Introduction
When Elon Musk bought Twitter, he also bought a treasure trove of internet traffic data from websites like Reddit, NYTimes.com, Amazon.com, studentaid.gov (Department of Education’s Free Application for Federal Student Aid), and the website of Democratic Congressional Campaign Committee (dccc.org).
Government agencies, hospitals, over half of all US members of Congress, media publishers, and brands may not be aware that they are sharing terabytes of their visitors’ and audiences' data with Twitter.
The vast majority of these entities have not enabled Twitter's Restricted Data Usage (RDU) feature to set legal guardrails around what Twitter can do with that web traffic data.
On October 27th, 2022, Elon Musk completed an acquisition of Twitter. Some US Senators expressed national security concerns over how the deal was financed with capital from foreign investors, such as a holding company partly owned by Saudi Arabia’s sovereign wealth fund.
On November 1st, 2022, the Washington Post reported that:
“Experts on the foreign review process said of particular interest will probably be whether any of Musk’s foreign investors would have special privileges to access personal data about Twitter’s users. According to people familiar with Musk’s purchase of Twitter, those who invested $250 million or more have access to information beyond what a lower-level investor would receive. The Saudi and Qatari funds and Binance have invested above that level. But what that additional access includes is not known.” (emphasis added)
In the past, Twitter has suffered numerous data breaches, foreign espionage infiltration, been fined repeatedly by the FTC for consumer privacy violations, and has recently lost significant portions of its cybersecurity and regulatory personnel.
Over the next few weeks, several major brands and media agencies stated they would stop advertising on Twitter. On November 28th, Elon Musk tweeted that “Apple has mostly stopped advertising on Twitter”, a claim which was contested by ad analytics firm Pathmatics, whose data showed that Apple had continued to spend heavily on Twitter ads.
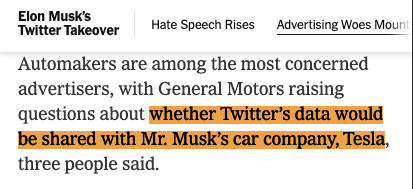
The New York Times reported on Dec. 2nd that "automakers are among the most concerned advertisers, with General Motors raising questions about whether Twitter’s data would be shared with Mr. Musk’s car company, Tesla, three people said." “It’s important for us to ensure our advertising strategies and data can be safely managed by a platform owned by a competitor,” a G.M. spokesman said in a statement.
 Screenshot of a quote from The New York Times.
Screenshot of a quote from The New York Times.Motivated by these and other events, Adalytics chose to use a different methodology to assess which brands and entities may still consider advertising on Twitter despite their public proclamations. This analysis focuses on both privacy implications and potential cybersecurity risk.
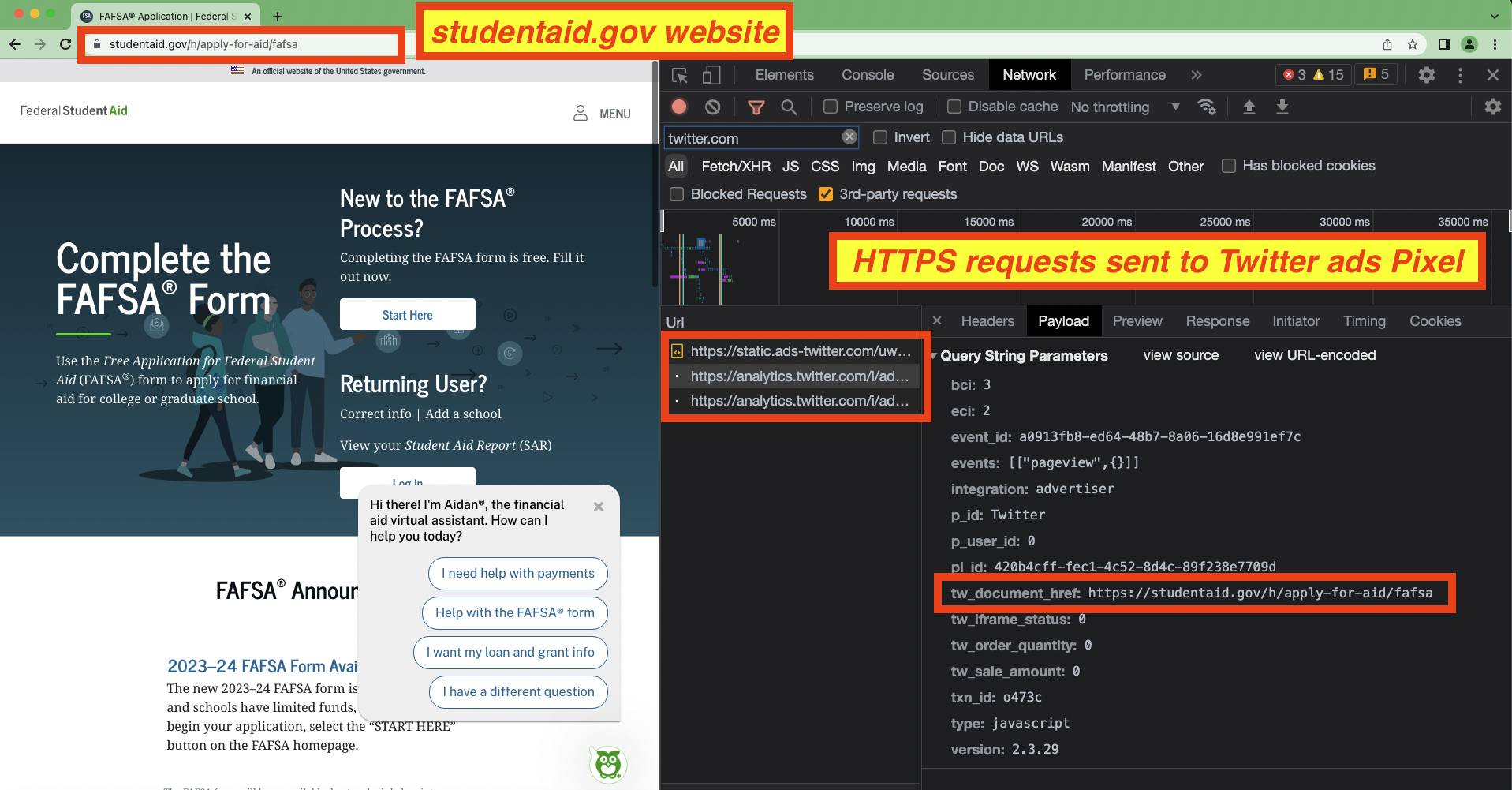
Adalytics analyzed web crawler data from hundreds of thousands of websites to determine which websites are still hosting Twitter’s advertising pixel. At least 70,772 websites were observed using Twitter’s advertising Pixel on their pages. Many brands that made public statements about suspending digital ads on Twitter - such as General Motors, Mondelez, Pfizer, and Volkswagen - continue to host the Twitter Pixel on their websites, which enables Twitter to collect information about visitors to these brands’ webpages. It appears that the vast majority of advertisers that use the Twitter pixel are not using the pixel’s “Restricted Data Use” privacy feature. Surprisingly, Apple (Twitter's biggest advertiser by spend) and Elon Musk’s own companies - SpaceX and Tesla - do not appear to host the Twitter Pixel on their websites. This is despite SpaceX recently ordering one of the larger advertising packages available on Twitter around November 14th, 2022.
