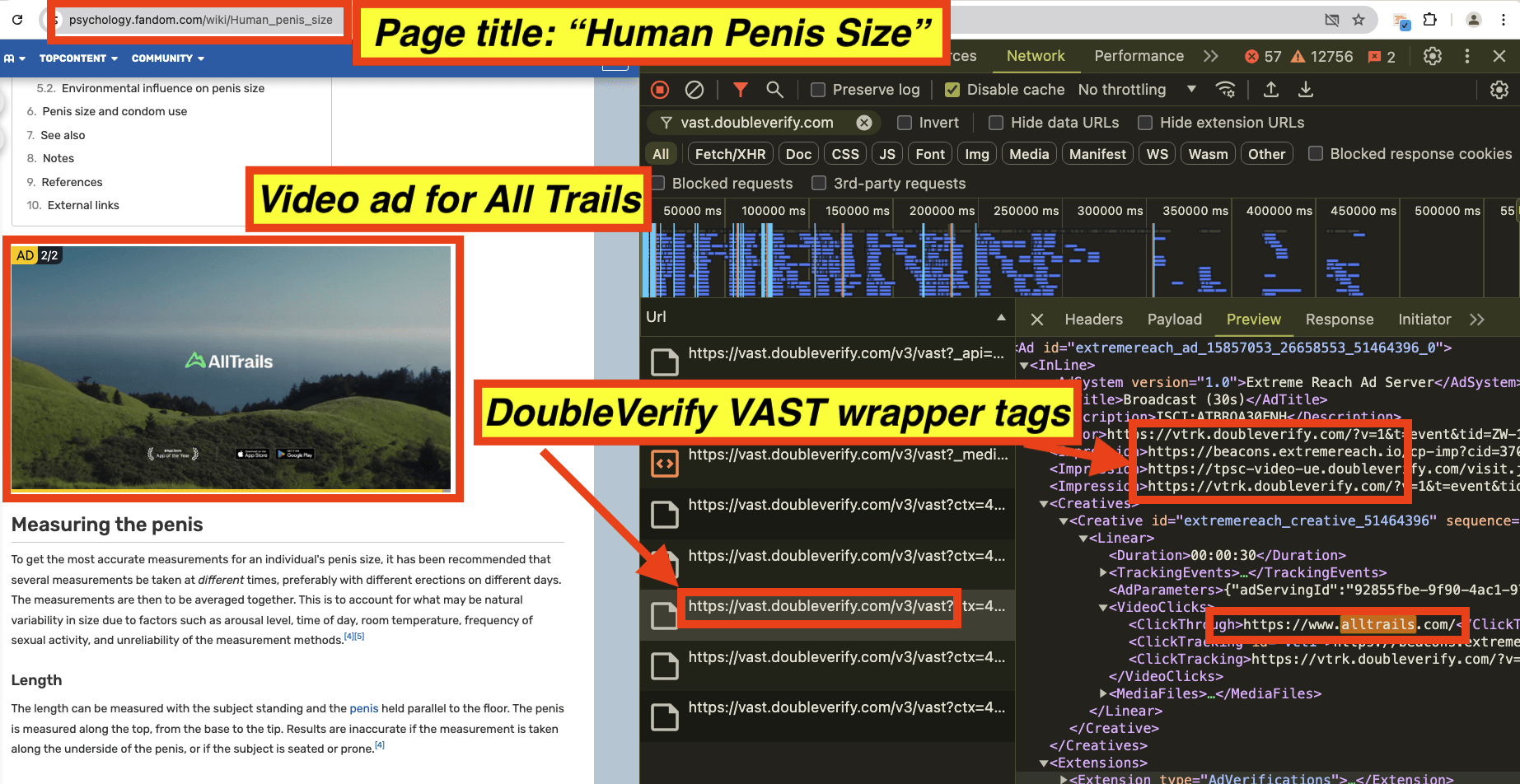
Screenshot of an AllTrails video ad observed on an article titled: “Human Penis Size”. The source code of the AllTrails ad includes video VAST tag wrappers from “vast.doubleverify.com”, owned by DoubleVerify.
As a third example, AllTrails had video ads served on an article titled “Sex Stats”. The Allstate video ad appeared to use video ad wrappers from IAS (unified.adsafeprotected.com). The Javascript may be related to video completion, viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
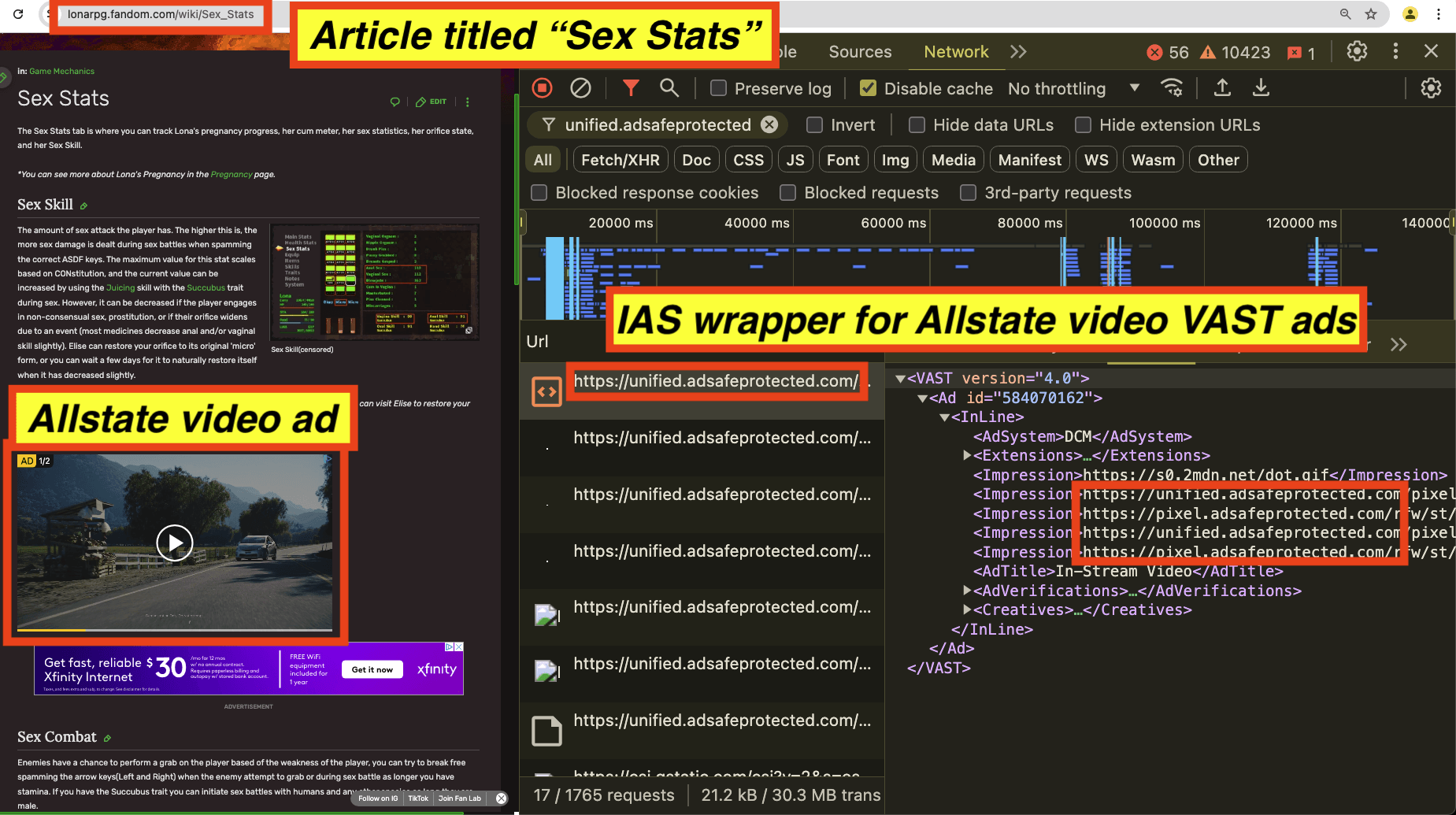
Screenshot of an Allstate insurance video ad observed on an article titled: “Sex stats”. The source code of the Allstate ad includes video VAST tag wrappers from “unified.adsafeprotected.com”, owned by IAS.
As a fourth example, International Justice Mission (ijm.org) had video ads served on an article titled “Coprophilia”. The International Justice Mission video ad appeared to use video ad wrappers from IAS (unified.adsafeprotected.com). The Javascript may be related to video completion, viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
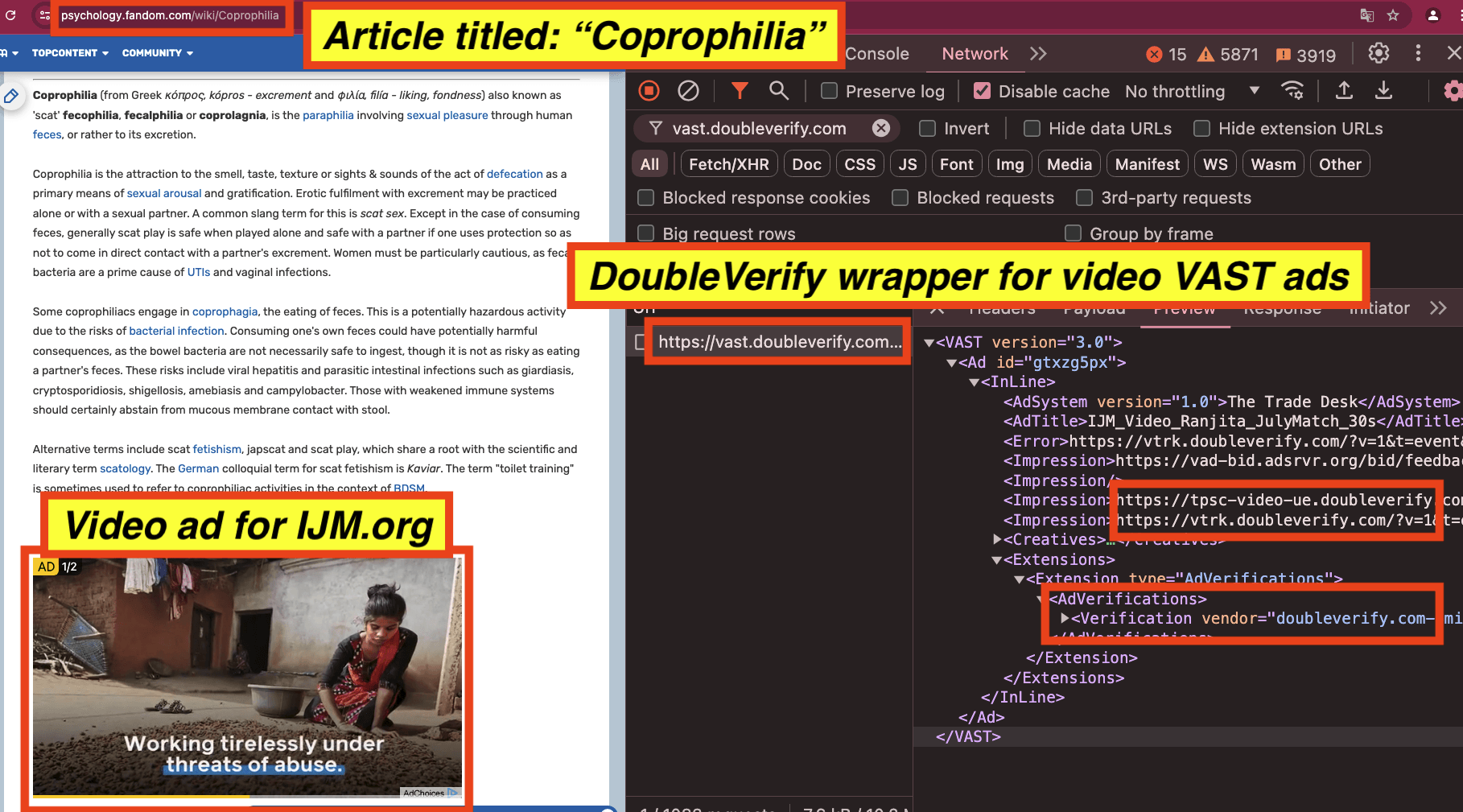
Screenshot of an International Justice Mission (IJM.org) video ad observed on an article titled: “Coprophilia”. The source code of the International Justice Mission ad includes video VAST tag wrappers from “vast.doubleverify.com”, owned by DoubleVerify.
As a fifth example, Pizza Hut had video ads served on an article titled “Impregnation fetish”. The Pizza Hut video ad appeared to use video ad wrappers from IAS (vast.adsafeprotected.com). The Javascript may be related to video completion, viewability, monitoring, and/or fraud detection, or it could also be related to brand safety functionality.