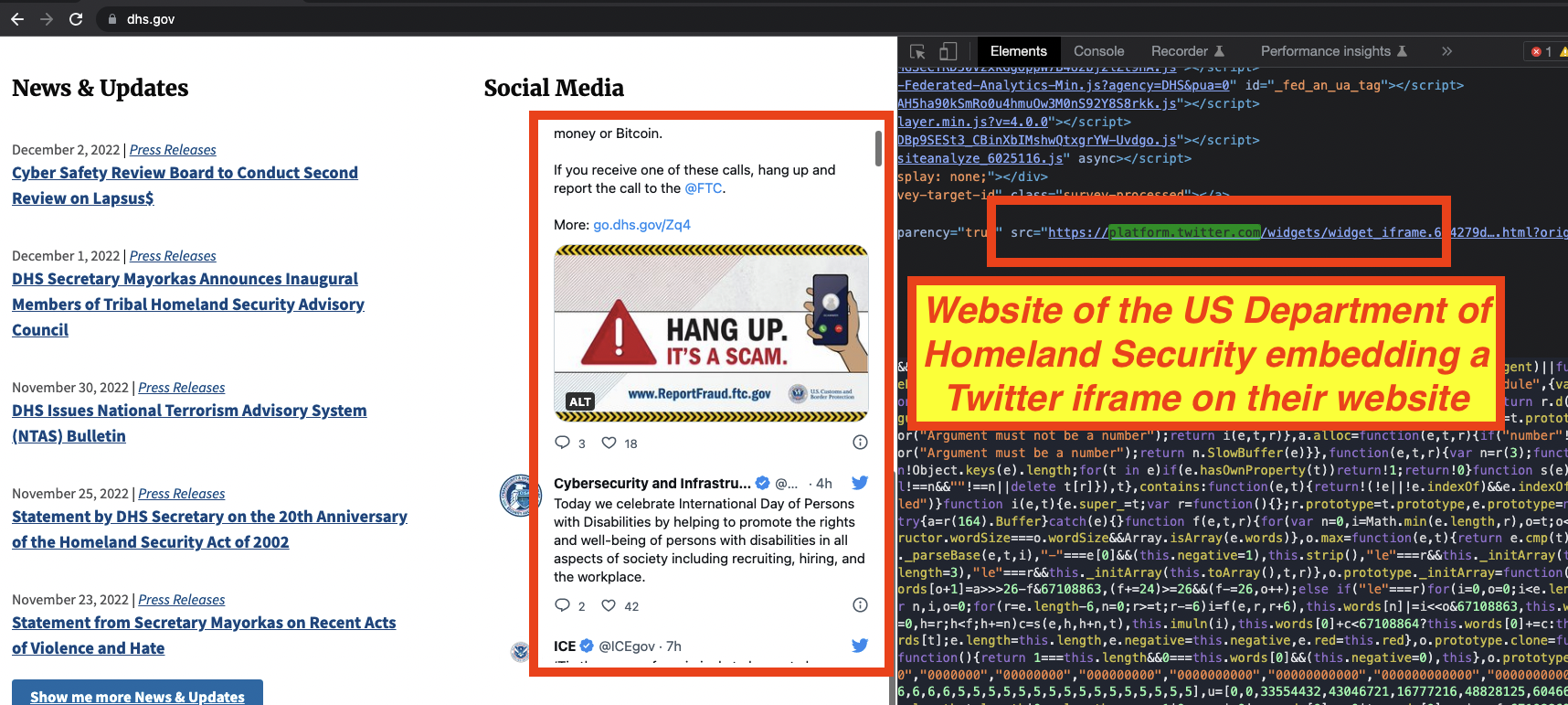
Furthermore, many highly sensitive websites, such as goarmy.com, FBI.gov, and the website of the US Department of Homeland Security (dhs.gov), are hosting 3rd party Javascript code from Twitter on their websites without configuring content security policies or subresource integrity (SRI) hashes. This lack of security precautions could result in supply chain and code injection attacks on government properties if Twitter was ever compromised. British Airways and Ticketmaster both lost tens of thousands of consumers’ personal data after being breached through Javascript exploits, according to research by cybersecurity firm RiskIQ and BBC (respectively).
Do you want the full list of websites hosting Twitter's Pixel? Reach out to @kfranasz or the Contact page.
Background
This section provides context for the study, including Twitter’s history of data breaches, regulatory fines by the Federal Trade Commission (FTC), and various cybersecurity concerns. The section will also explain the Twitter advertising pixel and Twitter widget plug-ins.
 Screenshot of the Department of Homeland Security website (dhs.gov), showing the Twitter syndication social plugin.
Screenshot of the Department of Homeland Security website (dhs.gov), showing the Twitter syndication social plugin.Twitter’s data breaches and cybersecurity concerns
Marketers, publishers, and government decision makers may wonder whether they can trust Twitter’s security posture sufficiently to add Twitter’s 3rd party code to their own websites.
Even before a large portion of Twitter’s cybersecurity and regulatory teams were allegedly fired or quit, public reporting has detailed numerous Twitter data breaches over the years.
Michael X. Heiligenstein, the founder of Firewall Times, wrote an excellent article enumerating the various data breaches Twitter suffered from 2009 through 2022.
In January 2009, a hacker “used an automated password-guessing tool to access the Twitter administrative control panel” and hijacked 33 high-profile user accounts, including then-President-elect Barack Obama, offering his followers an opportunity to win $500 in free gasoline.
In April 2009, another hacker guessed “a Twitter administrative password after gaining access to an employee’s personal email account”, and changed at least one Twitter account password.
In February 2013, Twitter announced a “security incident that potentially impacted around 250,000 users”.
In May 2018, Twitter advised every user to change their password after the company discovered a bug that left 330 million passwords exposed.
In October 2019, it was found that Twitter “incorporated phone numbers and email addresses provided for two-factor authentication into its ad systems, namely its Tailored Audiences and Partner Audiences.”
In November 2019, two former Twitter employees were charged with spying for Saudi Arabia. The spies gained unauthorized access to private and sensitive account details.
In July 2020, a hacker took over the Twitter accounts of approximately 130 high-profile individuals, including Elon Musk, Bill Gates, Barack Obama, and Kanye West. This was done as a part of a bitcoin scam, and the hackers were able to obtain over $100,000 in transfers as a result of this incident.
In July 2022, a hacker obtained personal data on 5.4 million Twitter users, including email addresses and phone numbers.
 News being shared about the 2022 Twitter data breach. Source: BleepingComputer
News being shared about the 2022 Twitter data breach. Source: BleepingComputerIn August 2022, a federal jury in California found a “former Twitter employee guilty for acting as an unregistered agent of the Saudi government. The jury found that Ahmad Abouammo had used his position at Twitter to investigate Saudi dissidents and convey information on them to Bader al-Asaker, an aide to Saudi Crown Prince Mohammed bin Salman.” In Sept 2022, Reuters reported that the FBI informed Twitter that at least one Chinese government espionage agent was working at Twitter. Twitter’s former head of security testified that some “Twitter employees were concerned the Chinese government would be able to collect data on the company's users.”
Twitter’s former head of security also alleged in a complaint filed with the FTC, that Twitter’s cybersecurity practices had “egregious deficiencies, negligence, willful ignorance, and threats to national security.” Twitter disputed the former executive’s claims.
Federal Trade Commission fines against Twitter
In 2011, the Federal Trade Commission (FTC) accepted a settlement with Twitter for a “failure to safeguard personal information.” Part of the FTC settlement included an order that “explicitly prohibited [Twitter] from misrepresenting its privacy and security practices.”
In 2022, the FTC fined Twitter $150 million “for allegedly breaking its privacy promises – again.”. Regulators alleged that Twitter collected customers’ personal information for the stated purpose of security and then exploited it commercially.
Twitter Pixel
Twitter, like many digital advertising platforms, offers a “free” Javascript tag to advertisers–also known as a ‘pixel’. Advertisers can embed this code on their own websites and use it to track, analyze, and target Twitter users with their ads. One common use case for the Twitter Pixel is to track “actions people take after viewing or engaging with” a brand’s ads on Twitter.
Advertising pixels have been implicated in numerous consumer privacy violations. An investigation by The Markup in early June found that “33 of the top 100 hospitals in the United States use the Meta Pixel on their websites. At seven hospitals, it was installed on password-protected patient portals. The investigation found that the tool was sending information about patient health conditions, doctor appointments, and medication allergies to Facebook.” Experts interviewed by The Markup said, “hospitals’ use of an ad tracking tool may violate a federal law protecting health information.”
Another investigation found that the Meta Pixel was embedded on the website of “the Free Application for Federal Student Aid, or FAFSA, [and] was automatically sending the data to Facebook. The data was being collected even if the visitor to the site did not have a Facebook account and began even before the user logged in to studentaid.gov, the site that hosts the form.” In a letter to the US Secretary of Education, two members of Congress described the sharing of students’ financial data with Facebook as an “unprecedented breach, seemingly perpetrated by the Department.”
While one might assume that every advertiser on Twitter platform also uses the Twitter pixel on their own websites, this is not the case. Some brands have made the decision not to use the third party Twitter Pixel on their page. One prominent example is Apple; apple.com and various other Apple owned properties like shazam.com and beatsbydre.com were not observed loading any code from Twitter. This is despite a recent report that found that Apple continues to be a major spender on Twitter’s ad platform.
Elon Musk’s other major companies such as SpaceX and Tesla also do not appear to host the Twitter Pixel or any Twitter code on their websites. This is despite the fact that SpaceX ordered one of the larger advertising packages available on Twitter around November 14th, 2022. According to internal documents viewed by CNBC, “SpaceX has spent more than $160,000 on the Twitter ad campaign for Starlink in Australia and Spain so far.” Neither spacex.com nor starlink.com appear to host the Twitter Pixel on their websites, including when viewed from a Spanish or Australian IP address.
The Twitter Pixel can be observed as either the Online Conversion Tracking Tag (oct.js) or the Universal Conversion Tracking tag (uwt.js). These Javascript tags will serve on a brand’s website from endpoints such as `https://static.ads-twitter.com/oct.js` or `https://static.ads-twitter.com/uwt.js`. Twitter’s Pixel documentation also says that advertisers should also allow the subdomain `analytics.twitter.com` to run code on their websites.
The Twitter Universal Conversion Tracking (uwt.js) is a ~15.7 KB Javascript file which can collect various meta-data about a user’s browser, device, and IP address. The Online Conversion Tracking Tag (oct.js) is a 56 KB Javascript tag that similarly collects various telemetry about a consumer and page view session.
According to Twitter’s video documentation, when the Twitter tag uwt.js tag is invoked, approximately three network requests are made from a browser to Twitter's servers. “Both the t.co and analytics.twitter.com calls are necessary for a functioning tag fire.”
When the Twitter Pixel is invoked, it utilizes a persistent cookie, such as one called the Twitter personalization_id, which “tracks activities on and off Twitter for a personalized experience”. The cookie persists on a consumer’s phone or computer for up to 13 months. It appears that this cookie can be set on a consumer's browser, even if said user does not have a Twitter account or is not logged into Twitter.
Restricted Data Usage (RDU)
Twitter’s Pixel has a Restricted Data Use (“RDU”) feature, which “enables an advertiser to limit Twitter’s use of individual-level conversion events for specific business purposes only on that advertiser’s behalf.”
To enable RDU, an advertiser must send Twitter a parameter to indicate the advertiser would like Twitter to limit its use of conversion data received for an individual conversion event. When enabled, Twitter will limit the use of personal data received in connection with the restricted conversion event to certain business purposes on behalf of the advertiser, such as measurement.
 Screenshot of Chrome Developer Tools’ Network tab on zendesk.com. The screenshot shows an HTTPS network request to Twitter’s measurement endpoint, with the query string parameter for restricted_data_use set to “restrict_optimization”.
Screenshot of Chrome Developer Tools’ Network tab on zendesk.com. The screenshot shows an HTTPS network request to Twitter’s measurement endpoint, with the query string parameter for restricted_data_use set to “restrict_optimization”.Twitter’s documentation states that advertisers may wish to enable RDU “more broadly based on user location in regions where certain laws apply”. This is likely a reference to laws such as the European Union’s GDPR or Brazil’s LGPD.