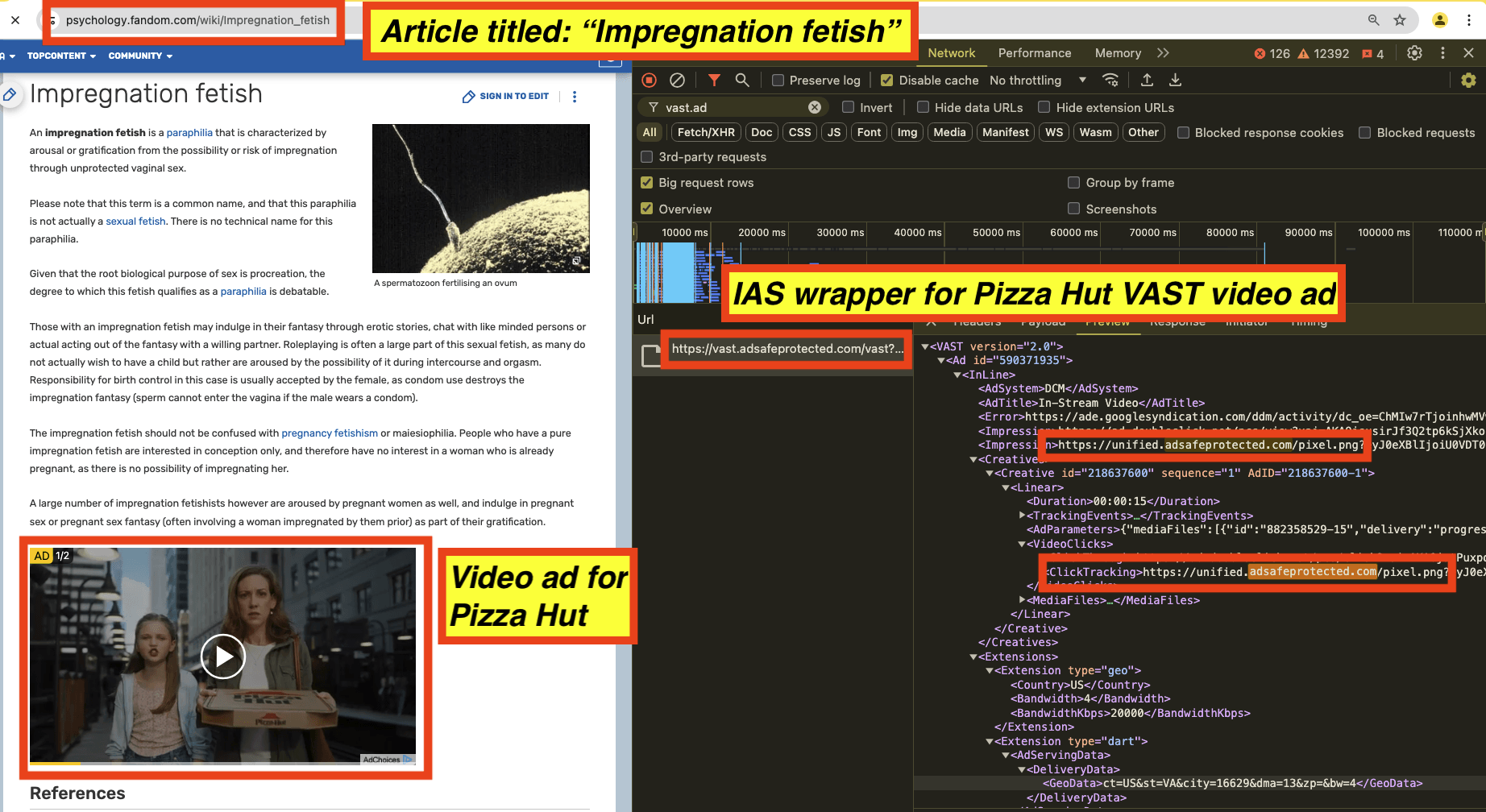
Screenshot of a Pizza Hut video ad observed on an article titled: “Impregnation fetish”. The source code of the Pizza Hut ad includes video VAST tag wrappers from “vast.adsafeprotected.com”, owned by IAS.
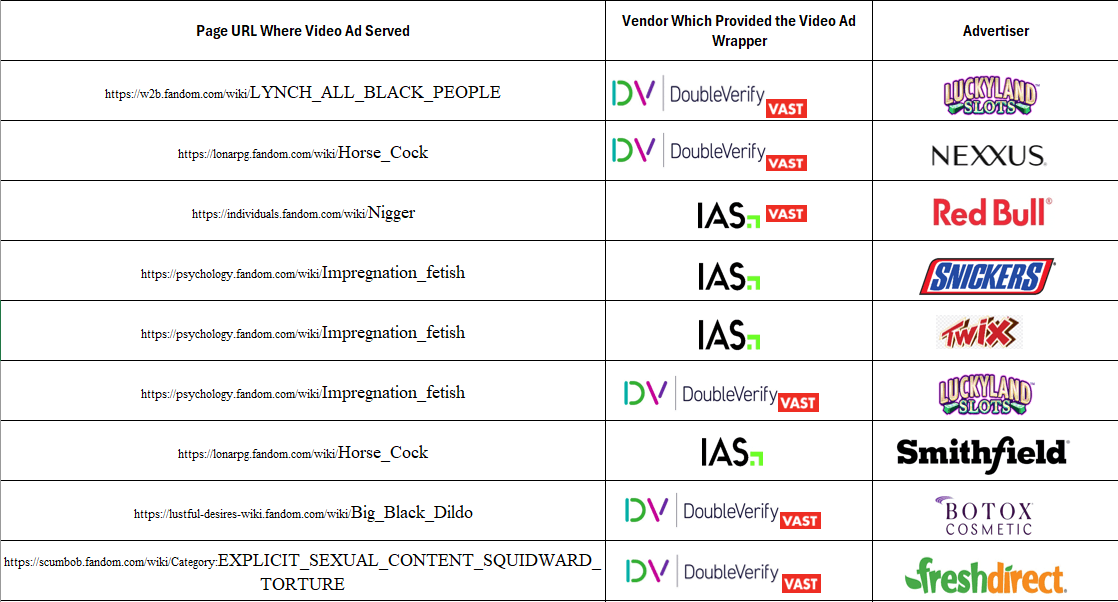
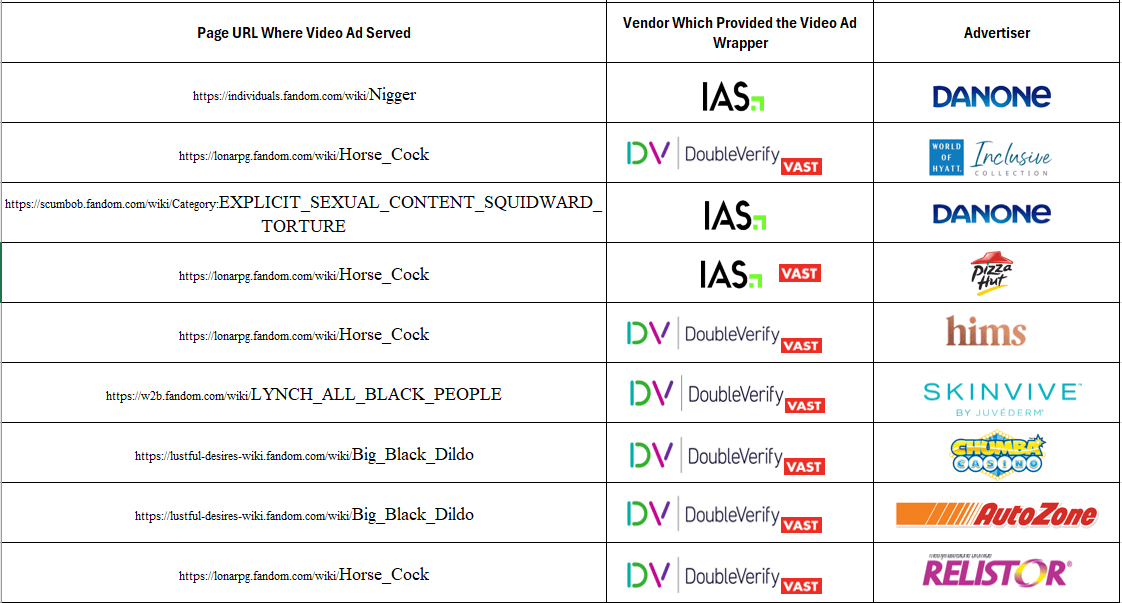
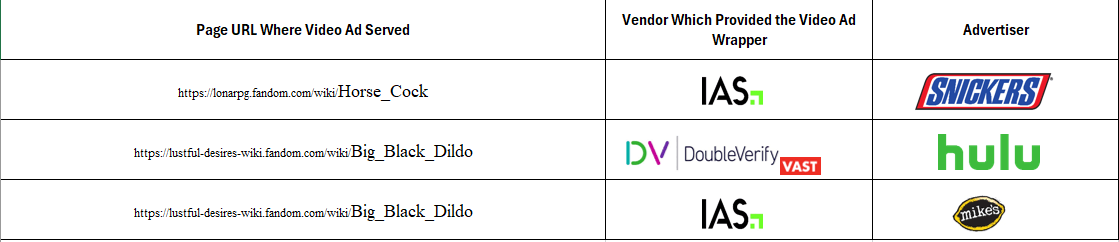
The table below shows additional examples of brand ads observed on various specific page URLs, and what video wrapper vendors observed in the source code of a given brands’ ads. For example, Pharmaceutical company Abbvie had video ads for “SKINVIVE™ by JUVÉDERM®” served on “LY*CH ALL B***K PEOPLE” (redacted in this report). The Abbvie video ads appeared to use video ad wrappers from DoubleVerify (vast.doubleverify.com). Redbull and yogurt company Danone had video ads served on an article titled: "N*****" (redacted in this report), showing the word "N*****" (redacted in this report) 5861 times. The Redbull and Danone video ads appeared to use video ad wrappers from IAS (vast.adsafeprotected.com and unified.adsafeprotected.com, respectively).
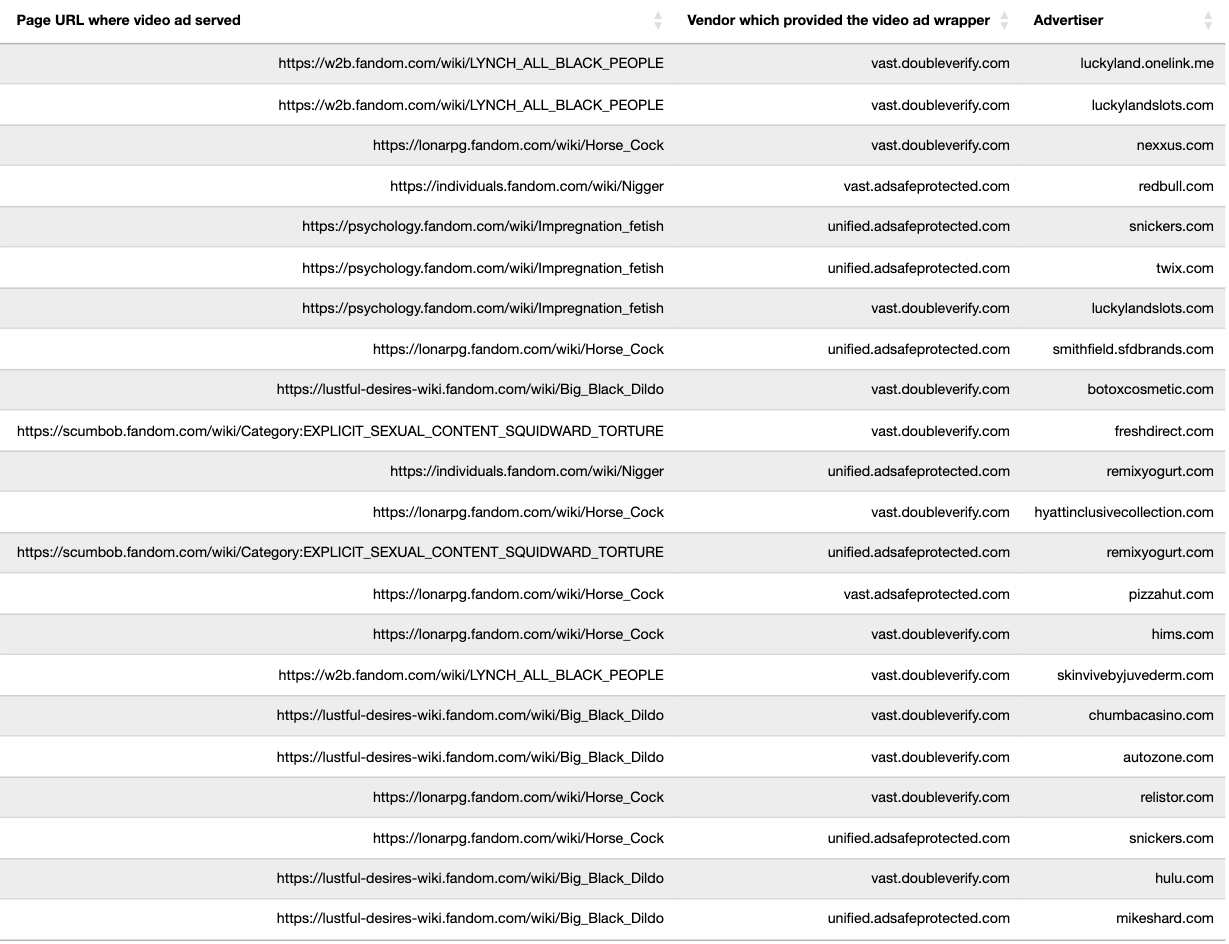
Data table illustrating examples of brand ads observed on various specific page URLs, and what video wrapper vendors observed in the source code of a given brands’ ads.
Putative brand safety classifications on various news sites
As mentioned earlier, some publishers appear to install Javascript from IAS on their websites that loads before any ads are served or any ad auctions occur. This publisher specific code is “cdn.adsafeprotected.com/iasPET.js”. The IAS Javascript is loaded directly from the publisher’s page rather than by any ad iframes. The IAS “iasPET.js” Javascript appears to initiate another HTTPS request to IAS’s servers, invoking a server endpoint called: “pixel.adsafeprotected.com/services/pub”.
IAS’s Brand Safety one sheet explains that IAS standard categories include: “Adult, Alcohol, Violence, Hate Speech, Offensive Language, Illegal Drugs, Illegal Downloads, Gambling”.

Screenshot of IAS’s Brand Safety one sheet. The document explains that IAS standard categories include: “Adult, Alcohol, Violence, Hate Speech, Offensive Language, Illegal Drugs, Illegal Downloads, Gambling”.
The IAS “pixel.adsafeprotected.com/services/pub” endpoint returns an HTTPS response, which includes a parameter called: “brandSafety”. This “brandSafety” parameter includes seven key-value pairs. The keys include:
“adt” (possibly a reference to adult content risk),
“alc” (possibly a reference to alcohol content risk),
“dlm” (possibly a reference to illegal downloadable material)
“drg” (possibly a reference to illegal drugs content risk)
“hat” (possibly a reference to hate speech content risk)
“off” (possibly a reference to offensive content risk)
“vio” (possibly a reference to violent content risk)
One can observe various “brandSafety” key value pairs relayed by IAS’s servers on various mainstream news, culture, and other types of websites.
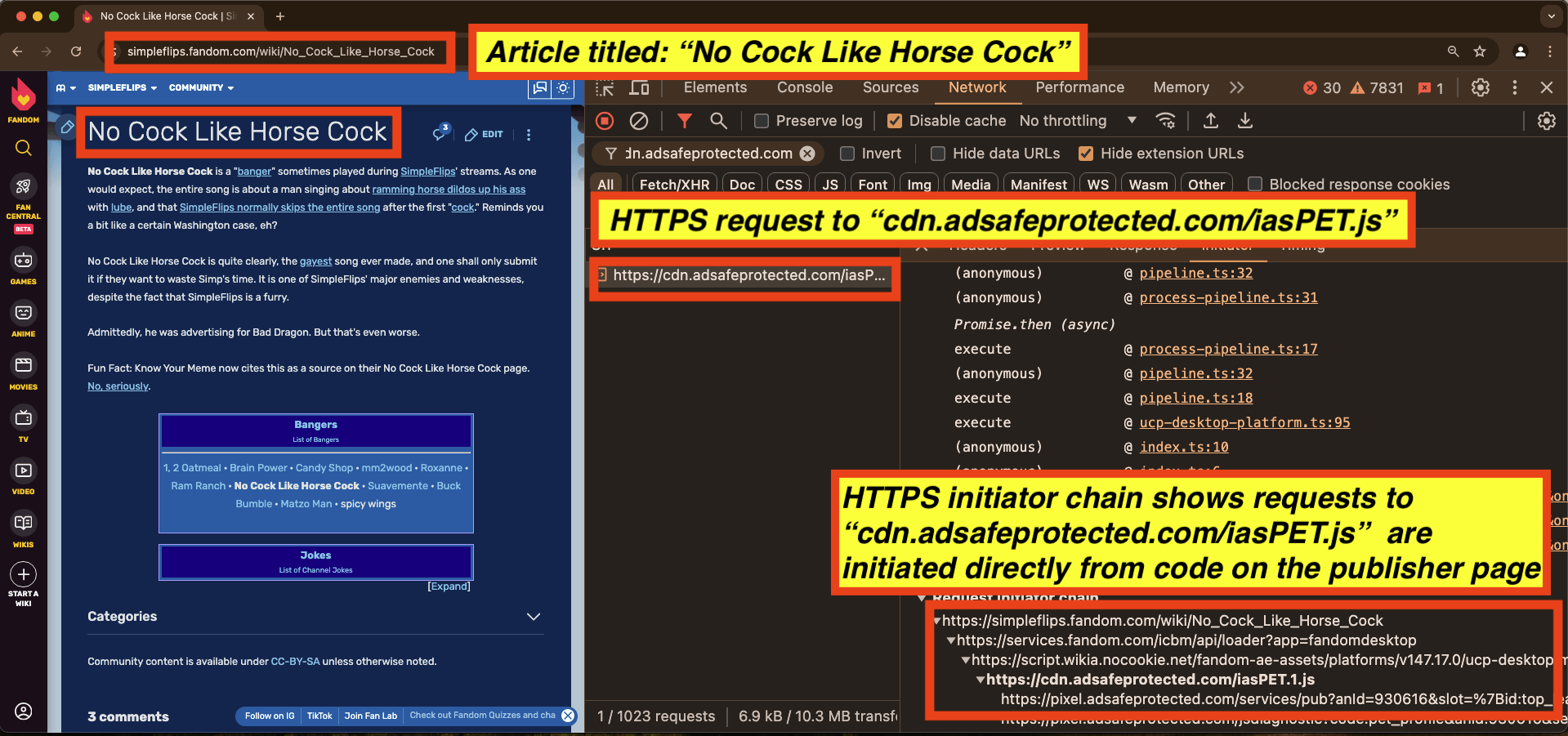
For example, the website scanner service URLScan.io crawled various pages over the course of several years and archived all the HTTP network traffic that was transmitted while the URLScan.io headless bot was visiting a given page. On May 3rd, 2024, the URLScan.io bot crawled and archived theroot.com. The Root is an “African American-oriented online magazine”, and describes itself as “Black News and Black Views”.
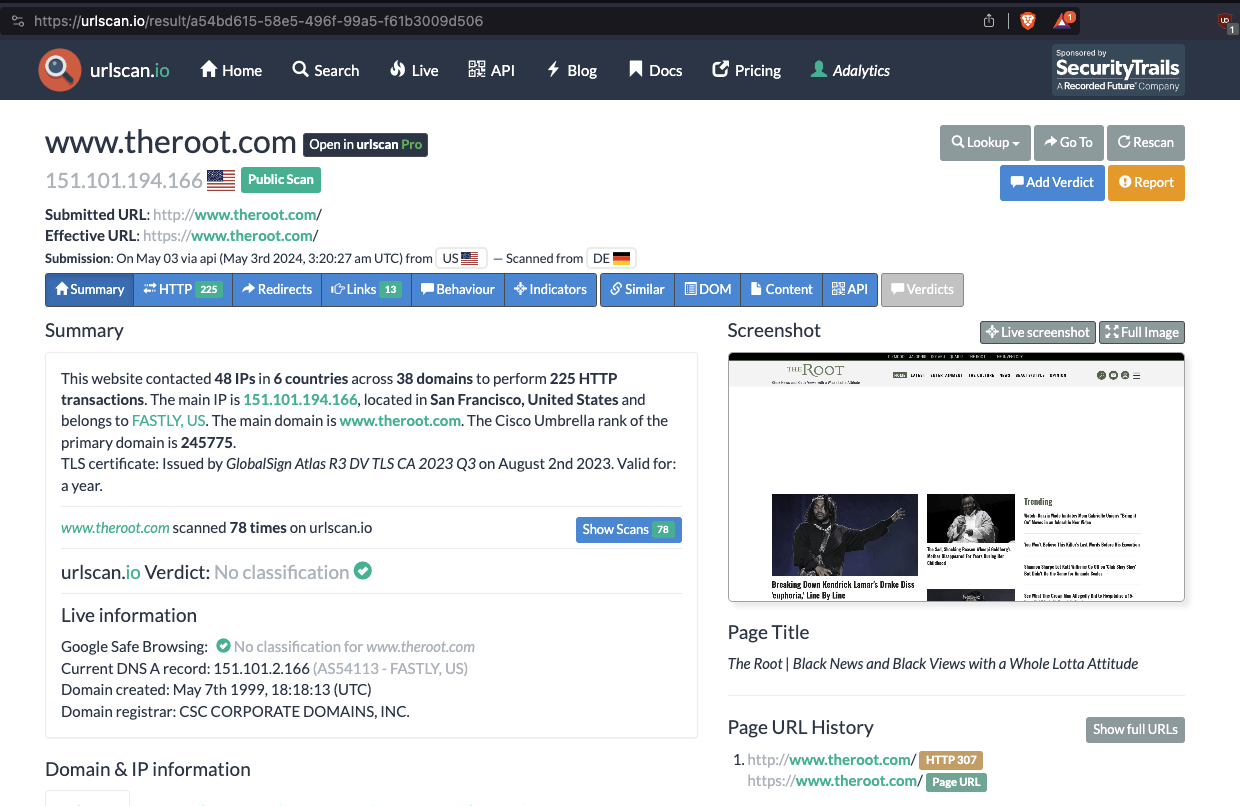
Screenshot of URLScan.io - showing a crawl and archiving of theroot.com on May 3rd, 2024. The Root is an “African American-oriented online magazine”.
If one clicks into the “HTTP” tab on this specific URLScan.io crawl from May 2024 on theroot.com, one can observe various HTTP requests and responses that were transmitted to the URLScan.io bot as it was crawling theroot.com. One of those HTTPS requests was an HTTPS request to “pixel.adsafeprotected.com/services/pub”.
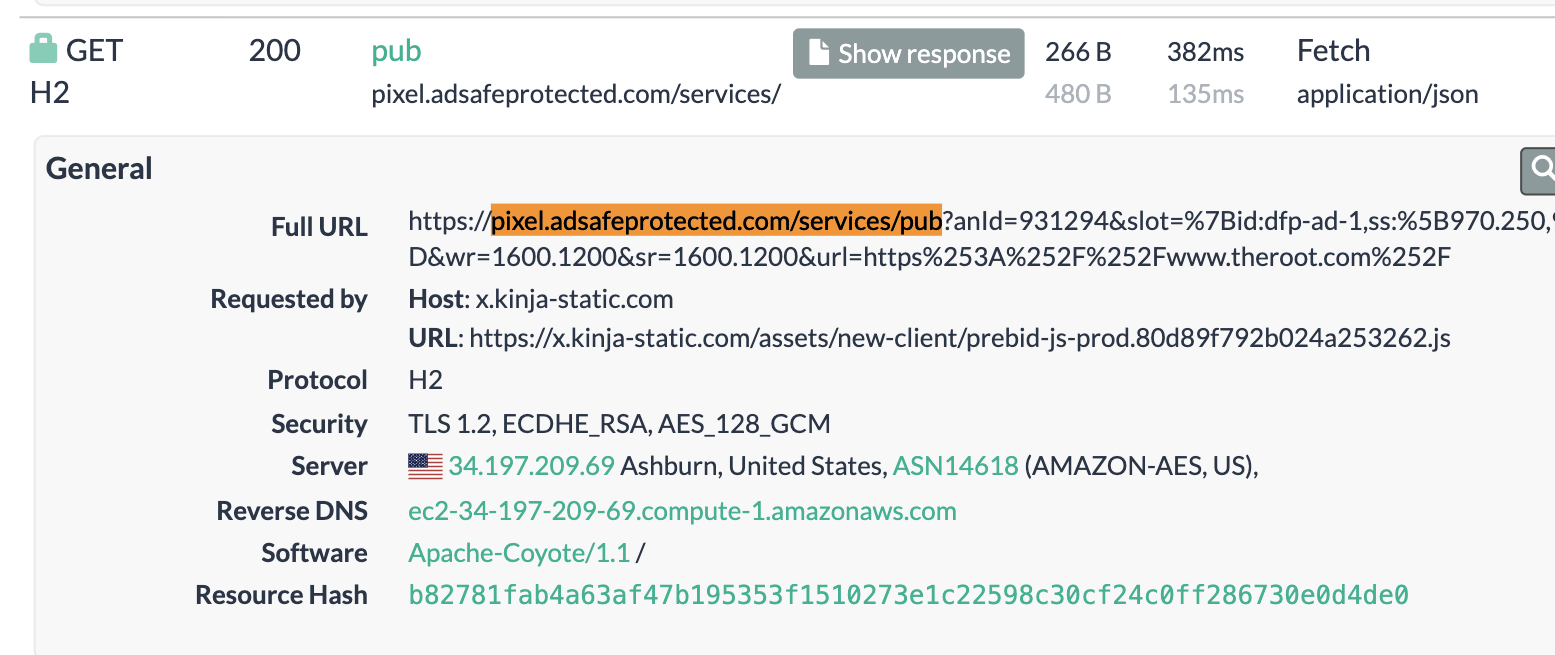
Screenshot of an HTTPS request to “pixel.adsafeprotected.com/services/pub” that was recorded by URLScan.io’s bot while crawling theroot.com on May 3rd, 2024.