Google Analytics, another widely used conversion tracking tool, has a feature called “IP address anonymization”, which marketers and web developers can use to instruct Google to avoid storing a consumer’s full IP address to a database. Previous research by Adalytics found that approximately 86% of websites, including many in Europe, were not using the anonymize IP feature.
Twitter Syndication & Tweet embeds
Twitter offers website developers the option of embedding select Tweets on their pages. This allows for an interactive viewing experience. Many websites, including government websites, embed Tweets via Twitter’s own Javascript code on their pages.
Previous research by Adalytics found that approximately 294 different US Congressmen and Senators embed Twitter Javascript code on their taxpayer funded house.gov and senate.gov websites. Why does this matter?
Embedding social-plugins, such as Tweets or Facebook “like” buttons, can result in a website sharing data about its visitors with third parties like Twitter or Facebook (respectively), thereby learning about a visitor’s interests and browsing history. In 2018, a Belgian court ruled that Facebook broke privacy laws by using social plug-ins across the internet to track users. A Belgian privacy watchdog stated that, “Facebook uses various technologies, such as the famous ‘cookies’ or the ‘social plug-ins’ (for example, the ‘Like’ or ‘Share’ buttons) or the ‘pixels’ that are invisible to the naked eye. It uses them on its website but also and especially on the websites of third parties. Thus, the survey reveals that even if you have never entered the Facebook domain, Facebook is still able to follow your browsing behavior without you knowing it, let alone, without you wanting it, thanks to these invisible pixels that Facebook has placed on more than 10,000 other sites.”
Twitter’s own developer documentation states that when consumers (including potentially people who have never registered for or used Twitter’s platform themselves) view “content such as embedded Tweets, buttons, or timelines integrated into other websites using Twitter for Websites, Twitter may receive information, including the web page you visited, your IP address, browser type, operating system, and cookie information.”
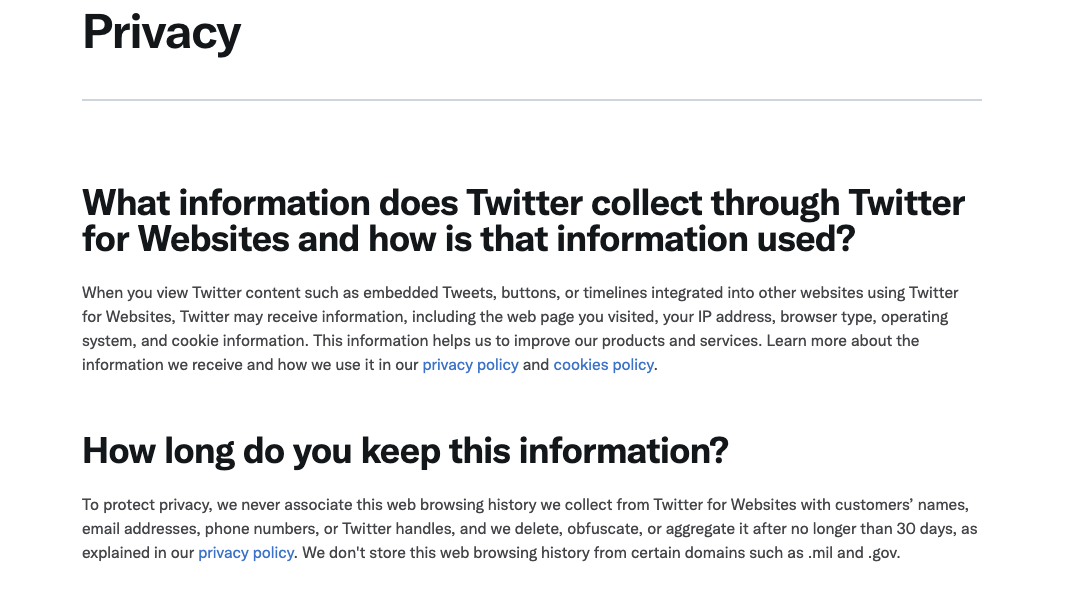 Source: Twitter developer documentation Privacy Page
Source: Twitter developer documentation Privacy Page
It is important to note that Twitter’s documentation states that the company does not “store this web browsing history from certain domains such as .mil and .gov.” However, it is unclear whether that data could be monitored in real-time without storing it to disk or whether or not the claims of non-storage have been independently audited.
Some website owners, cognizant of the fact that hosting 3rd party content widgets results in web traffic data about consumers being shared with those 3rd parties, have elected to allow consumers to decide for themselves whether or not they want the widgets to load. For example, the technology website the-decoder.com replaces Twitter social media widgets with a message that says:
“External media content (Twitter) has been blocked here. When loading or playing, connections are established to the servers of the respective providers. Personal data may be communicated to the providers in the process. You can find more information in our privacy policy.” Consumers can then choose whether or not to “allow external media content.”
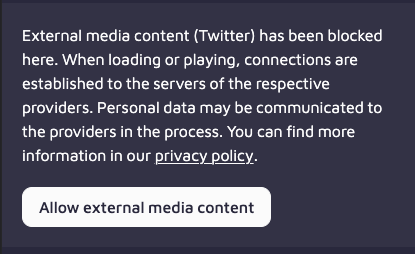 Source: the-decoder.com
Source: the-decoder.comThus, in addition to analyzing which websites were hosting the Twitter ads conversion tracking tools, Adalytics also analyzed which websites are potentially sharing data with Twitter via social media plugins and Tweet widgets. This was done by looking for the presence of HTTPS requests to various Twitter owned sub-domains, such as "platform.twitter.com”.
Results
Websites hosting the Twitter Pixel as Q4 2022
Adalytics collected data from various headless chrome crawls spanning hundreds of thousands of public websites. Adalytics analyzed which of those websites appeared to invoke the Twitter Universal Conversion Tracking tag (https://static.ads-twitter.com/uwt.js), the Twitter Online Conversion Tracking Tag (https://static.ads-twitter.com/oct.js), or send HTTPS requests to analytics.twitter.com. This data was assembled from several sources, including publisher intelligence firm DeepSee.io, URLScan.io, Common Crawl, and others. 70,772 websites were found to make HTTPS requests to static.ads-twitter.com. These included many government, media, non-profit, university, and brand websites.
Somewhat surprisingly, Elon Musk’s other major companies - Tesla and SpaceX - were not observed using the Twitter Pixel on their pages. This is despite SpaceX recently ordering one of the larger advertising packages available on Twitter around November 14th, 2022.