One can click on the “Show response” button adjacent to this individual recorded HTTPS request, and see the specific HTTPS response payload that was transmitted from IAS’s server back to the browser before an ad auction ran while the URLScan.io bot was crawling theroot.com. This HTTPS response includes the “brandSafety” key value pairs in JSON format.
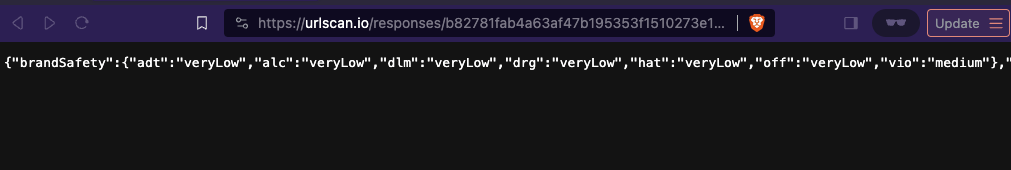
Screenshot of an HTTPS response payload from “pixel.adsafeprotected.com/services/pub” as the URLScan.io bot crawls the home page of theroot.com, an “African American-oriented online magazine”. The screenshot shows a JSON body with “brandSafety” key value pairs. The “vio” key is set to “medium” by IAS’s servers.
The screenshot of theroot.com’s homepage, overlaid with screenshots of the HTTPS request to and HTTPS JSON response from IAS’s “pixel.adsafeprotected.com/services/pub” endpoint, can be seen below.

Screenshot of URLScan.io’s bot crawling theroot.com (an “African American-oriented online magazine”) on May 3rd, 2024. The image is overlaid with screenshots showing HTTPS requests sent to ““pixel.adsafeprotected.com/services/pub” and an HTTPS response payload from “pixel.adsafeprotected.com/services/pub. The screenshot shows a JSON body with “brandSafety” key value pairs. The “vio” key is set to “medium” by IAS’s servers.
As another example, one can see below an overlaid screenshot of a CNN Business article about the Blue Origin rocket company unveiling a new space capsule. URLScan.io crawled this particular page on August 4th, 2023. The screenshot is overlaid with screenshots of the HTTPS request to and HTTPS JSON response from IAS’s “pixel.adsafeprotected.com/services/pub” endpoint, can be seen below. The IAS server endpoint returned a “brandSafety” JSON payload, where the “adt” key value pair is set to “high”.
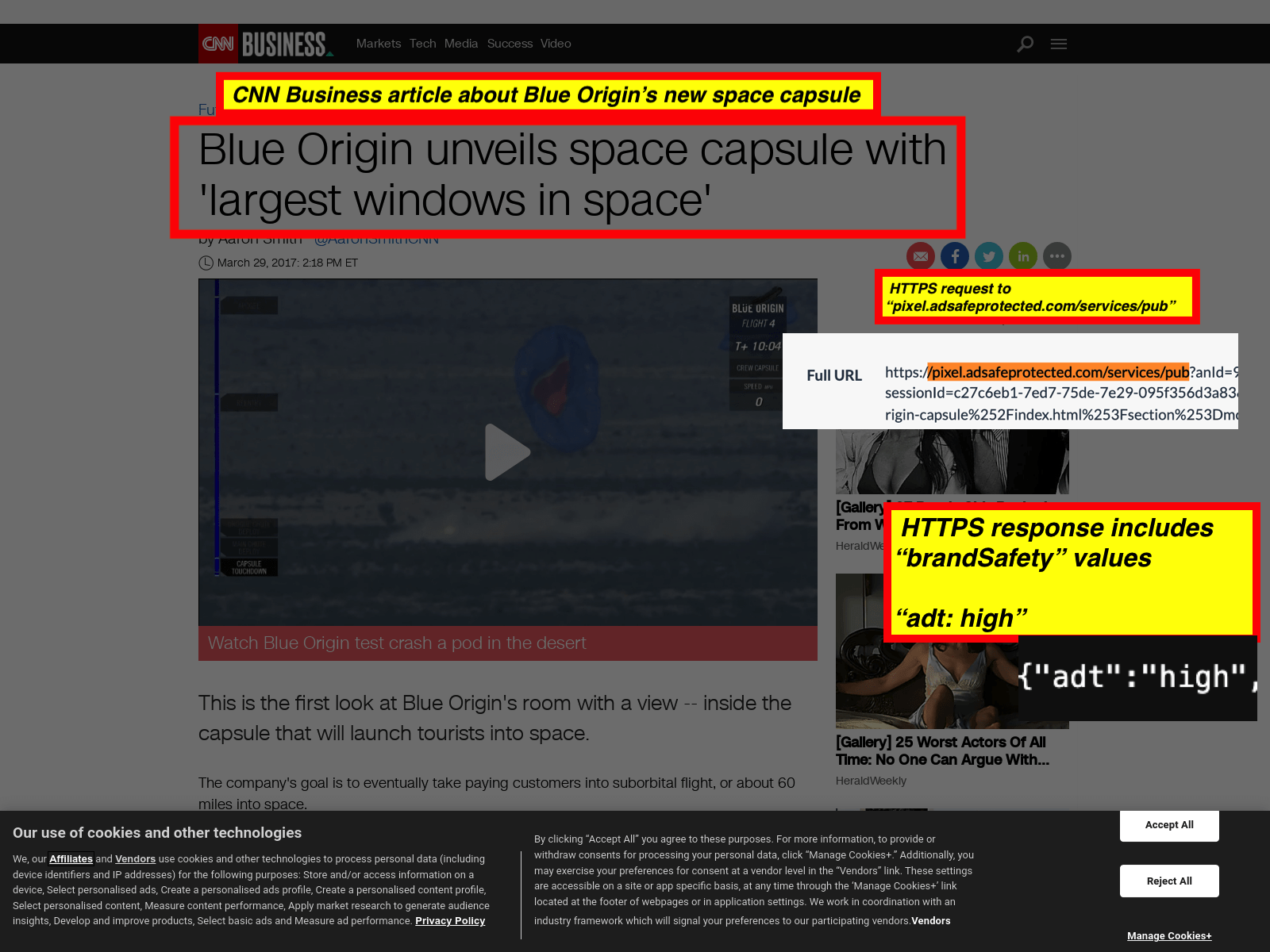
Screenshot of URLScan.io’s bot crawling a cnn.com about the Blue Origin space capsule on August 4th, 2023. The image is overlaid with screenshots showing HTTPS requests sent to “pixel.adsafeprotected.com/services/pub” and an HTTPS response payload from “pixel.adsafeprotected.com/services/pub”. The screenshot shows a JSON body with “brandSafety” key value pairs. The “adt” key is set to “high” by IAS’s servers.
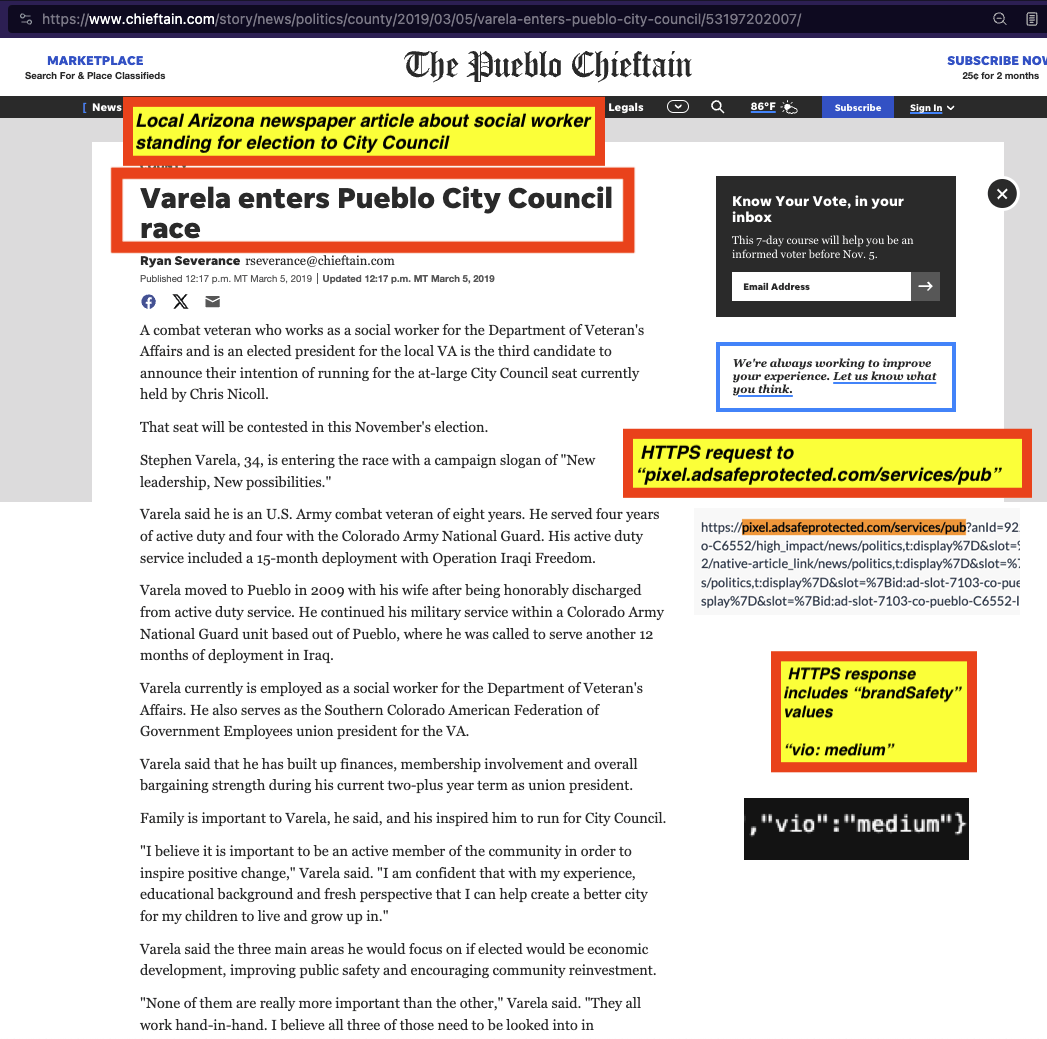
As a third example, one can see below an overlaid screenshot of a local newspaper in Pueblo, Colorado that is owned by Gannett Media. The local newspaper article discusses a US Army veteran running for election to Pueblo City Council. URLScan.io crawled this particular page on November 11th, 2023. One can see a screenshot below, wherein the screenshot is overlaid with screenshots of the HTTPS request to and HTTPS JSON response from IAS’s “pixel.adsafeprotected.com/services/pub” endpoint, can be seen below. The IAS server endpoint returned a “brandSafety” JSON payload, where the “vio” key value pair is set to “medium”.
As a fourth example, one can see a screenshot of an article from Reuters, discussing Apple’s antitrust lawsuit.. In the screenshot, one can see the HTTPS request to and HTTPS JSON response from IAS’s “pixel.adsafeprotected.com/services/pub” endpoint. The IAS server endpoint returned a “brandSafety” JSON payload, where the “hate” key value pair is set to “medium”.
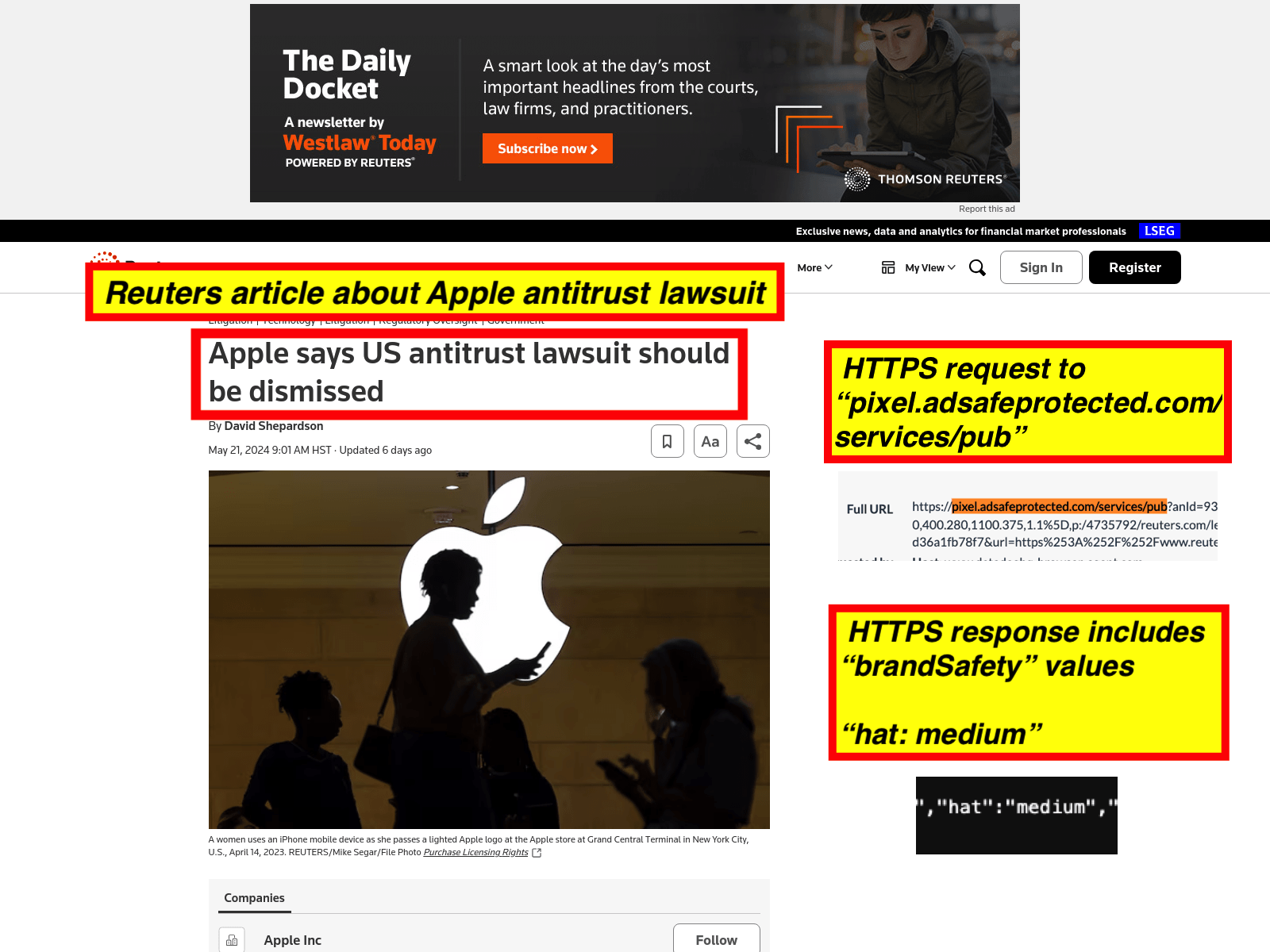
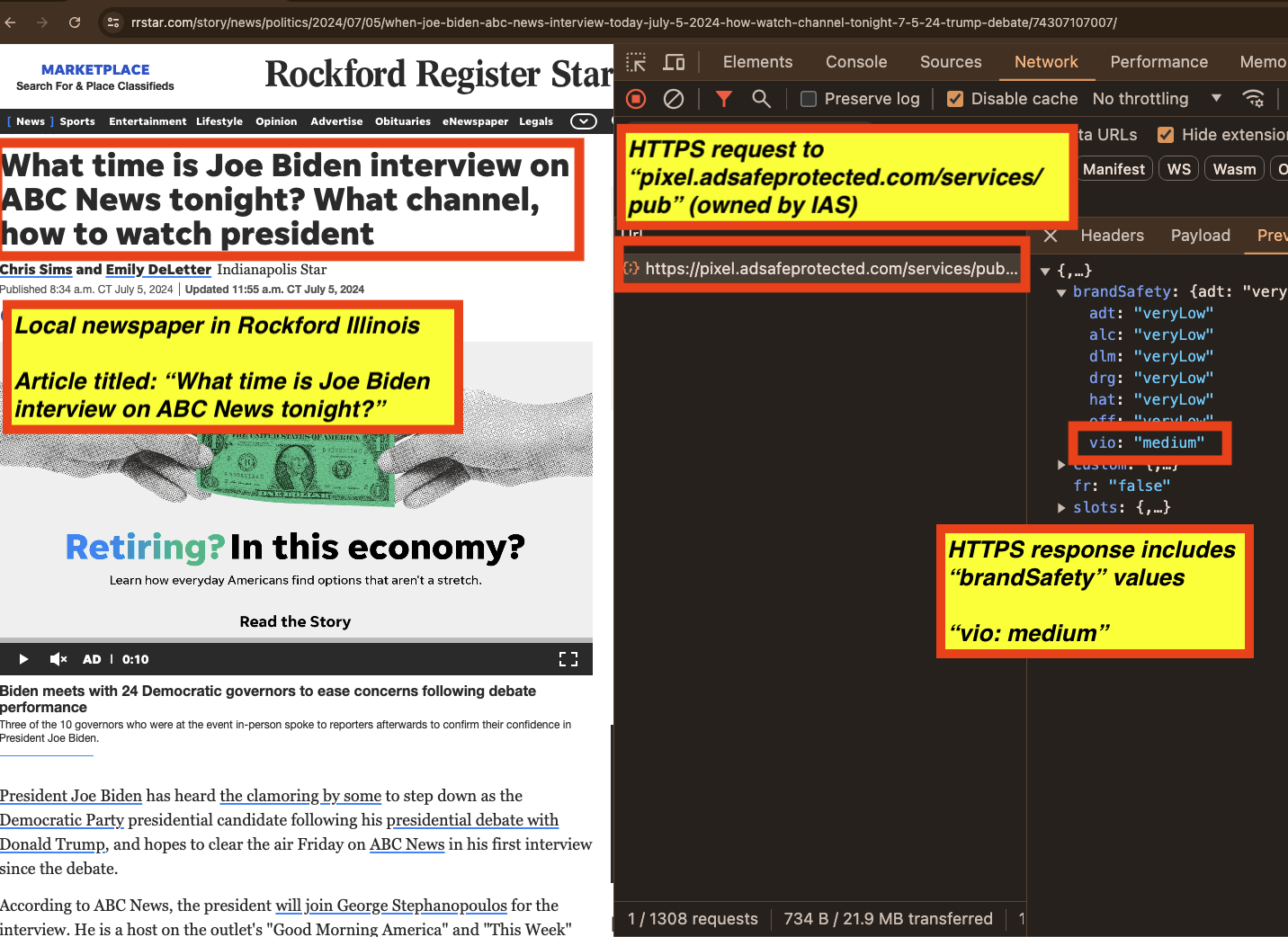
As a fifth example, one can see a screenshot of an article about Joe Biden’s interview on the Rockford Register Star, a local newspaper owned by Gannett Media, from July 2024. In the screenshot, one can see the HTTPS request to and HTTPS JSON response from IAS’s “pixel.adsafeprotected.com/services/pub” endpoint. The IAS server endpoint returned a “brandSafety” JSON payload, where the “vio” key value pair is set to “medium”.
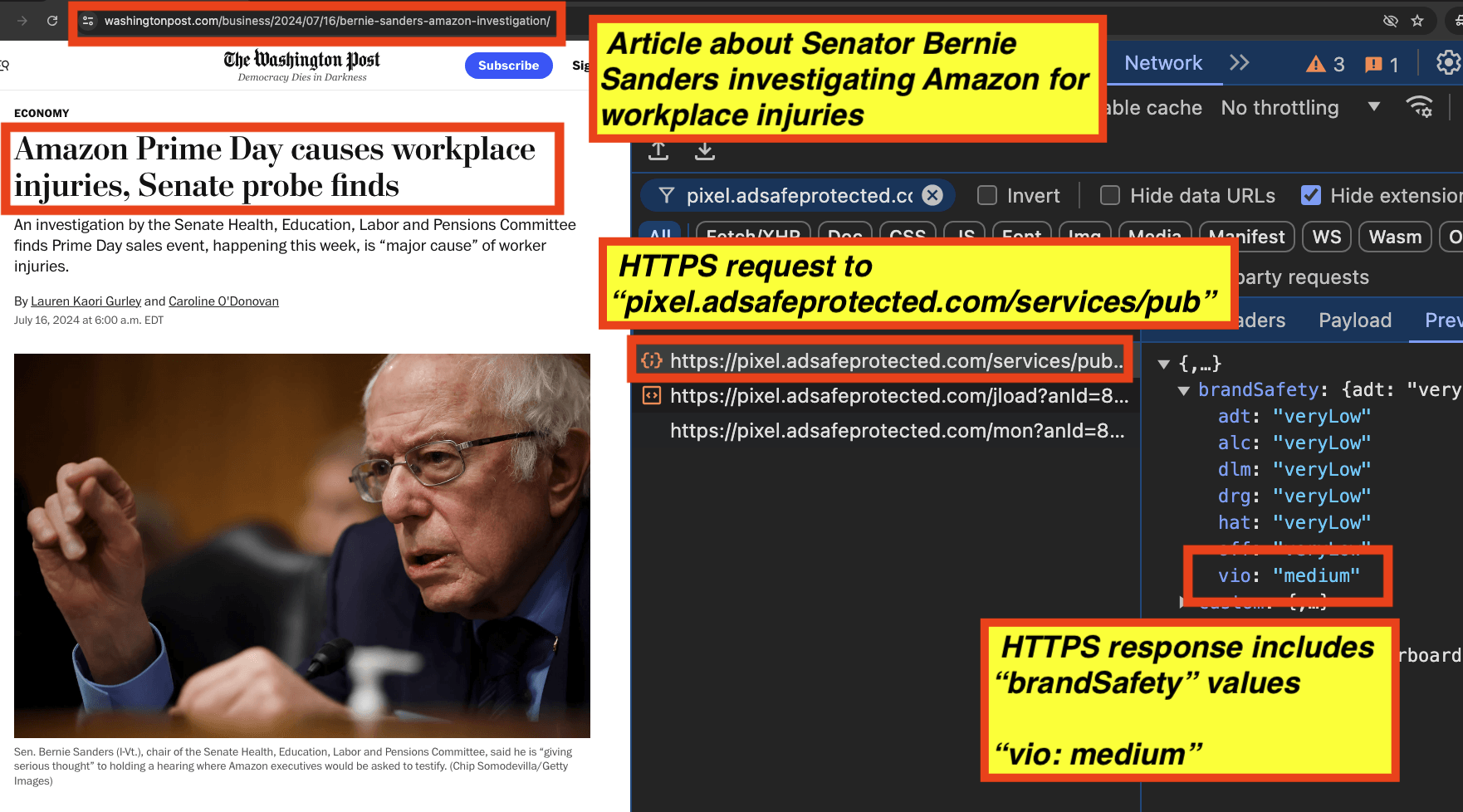
As a sixth example, one can see a screenshot of a Washington post article about Senator Bernie Sanders investigating workplace injuries. In the screenshot, one can see the HTTPS request to and HTTPS JSON response from IAS’s “pixel.adsafeprotected.com/services/pub” endpoint. The IAS server endpoint returned a “brandSafety” JSON payload, where the “vio” key value pair is set to “medium”.