Government websites with Twitter ads pixel
Amongst government entities, the following websites were observed sending data to static.ads-twitter.com:
- studentaid.gov - the Department of Education’s Free Application for Federal Student Aid or FAFSA. The MarkUp previously published research on how studentaid.gov was sharing data with Facebook. Citing the investigation, two Republican lawmakers from North Carolina, Sen. Richard Burr and Rep. Virginia Foxx, said in a letter sent to Secretary of Education Miguel Cardona that it was “completely inappropriate” for aid applicants to be tracked by Facebook through “predatory data collection.” The lawmakers wrote: “This unprecedented breach, seemingly perpetrated by the Department, will likely increase the discomfort already felt by many parents who are asked to provide sensitive financial information to the Department.”
- website of the Indiana state government
- Republican Congressman Kevin McCarthy’s website (republicanleader.gov),
- Bay Area Rapid Transit (BART)
- the US Selective Service Systems (sss.gov)
- Various Saudi Arabian government websites, including modon.gov.sa, data.gov.sa, vision2030.gov.sa, greeninitiatives.gov.sa
- Various United Arab Emirate government websites, including gpssa.gov.ae, gpssa.gov.ae, home.moi.gov.ae
- Australian Government Department of Foreign Affairs (smartraveller.gov.au)
- New York State Donate Life Registry (register-donatelife.ny.gov). This website asks users to fill out personal information, including part of their Social Security Number
- Australian defense sector jobs (defencejobs.gov.au)
- US Department of Health & Human Services (telehealth.hhs.gov)
- Maryland Department of Health (covidlink.maryland.gov)
Academic & university websites with Twitter ads pixel
Among academia, the websites of the University of Washington, Johns Hopkins University, Purdue University, University of California, City University of New York (CUNY) and were observed sharing data with the Twitter Pixel.
Non-profit websites with Twitter ads pixel
Amongst non-profit entities, the following websites were observed sending data to static.ads-twitter.com:
- United Nations Programme on HIV/AIDS (unaids.org)
- cookielaw.org (CookieLaw by CookiePro)
- Alzheimer’s Association (alz.org)
- American Academy of Family Physicians (aafp.org)
- US Conference of Catholic Bishops (usccb.org)
- Project Management Institute (pmi.org)
- Doctors Without Borders (doctorswithoutborders.org)
Healthcare websites with Twitter ads pixel
Amongst healthcare entities, the following websites were observed sending data to static.ads-twitter.com:
- webmd.com
- British Medical Journal (bmj.com)
- United Health Group (unitedhealthgroup.com)
- healthywomen.org
- EmblemHealth (emblemhealth.com)
- Women’s Preventive Services Initiative (womenspreventivehealth.org)
- Stamford Hospital Foundation (stamfordhospitalfoundation.org)
- health.org.uk
- Holy Cross Health (holycrosshealth.org)
Major media publishers with Twitter ads pixel
Several major media publishers were observed using the Twitter ads pixel on various parts of their websites, including:
Fortune 500 brands websites with Twitter ads pixel
Many prominent companies and Fortune 500 brands were observed still utilizing the Twitter Pixel on their websites (including many who have allegedly paused their spend on the platform). Somewhat surprisingly, this list includes many automobile major manufacturers.
The New York Times reported on Dec. 2nd that "automakers are among the most concerned advertisers, with General Motors raising questions about whether Twitter’s data would be shared with Mr. Musk’s car company, Tesla, three people said." “It’s important for us to ensure our advertising strategies and data can be safely managed by a platform owned by a competitor,” a G.M. spokesman said in a statement.
The list of major brands whose websites were observed sharing data with Twitter about consumers via the Twitter Pixel included:
- Audi USA
- General Motors (cadillac.com, chevrolet.com.mx, and other websites)
- General Mills (bluebuffalo.com)
- Volkswagen (vw.com)
- Mondelez (oreo.com)
- Chrysler (jeep.com)
- Ford
- Dentsu media agency
- Pfizer
- Chipotle
- Pfizer
- Spotify
- Amazon-owned zappos.com
- Disney (disneyplus.com)
- Coca-cola (Sprite website - https://www.sprite.com/)
- PNC
- Citigroup
- Cisco
- Mazda
- Kohl's
- Hyundai
- Wingstop
Major European websites which send data via Twitter Pixel
Some readers in Europe may be interested to consider the EU’s GDPR law in relation to the Twitter Pixel. To this end, a separate analysis was conducted from European IP addresses in Germany and other EU countries. It appears that several major European websites continue to invoke the Twitter Pixel when a EU IP address visitor browses their pages.
These include websites such as:
- McKinsey’s German website (mckinsey.de) - only observed invoking the Twitter Pixel after the user has given consent via cookie banner
- Shopify (shopify.com). Shopify’s website was observed sending data to Twitter via the Twitter Pixel from the German, French, Italian, Danish, Norwegian, and Spanish users’ browsers
- thelocal.fr - observed beaconing data to Twitter from a French user’s browser before the French user had an opportunity to give any consent
- Noroff School of Technology & Digital Media (noroff.no) - observed beaconing data to Twitter from a Norwegian user’s browser before the Norwegian user had an opportunity to give any consent
- Astegiudiziarie.it - observed beaconing data to Twitter from an Italian user’s browser before the Italian user had an opportunity to give any consent
Major brands who advertise on Twitter but do not use the Twitter Pixel
There were at least two notable instances where a major brand advertised on Twitter, but was not observed using the Twitter Pixel or any Twitter code on their own websites.
The first prominent example is Apple - apple.com and various other Apple owned properties like shazam.com and beatsbydre.com were not observed loading any code from Twitter. This is despite a recent report that found that Apple continues to be a major spender on Twitter’s ad platform.
 Screenshot of an Apple advertisement on the Twitter web app
Screenshot of an Apple advertisement on the Twitter web appElon Musk’s other major companies - SpaceX and Tesla - also do not appear to host the Twitter Pixel or any Twitter code on their websites. This is despite the fact that SpaceX ordered one of the larger advertising packages available on Twitter around November 14th, 2022. According to internal documents viewed by CNBC, “SpaceX has spent more than $160,000 on the Twitter ad campaign for Starlink in Australia and Spain so far.” Neither spacex.com nor starlink.com appear to host the Twitter Pixel on their websites (including when viewed from a Spanish or Australian IP address).
Which websites have enabled the Twitter Pixel’s “Restricted Data Usage” feature?
As mentioned earlier, Twitter’s Pixel has a Restricted Data Use (“RDU”) feature, which “enables an advertiser to limit Twitter’s use of individual-level conversion events for specific business purposes only on that advertiser’s behalf.”