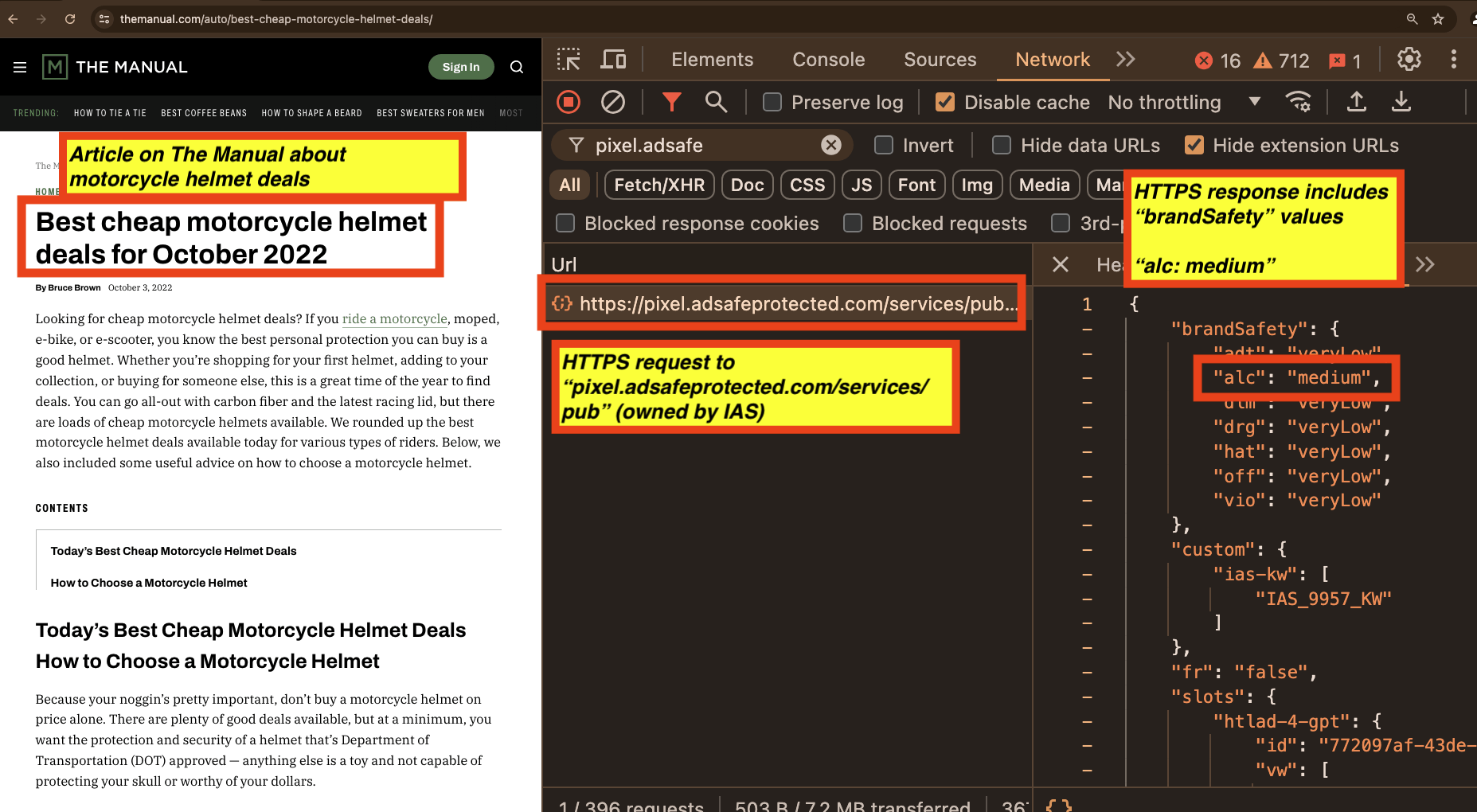
As a seventh example, one can see a screenshot of a The Manual article about best cheap motorcycle helmet deals. In the screenshot, one can see the HTTPS request to and HTTPS JSON response from IAS’s “pixel.adsafeprotected.com/services/pub” endpoint. The IAS server endpoint returned a “brandSafety” JSON payload, where the “alc” key value pair is set to “medium”.
As an eighth example, one can see a screenshot of a The Manual article about pumpkin spice lattes. In the screenshot, one can see the HTTPS request to and HTTPS JSON response from IAS’s “pixel.adsafeprotected.com/services/pub” endpoint. The IAS server endpoint returned a “brandSafety” JSON payload, where the “alc” key value pair is set to “medium”.
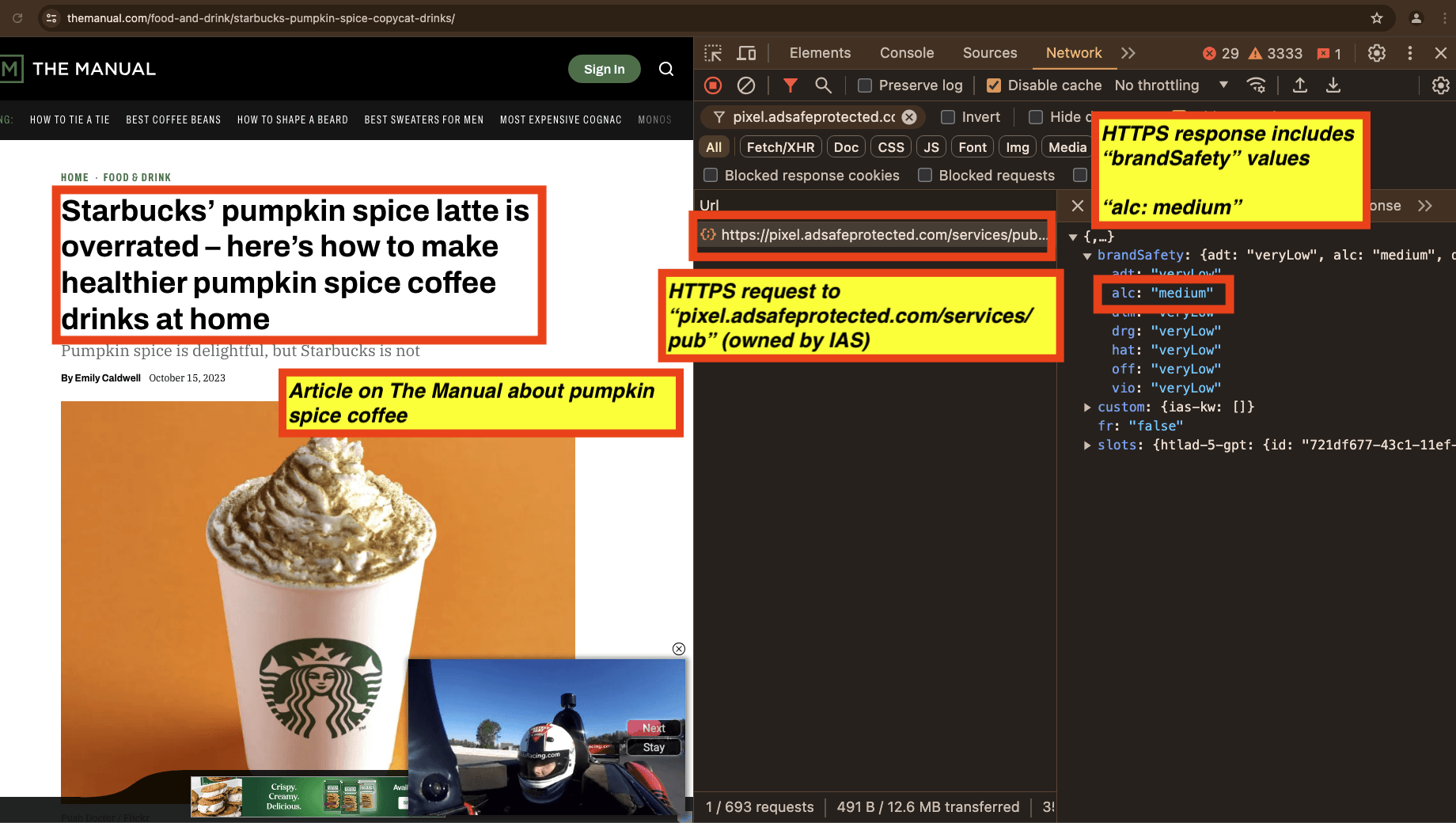
As a ninth example, one can see a screenshot of the homepage of Tripadvisor Switzerland (tripadvisor.ch). In the screenshot, one can see the HTTPS request to and HTTPS JSON response from IAS’s “pixel.adsafeprotected.com/services/pub” endpoint. The IAS server endpoint returned a “brandSafety” JSON payload, where the “adt” key value pair is set to “medium”.
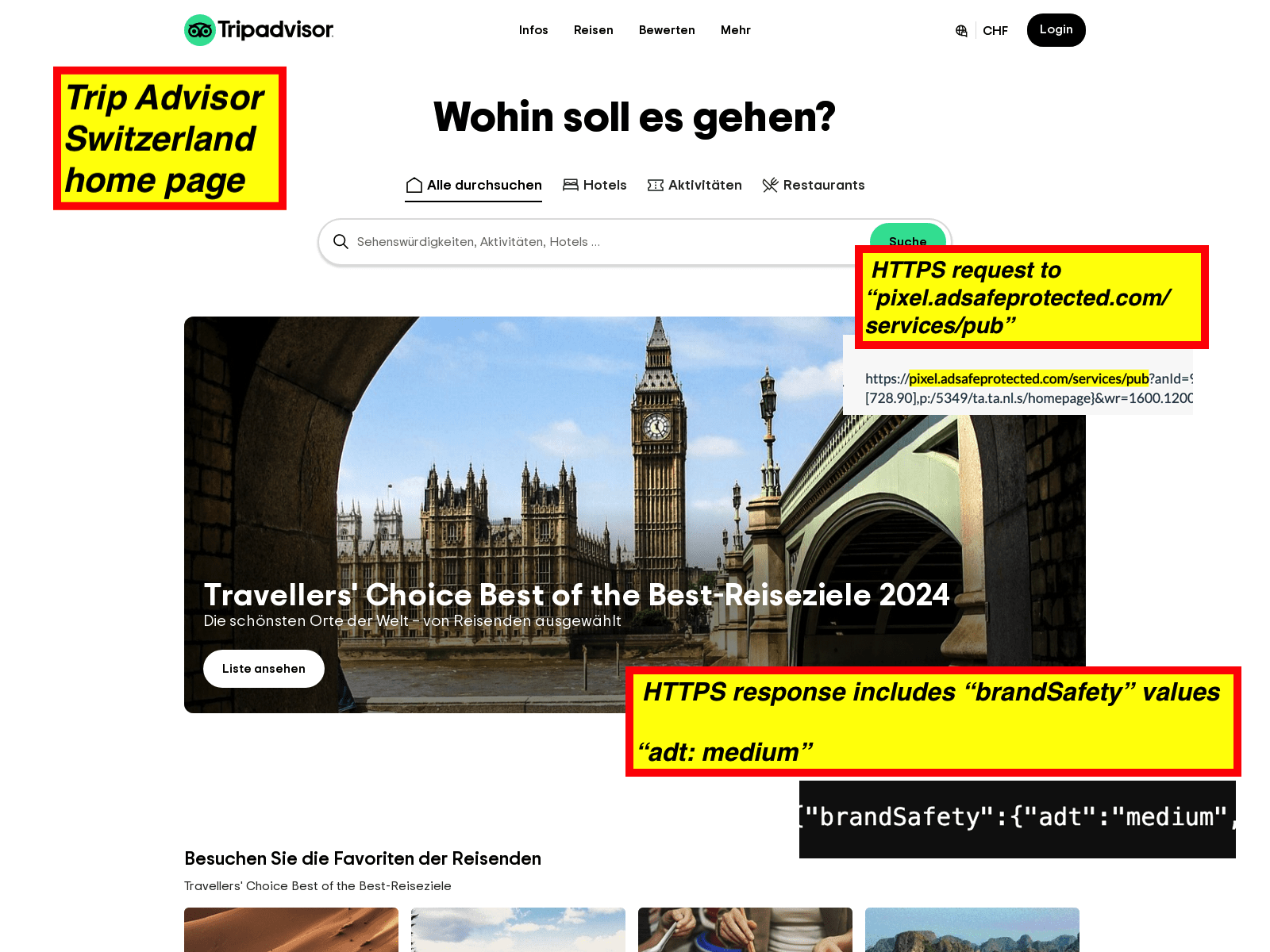
As a tenth example, one can see a screenshot of the home page of Vanity Fair, a Conde Nast owned publication. In the screenshot, one can see the HTTPS request to and HTTPS JSON response from IAS’s “pixel.adsafeprotected.com/services/pub” endpoint. The IAS server endpoint returned a “brandSafety” JSON payload, where the “vio” key value pair is set to “medium”.