To enable RDU, an advertiser must send Twitter a parameter to indicate the advertiser would like Twitter to limit its use of conversion data received for an individual conversion event. When enabled, Twitter will limit the use of personal data received in connection with the restricted conversion event to certain business purposes on behalf of the advertiser, such as measurement.
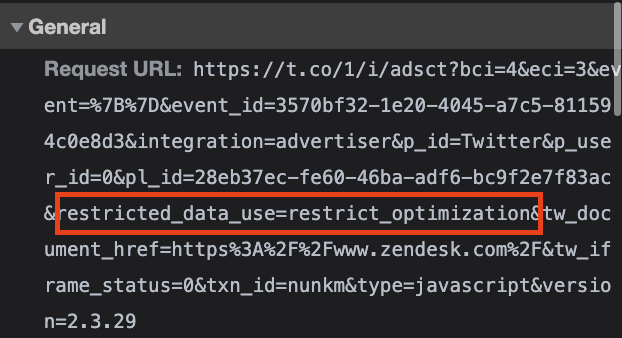
Throughout the course of this study, only two websites were observed utilizing the “restricted_data_use” query string parameter in HTTPS request to Twitter Pixel endpoints. These two websites were zendesk.com and chase.com.
For ZenDesk, the RDU query string parameter was configured to “restrict_optimization,” while for JPMorgan Chase’s website, the RDU query string parameter was set to “off.” The RDU documentation on Twitter’s website states: ‘this parameter, if not set, will be set to “off” by default. If the advertiser turns it on by setting the value of this parameter to “restrict_optimization”.’
The vast majority of websites analyzed in this study did not appear to use the Restricted Data Use feature.
What types of consumer data are websites sharing via the Twitter Pixel?
In addition to collecting cookie IDs, IP addresses, user agent, and website data, some users of the Twitter Pixel were observed sharing additional data with Twitter.
For example, on the following eight websites, HTTPS requests to analytics.twitter.com included a query string parameter called “email_address.” The source code of these websites suggests that this parameter shares with Twitter a given consumer’s hashed email address.
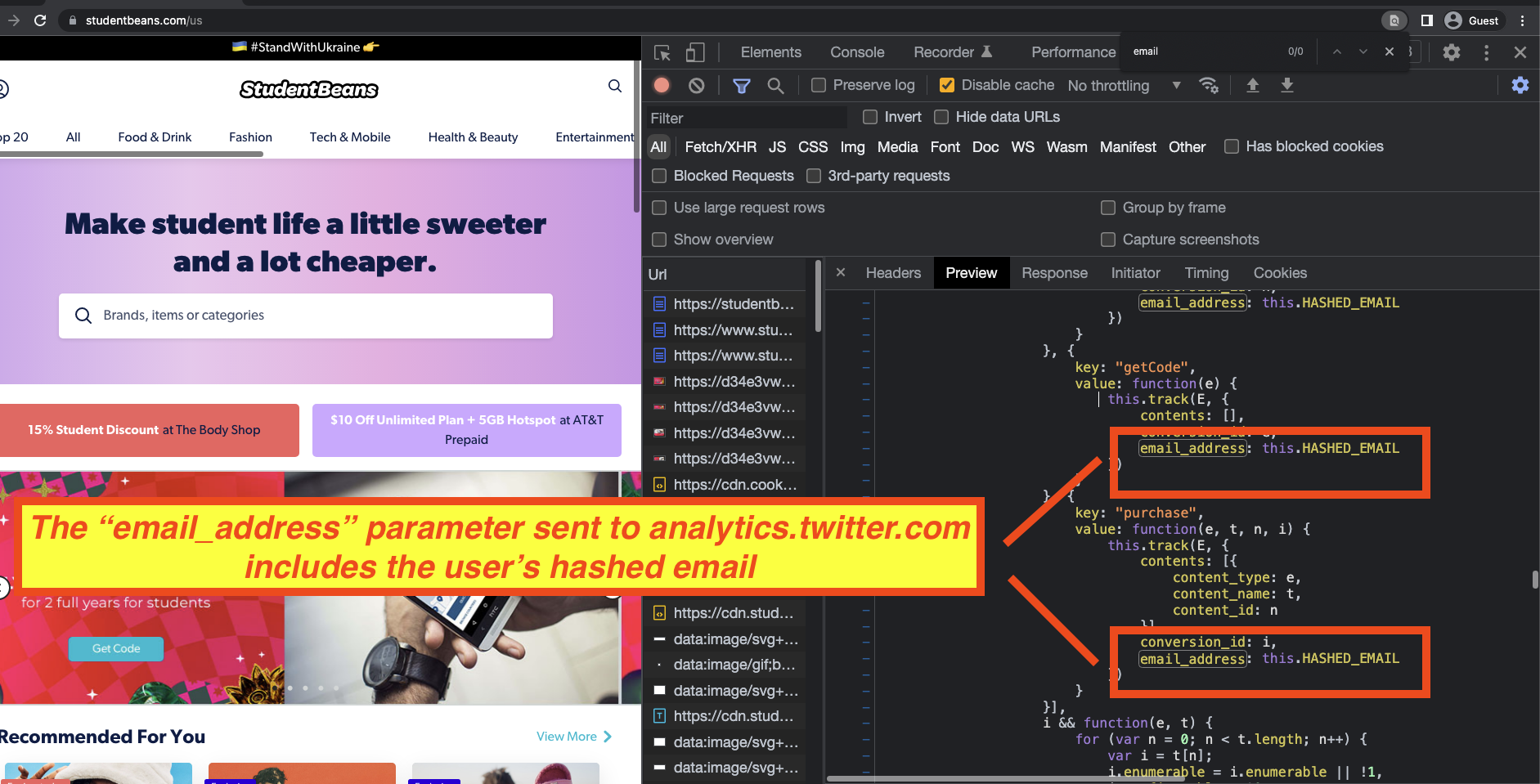
These eight websites included:
- cupshe.com
- cgtrader.com
- studentbeans.com
- xcite.com
- fisher-price.com
- tokopedia.com
- wandb.ai
- americangirl.com
On the website xcite.com, requests to analytics.twitter.com were observed containing the query string parameter “phone_number,” which appears to include the given consumer’s hashed phone number.
In addition to the Twitter Pixel, this study also sought to analyze which websites are using Twitter’s social plug-in to embed Tweets on their own websites.
As mentioned before, embedding social-plugins, such as Tweets or Facebook “like” buttons, can result in a website sharing data about its visitors with third parties like Twitter or Facebook (respectively).
Some website owners, cognizant of the fact that hosting 3rd party content syndication widgets results in web traffic data about consumers being shared with those 3rd parties, have elected to allow consumers to decide for themselves whether or not they want the widgets to load. For example, the technology website the-decoder.com, replaces Twitter syndication embeds with a message that says:
“External media content (Twitter) has been blocked here. When loading or playing, connections are established to the servers of the respective providers. Personal data may be communicated to the providers in the process. You can find more information in our privacy policy.” Consumers can then choose whether or not to “allow external media content.”
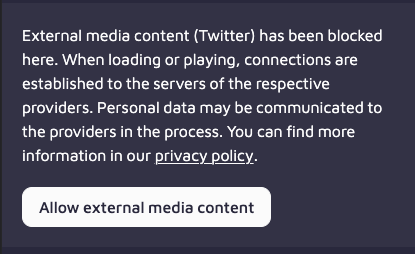 Source: the-decoder.com
Source: the-decoder.comFurthermore, if Twitter was to inadvertently ever suffer a security breach that allowed a rogue actor to modify the Twitter Javascript, an attacker could potentially deface websites which embed that Javascript or exfiltrate data from those websites. British Airways and TicketMaster both lost tens of thousands of consumers’ personal data after reportedly being breached through 3rd party Javascript exploits.
Through the course of this study, 637,998 websites were observed sending HTTPS requests to either `platform.twitter.com` or `syndication.twitter.com’. These included many government agencies, politicians, media publishers, universities, Fortune 500 brands, non-profits, and healthcare websites.
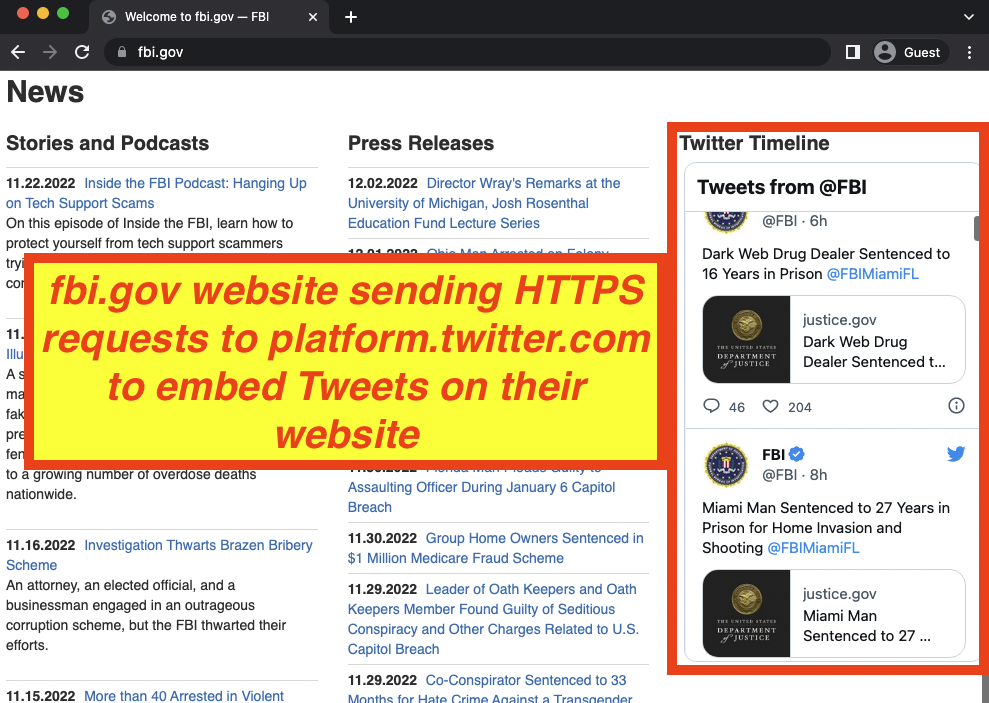
For example, the website of the Federal Bureau of Investigation (fbi.gov), was observed making HTTPS requests to platform.twitter.com to serve a social media widget embed.
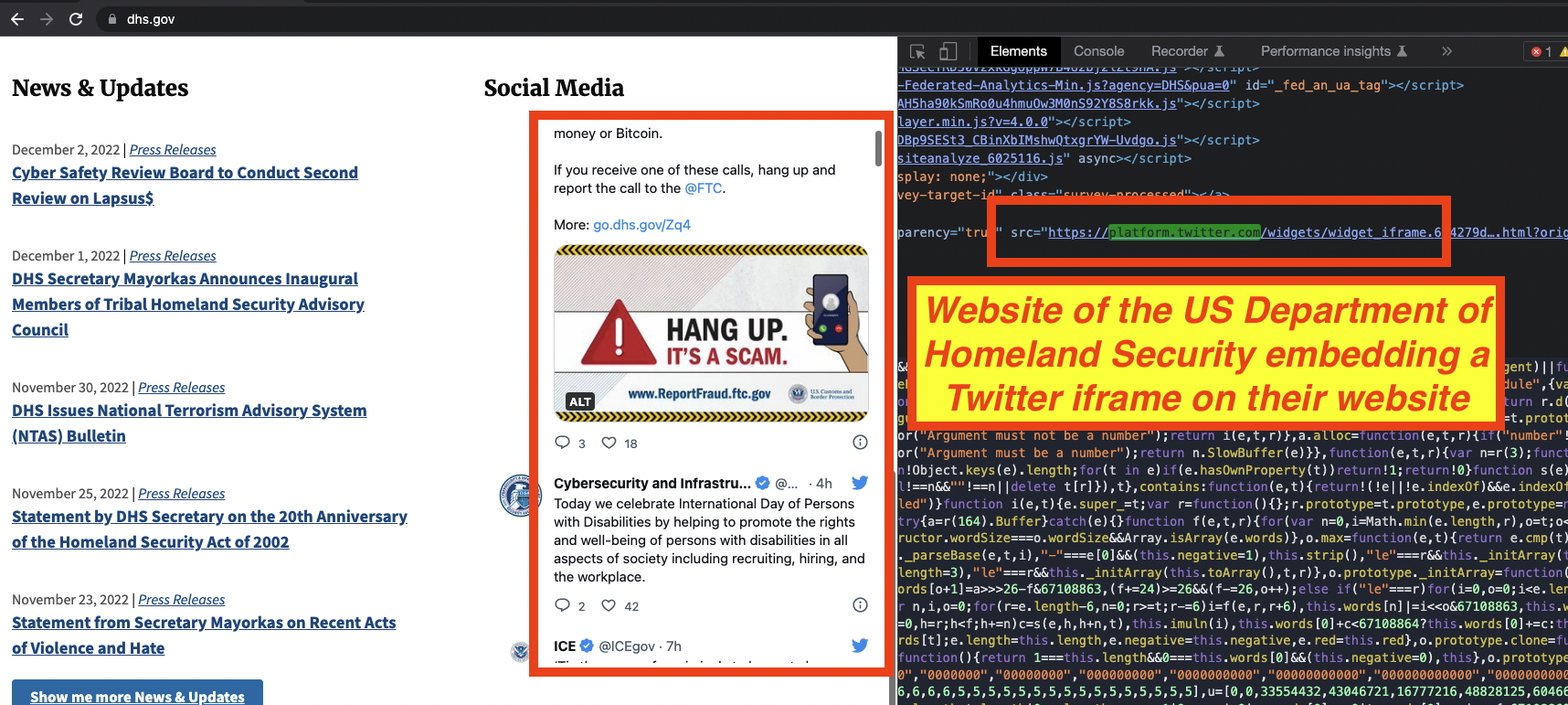
The website of the US Department of Homeland Security (dhs.gov), was also observed loading the Twitter social media plug-in, as an unsandboxed iframe.