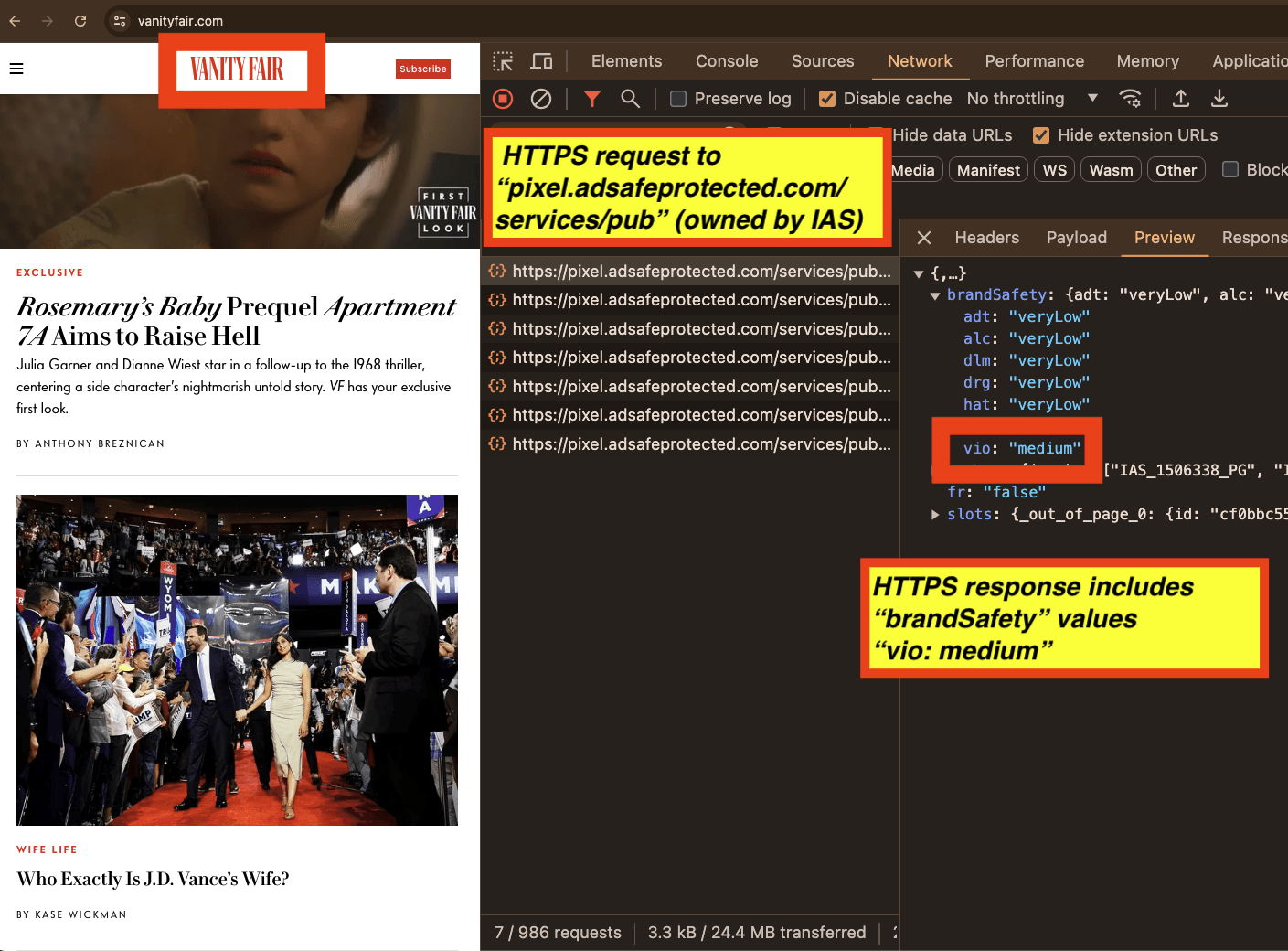
As an eleventh example, one can see a screenshot of the home page of the Washington Post. In the screenshot, one can see the HTTPS request to and HTTPS JSON response from IAS’s “pixel.adsafeprotected.com/services/pub” endpoint. The IAS server endpoint returned a “brandSafety” JSON payload, where the “vio” key value pair is set to “medium”.
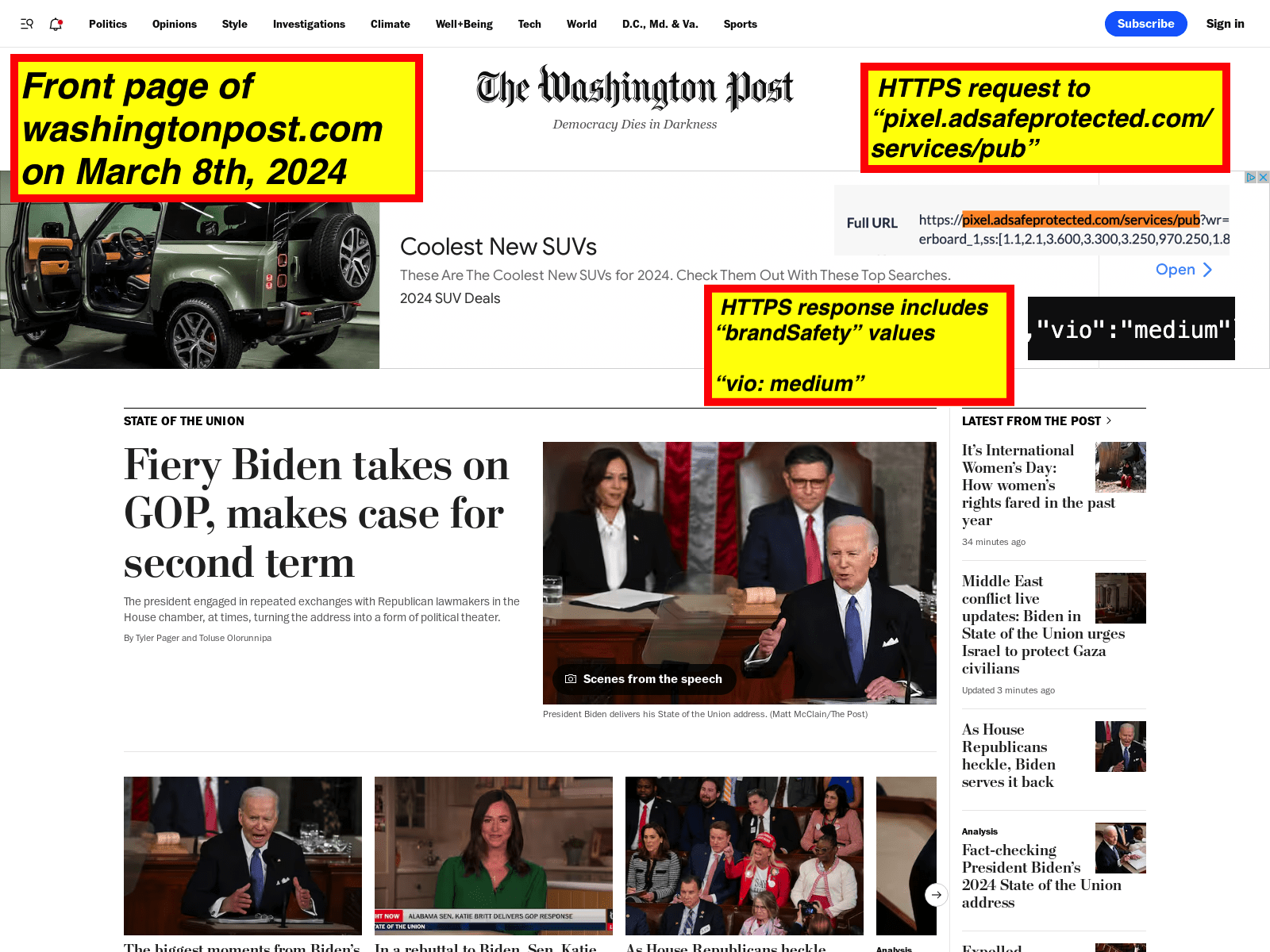
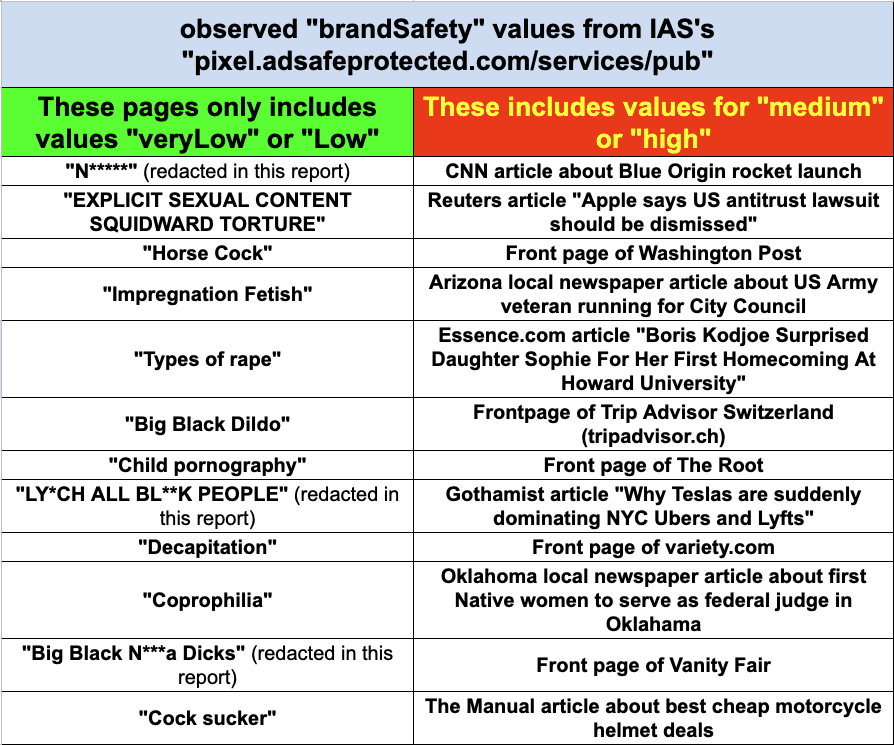
The front page of the Washington Post (https://www.washingtonpost.com/) appears to be labeled as “medium” or “high” for various “brandSafety” key value pairs from IAS at least once per month during many different months.
Between April 2023 and March 2024 (twelve months), URLScan.io archived the front page of the Washington Post as having “medium” or “high” key “brandSafety” values from IAS on ten various dates across ten different months. There were only two months in that time period where URLScan did not record a “medium” or “high” “brandSafety” value from IAS for the front page of the Washington Post.
Specifically:
April 2023 - “vio: medium” - https://urlscan.io/result/4a4e688b-9ac3-4bdf-890e-f7d016da439a
May 2023 - No observed instances of “medium” or “high” “brandSafety” key value pairs on the home page of washingtonpost.com observed by URLScan.io in May 2023
June 2023 - “vio: medium” - https://urlscan.io/result/bb05e1ee-7cf4-4168-ac74-a64c3bacde22
July 2023 - “vio: medium” - https://urlscan.io/result/8210870d-72b2-4c56-acc1-54653fd8c5e4
August 2023 - “vio: medium” - https://urlscan.io/result/32599bea-1d0b-41b5-9624-c77df1a6a0a9
September 2023 - No observed instances of “medium” or “high” “brandSafety” key value pairs on the home page of washingtonpost.com observed by URLScan.io in September 2023
October 2023 - “vio: medium” - https://urlscan.io/result/8e949db1-9e9c-47ef-a3cb-a0264d85e00e
November 2023 - “vio: medium” - https://urlscan.io/result/1b04497e-57ad-4b60-8c92-4a5f2f5f2322
December 2023 - “vio: medium” - https://urlscan.io/result/b8e49022-842a-4d3b-b0a9-0e0547431dd6
January 2024 - “vio: medium” - https://urlscan.io/result/defda5de-3e25-432f-9f9c-6cbcbdf8ee33
February 2024 - “vio: medium” - https://urlscan.io/result/e6d1a2f5-d925-4b7a-95bf-5440d468534e
March 2024 - “vio: medium” - https://urlscan.io/result/d2821f4a-b68e-43a9-9285-61cdf9f5f6ff
One can see several different examples of “brandSafety” key value pairs from IAS’s “pixel.adsafeprotected.com/services/pub” endpoint on various pages below.
Conclusion
Caveats & limitations
Interpreting the results of this observational study requires nuance and caution.
This observational study makes no assertions with regards to the actual knowledge or intent of any parties observed or cited in this study. The study cannot comment on whether any phenomenon, such as specific ad placements, occurred for some specific reason. It is at least theoretically possible that various observed ad placements were entirely within the desired specifications of various media buyers and their technology vendors.
Furthermore, the study uses client-side digital forensics to observe various query string parameters and other references within ad source code. However, this methodology can be prone to false positives in the case of low entropy strings, ad ops and trafficking errors, or other situations where a string references something other than what was inferred or deduced. As such, media buyers and vendors are encouraged to evaluate the observations in this study by examining their own logfile data.
The study relied entirely upon publicly accessible or available data; it made use of no proprietary or internal data on how ads are placed or paid for. Because the study was entirely based on browser client-side observations, it is unable to deduce if there are any post-ad impression reconciliations or corrections that take place. For example, it is possible that if a brand safety vendor, SSP, or DSP detected that an ad was served improperly, they could block any monetary value from changing hands.