The .house.gov and .senate.gov websites of 300 members of Congress and US Senators were observed making HTTPS requests to Twitter.
Do you want the full list of websites hosting Twitter's Pixel? Reach out to @kfranasz or the Contact page.
Conclusion
Caveats & Limitations
Interpreting the results of this observational study requires a lot of nuance and caution. This study should not be construed as a legal commentary or opinion. The study is meant to be viewed as a preliminary observational analysis of publicly available information and empirical data.
This study relied entirely on client-side browser traffic and source code inspection. It is not possible to fully characterize what Twitter does with the data it receives via HTTPS traffic.
Furthermore, many of the websites examined in this study could quickly remove or change the configuration of the Twitter Pixel or the Twitter social media widget on their webpages. Some of the websites analyzed in this study were only analyzed prior to the October 27th, 2022 date when Elon Musk completed his acquisition of Twitter, and not after that date.
This study only sampled a few pages on each website - it did not perform exhaustive crawls or scans, which could lead to false negatives. Furthermore, this study did not examine mobile apps, or how certain websites behave with regards to different user agents.
Discussion
The results of this preliminary study demonstrate that large numbers of websites continue to make HTTPS requests and share data with Twitter, even after the company was taken private by Elon Musk and his various financial backers.
If Twitter stores all of the data it receives from its pixel and embedded Tweets on third party websites, this could constitute a significant archive of consumer web browsing activity. Via these embed Pixels and tags, Twitter is able to gather data about not only its own users, but also about consumers who have never had any direct relationship with the Twitter platform.
It is unclear to what extent various website owners have considered the trade-offs of sharing detailed information about their site visitors with Twitter. For example, both General Motors and Ford continue to host the Twitter Pixel on their websites, despite the fact that Twitter is now owned by the CEO of Tesla, a competing vehicle maker. Neither General Motors nor Ford have configured the Twitter Pixel’s Restricted Data Usage (RDU) feature. This raises the hypothetical possibility that someone at Twitter could see the IP address of every consumer who visits ford.com or various General Motors websites - a potentially valuable market research dataset.
The New York Times reported on Dec. 2nd that "automakers are among the most concerned advertisers, with General Motors raising questions about whether Twitter’s data would be shared with Mr. Musk’s car company, Tesla, three people said." “It’s important for us to ensure our advertising strategies and data can be safely managed by a platform owned by a competitor,” a G.M. spokesman said in a statement. It is unclear whether General Motors or other brands have considered that pixels embedded on their websites may be sharing even more data about the brands' prospective customers than the Twitter ads platform itself.
Adalytics shared the results of this research report with Bob Hoffman, a prominent thought leader in the advertising industry. Mr. Hoffman commented to Adalytics:
"The results of this research are very disturbing [...] the idea that Ford and General Motors would allow Twitter to place tracking pixels on their websites is an indication of the cluelessness and carelessness of corporate America about the ramifications of adtech and online tracking. How responsible companies can voluntarily allow the CEO of one of their biggest competitors to monitor the activities of their customers is beyond comprehension."
Neither Apple, a company that is well known for its reluctance to share consumer data with other parties, nor Tesla and SpaceX, were observed using the Twitter Pixel on their websites. This is despite the fact that both Apple and SpaceX are currently large spenders on Twitter’s advertising platform.
Many government, defense, and journalism related websites were observed sharing data with Twitter. It is not clear what the risks this archive of web browsing data presents, or how this data could change hands in the future. Twitter has been known to have suffered at least four data breaches in the past.
Furthermore, several websites were observed sharing data with Twitter about European visitors before they had any chance to give or decline consent. It is unclear whether this practice is in violation of the GDPR.
Many sensitive websites, such as those of FBI and the US Department of Homeland Security, were observed embedding Twitter code on their pages without enabling security features such as iframe sandbox, Subresource Integrity (SRI) hashes, or content security policy (CSP) headers. If Twitter itself were to ever suffer a breach, a foreign threat actor could leverage their control over Twitter’s code to deface or hack these sensitive government websites. British Airways and TicketMaster both lost tens of thousands of consumers’ personal data after potentially being breached through code injection Javascript exploits. It took hackers just 22 lines of Javascript code to steal British Airways’ customer data.
Virtually all (>99%) of websites examined in this study that had the Twitter advertising pixel were not using the Restricted Data Usage (RDU) feature. It is unclear what Twitter can do with the large amounts of data it has gathered about consumers from site visitors via these Pixels. Currently, there does not appear to be any legislation, laws, or legal mechanisms in the US that would allow organizational entities to direct Twitter to delete large amounts of log data. For example, it is unclear whether Ford or General Motors can direct Twitter to delete all IP addresses of consumers who visited their websites.
Policymakers in Congress may wish to consider legislation that would govern what happens in the event that a data processor or data broker changes ownership as part of a Merger or Acquisition event. For example, if an American data broker with data about millions of Americans is acquired by a foreign investor with ties to a foreign nation-state, should the data broker be required to delete all data it has about American citizens prior to executing the change in ownership?
Take-away Points
- Twitter has amassed a large archive of web browsing data, including from consumers who have never used Twitter themselves
- Tens of thousands of websites are still sharing data about consumers with Twitter, some without asking for user consent
- The vast majority of these websites have not restricted Twitter’s usage of that data