This study used a convenience sample of data that was readily obtainable. However, it cannot deduce the relative or absolute abundance of certain phenomena observed in this study. It is theoretically possible that the phenomena observed in this study constitute only a small percentage of ad transactions for a given vendor.
Brands and ad tech entities are encouraged to audit their own media buys to analyze how much each entity transacted with any given vendor and whether the ad delivery via that vendor was consistent with their expectations.
Caveats & Limitations - Questions & Answers (Q&A)
Does this study make any assertions with regards to quantitative impact?
No. This study does not make any assertions with regards to quantitative impact. For example, this study does not quantify how many ads were served on potentially objectionable content, or what relative number of media buyers who utilized specific technologies had their ads served on potentially objectionable content. This study makes no assertions with regards to the specificity, sensitivity, or quantitative accuracy of any content classification technologies.
Some brand marketers specifically informed Adalytics that they have a “zero impression” tolerance level for having their ads served adjacent to some of the content identified in this study. Other media buyers may have different tolerance thresholds and brand safety requirements.
Does this study make any assertions that brands who paid for brand safety technology had their digital ads served on potentially objectionable content?
No - every single brand and media buyer may have a different set of marketing objectives and brand safety values. Some media buyers may find some content objectionable, whilst other media buyers may specifically be seeking out and intending to have their ads served on specific content. Whether or not a specific piece of content is “objectionable” or “brand unsafe” is a subjective matter which will vary with each media buyers’ intentions and specifications. As such, this study cannot assert whether or not brands had their ads served on content that each individual brand might consider objectionable or desirable.
The IAB states that “content that contains hate speech directed at a protected class would be inappropriate for any advertising”.
Some brand marketers specifically informed Adalytics that they have a “zero impression” tolerance level for having their ads served adjacent to some of the content identified in this study, as they would consider it to be highly objectionable. Other media buyers may have different tolerance thresholds and brand safety requirements.
Does this study assert that large numbers of ads were served on potentially objectionable content?
No. This study does not make any assertions with regards to how many ads or what proportion of various ad buys were served on potentially objectionable content.
The IAB states that “content that contains hate speech directed at a protected class would be inappropriate for any advertising”.
Some brand marketers specifically informed Adalytics that they have a “zero impression” tolerance level for having their ads served adjacent to some of the content identified in this study. Other media buyers may have different tolerance thresholds and brand safety requirements.
Does this study recommend that media buyers exclude or block specific publishers from future ad buys?
No. This study does not recommend or advise any media buyers to exclude or block specific publishers from future ad buys. Each media buyer may wish to review their own ad buy records, their internal brand safety requirements, and make their own informed decisions with regards to whether or not to continue to transact with any specific media publisher.
This study does not make any quantitative assessment or assertions with regards to how much potentially objectionable ad inventory is transacted by any given publisher.
Does this study assert that any specific media publishers are “at fault” for specific potentially objectionable ad placements?
No. This observational research study makes no assertions with regards to fault, intent, or causality.
Does this study allege that brands, vendors, or media agencies intentionally placed digital ads on objectionable content?
No. This observational research study makes no assertions with regards to fault, intent, or causality.
Does this study allege that any vendors intentionally mis-classified news content, user-generated content, or objectionable content?
No. This observational research study makes no assertions with regards to fault, intent, or causality.
Does this study recommend that media buyers stop using brand safety technology ?
No. This observational research study does not recommend or advise that any media buyers cease or continue to use brand safety technology. Each media buyer may wish to review their own ad buy records, their internal brand safety requirements, and make their own informed decisions with regards to whether or not to continue to transact with any specific brand safety technology vendor.
This report primarily cites observations from one publisher - Fandom.com. Are all examples of brands ads appearing on potentially objectionable content tied to this one specific publisher?
No. During the course of this observational research study, brands which appear to possibly be using brand safety technology had their ads observed on other, non-Fandom websites, which include potentially objectionable content. For example, brands ads were observed on non-Fandom pages discussing explicit adult content topics, racial slurs, and violent acts.
Some media buyers who wish to avoid their ads appearing next to racial slurs or adult content topics may simply add Fandom.com to an exclusion list. Is this sufficient to prevent their ads from appearing next to racial slurs or adult content topics?
No. Firstly, this study does not make any recommendations as to whether or not media buyers should continue to transact with any specific publisher. Secondarily, this study noted other, non-Fandom.com publishers which also had content featuring racial slurs or adult content topics, and noted that brands ads were appearing on those other, non-Fandom.com pages. Media buyers may desire to execute a detailed, holistic analysis of their media investments, rather than simply excluding a single publisher based on a few examples cited in this observational report.
Are the observations of brands’ ads next to racial slurs and adult content isolated to one publisher - Fandom.com ?
No. During the course of this study, brands ads were observed on other, non-Fandom.com publishers which had content featuring racial slurs and adult content topics.
Discussion
This study documents empirical observations where multiple international brands which appear to utilize solutions from various “AI powered” vendors had their ads served adjacent to content such as “dick”, “dildo”, “LY*CH ALL B***K PEOPLE” (redacted in this report), and "N*****" (redacted in this report). The IAB states that “content that contains hate speech directed at a protected class would be inappropriate for any advertising”.
Multiple multinational brands which spend millions of dollars per year on brand safety tech expressed concern privately to Adalytics regarding the placement of their digital ads adjacent to some of this content. These brands alleged that they use pre-bid brand safety technology, post-bid brand safety technology, and keyword blocking. Some of the brands claimed to block “user-generated content”.
The brands expressed concerns and questioned how - despite their significant financial investment into various technologies - their ads could appear on specific pages where the page URLs and plain text on the page itself encoded some of the excluded keywords.
Multiple brand marketers asked Adalytics: “How is this possible?”.
Adalytics was unable to answer these brand marketers questions, with regards to how - despite brands allegedly paying millions of dollars for pre-bid brand safety tech, post-bid brand safety tech, and keyword blocking tech - the brands had their ads served on pages such as "N*****" (redacted in this report), “No Cock Like Horse Cock”, “Big black n***a dicks” (redacted in this report),“Gag Penis”, and “LY*CH ALL B***K PEOPLE” (redacted in this report).
One marketer noted that it is ostensibly possible that the brands or their media agencies mis-configured the brand safety technology. For example, the marketer said it is possible that brands paid for brand safety technology, but used very permissive settings or did not activate specific keyword exclusion lists on specific ad campaigns.
This study observed hundreds of different major brands and multiple agency holding companies - such as IPG, GroupM/WPP, Omnicom, and Publicis - having their ad campaigns served on “potentially objectionable content”. As such, one might question whether setup or tool configuration issues are entirely responsible for some potentially un-desired ad placements.
Some brand safety vendors' materials allege that they utilize “Real-time processing” and “AI/ML enrichment”.

IAS materials reference “AI/ML enrichment” and “Real-time processing”. Source: Integral Ad Science (IAS) May 2024 Investor Presentation

IAS materials reference “AI/ML” data enrichment and “Real-time data processing”. Source: Integral Ad Science (IAS) May 2024 Investor Presentation

Source: https://integralads.com/insider/cannes-lions-2024-recap/

Source: https://integralads.com/insider/cannes-lions-2024-recap/
Some marketers expressed interest in understanding how various “AI/ML” and “real-time data” solutions may influence the ability to adjudicate ad placements on content such as “anal sex”, “no cock like horse cock”, “LY*CH ALL B***K PEOPLE” (redacted in this report) or "N*****" (redacted in this report). The IAB states that “content that contains hate speech directed at a protected class would be inappropriate for any advertising”.
The European Commission's “Strengthened Code of Practice on Disinformation 2022”, specifically states that:
“Brand safety tool providers and rating services who categorise content and domains will provide reasonable transparency about the processes they use, insofar that they do not release commercially sensitive information or divulge trade secrets, and that they establish a mechanism for customer feedback and appeal.”

Screenshot from the European Commission's “Strengthened Code of Practice on Disinformation 2022”
The United States Department of Commerce National Institute of Standards & Technology (NIST) is the US Federal AI Standards Coordinator. NIST “aims to cultivate trust in the design, development, use,and governance of Artificial Intelligence (AI) technologies and systems in ways that enhance safety and security.”
NIST states that some of the essential building blocks of AI trustworthiness include: “Accountability and Transparency“ and “Explainability and Interpretability”. The NIST AI RIsk Management Framework states “Characteristics of trustworthy AI systems include: valid and reliable, safe, secure and resilient, accountable and transparent, explainable and interpretable, privacy-enhanced, and fair with harmful bias managed.”
Screenshot of the NIST AI Risk Management Framework discussing “Characteristics of trustworthy AI systems”
The NIST AI RIsk Management Framework states that: “Inscrutability: Inscrutable AI systems can complicate risk measurement. Inscrutability can be a result of the opaque nature of AI systems (limited explainability or interpretability), lack of transparency or documentation in AI system development or deployment, or inherent uncertainties in AI systems.”

Screenshot of the NIST AI Risk Management Framework discussing “Inscrutable AI systems”
In 2020, IAS launched “Context Control” - a “sophisticated new suite of brand safety & suitability solutions”. It also launched its “Context Control” demo, inviting users to test the technology behind Context Control. A non-profit tested the demo tool in August 2020, publicized its observations, and the demo was allegedly removed the “next day”.
Several media buyers reported that they do not receive access to page URL level brand safety classification or reporting from their brand safety vendors. For example, while the brands may have the ability to see how many ads were labeled as brand unsafe on “example.com”, they lack the ability to see how many ads were served on “https://subdomain.example.com/offensive-keyword”.
As such, these brands were unable to independently investigate or quantify how many of their ads were served on page URLs which contain “potentially objectionable content”, and how whether or not their AI powered brand safety solutions were accurately classifying content.

Publishers and brand marketers may be interested in reviewing thought leadership from NIST and the European Commission regarding transparency and explainability regarding AI technology.
Furthermore, brand marketers may be interested in having discussions with their media supply chain vendors and AI technology vendors to obtain sufficiently detailed page URL level data to allow independent adjudication of the accuracy of AI technologies.
One Fortune 500 brand marketer stated:
“The facts uncovered in this research make something alarmingly clear – not only does full URL transparency for advertisers need to be adopted immediately by all DSPs, but also the brand safety & verification technologies that claim to have been providing URL & Page level protection have been nothing short of insufficient and need to immediately review and update their tools to actually include full URL data and properly classify content to protect brands as well as publishers. If this is not addressed, we will not allow our brand dollars to flow through a DSP, tagged with a Verification Provider that allows delivery to a page titled “L*NCH ALL ***** PEOPLE”. Completely unacceptable.”
Another Fortune 500 brand marketer stated:
“Is verification tech implemented correctly but not working? If so huge problem. Does not seem to be doing any page level scanning. Ultimately, advertisers want 100% of their ads to be in safe, suitable, viewable environments delivered to real consumers. Currently that is almost impossible to do at scale.”
A third Fortune 500 brand marketer stated:
“The problem with issues like this is that I can't actually verify my company's degree of exposure because none of the platforms we activate on or use for brand safety provide us with URL level reporting capabilities out of the box. But beyond that, it's not even that a level of exposure matters, it's that exposure itself is a line in the sand I don't want to cross. If I have served an ad on a URL containing "big black cock", what's to say that an ad didn't end up on a URL that contains the string "little boy cock", which I can't now just magically assume hasn't happened."
Key questions for brand marketers
Brand marketers may wish to ask various specific questions to their vendors to better understand the vendors’ technology and functionality. Some questions may include:
Can brands get page URL level reporting and classifications, to independently validate the statistical performance of vendors' classifier models?
What is the temporal latency with which vendors crawl, classify, and deploy the classifications of specific content? For example, if an article is published on Monday at 9:00 AM, when will a vendor have crawled, classified, and deployed their classifications for that article to a DSP? Will it be within 5 minutes, 5 hours, 5 days, or 5 weeks? Can vendors see this temporal latency on a page URL basis ?
Do vendors analyze all content on which brands' ads appear, or do they sample - for example, only examining content for which at least 100,000 impressions have been served on?
Do vendors look at data on a domain, sub-domain, or page URL basis ? For example, for a publisher with 13,000 articles, will the vendors crawl and classify every single article?
How do vendors extract data to power their classifications? Do they only use page URLs, meta html tags, image/video meta tags, or fully body text? If the latter, do the vendors' crawlers render the full DOM of a page, including the parts of a page that are only visible with fully Javascript rendering such as in Single Page Application (SPA) pages that use frontend frameworks such as React?
How do vendors handle crawling pages which use anti-crawler defenses, such as subscriber paywalls, re-captchas, or Cloudflare bot firewalls?
Do vendors have the ability to check page URLs declared in ad auctions in real time?
What are the statistical sensitivity and specificity of vendors' classifier models?
